-
Notifications
You must be signed in to change notification settings - Fork 392
Reverse proxy header authentication
CloudBeaver offers a feature for authorization and authentication using reverse proxy headers. This method allows to authenticate users via specific HTTP header fields.
-
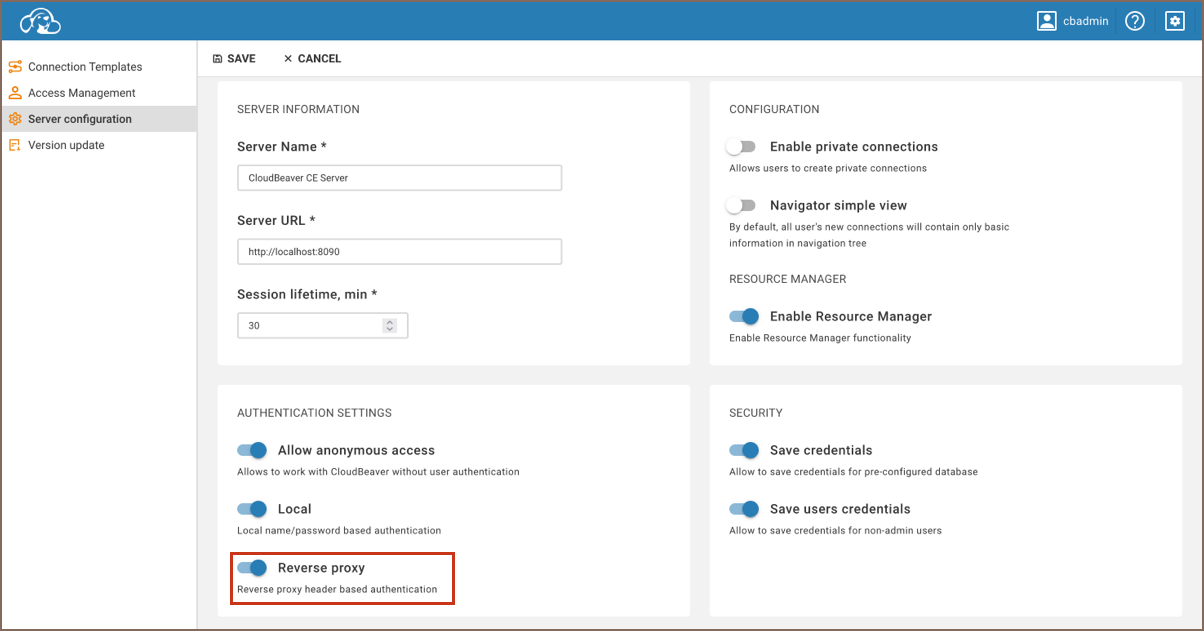
As an administrator, navigate to the Settings -> Server configuration.
-
Locate the Reverse proxy option and activate this setting to allow reverse proxy authentication.
-
Save changes.
To configure reverse proxy authentication, follow these steps:
- Open your
.cloudbeaver.runtime.confconfiguration file. - Locate the
appsection within the file. - Add a new entry to the
authConfigurationsarray with the following structure:
"app": {
...
"authConfigurations": [
{
"id": "your_proxy_id",
"provider": "reverseProxy",
"displayName": "your_proxy_username",
"disabled": true,
"iconURL": "",
"description": "",
"parameters": {
"logout-url": "https://link_if_needed",
"user-header": "",
"team-header": "",
"team-delimiter": "",
"first-name-header": "",
"last-name-header": ""
}
}
]
}
Important: Ensure you include the mandatory fields id, provider, and displayName. The
providername must be set toreverseProxy.
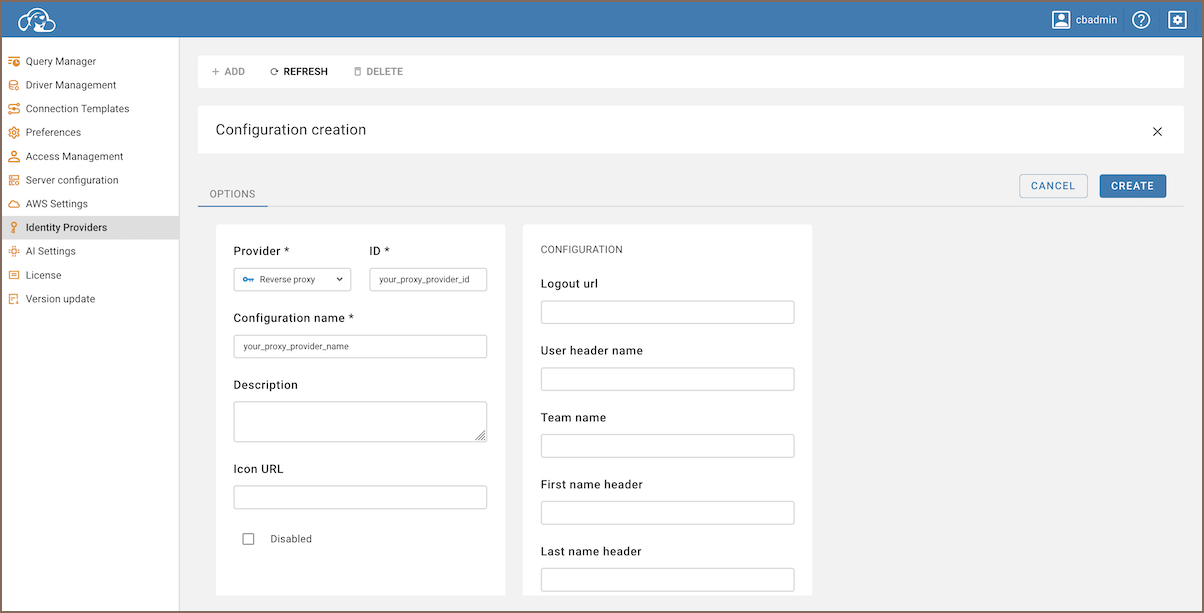
To configure reverse proxy authentication in the CloudBeaver using the graphical user interface (GUI), follow these steps:
- Log in as an administrator.
- Navigate to Settings -> Server configuration in the CloudBeaver interface.
- Click on the + Add button to create a new authentication provider.
- In the Provider dropdown menu, select Reverse Proxy.
- Enter a unique identifier in the ID field and a name for the configuration in the Configuration name field.
- Click on Save to apply the changes.
Configure the standard HTTP header fields as follows:
| Header | Description |
|---|---|
X-User |
user login |
X-Team |
user teams |
X-First-name |
user profile firstname |
X-Last-name |
user profile lastname |
X-Full-name |
user profile fullname |
X-Role |
user roles, only for DBeaver Team edition |
Consider a user named newuser, belonging to both user and admin teams. To access an application with reverse proxy
header authentication enabled, the following HTTP headers should be set in the request to the CloudBeaver application:
X-User: newuser
X-Team: user|admin
X-First-name: John
X-Last-name: Smith
Tip: CloudBeaver categorizes users into two default teams:
userandadmin. Default delimiter used to separate teams in the header is|(could be customized inteam-delimiterparameter, all characters are allowed).
- Application overview
- Demo Server
- Administration
- Server configuration
- Create Connection
- Connection Templates Management
- Access Management
-
Authentication methods
-
Local Access Authentication

- Anonymous Access Configuration
- Reverse proxy header authentication
- LDAP
-
Single Sign On

-
SAML

-
OpenID

-
AWS OpenID

-
AWS SAML

-
AWS IAM

-
AWS OpenId via Okta

-
Snowflake SSO

-
Okta OpenId

-
Cognito OpenId

-
JWT authentication

-
Kerberos authentication

-
NTLM

-
Microsoft Entra ID authentication

-
Google authentication

-
Local Access Authentication
- User credentials storage
-
Cloud Explorer

-
Cloud storage

-
Query Manager

-
Drivers Management

- Supported databases
- Accessibility
- Keyboard shortcuts
- Features
- Server configuration
- CloudBeaver and Nginx
-
Domain manager

- Configuring HTTPS for Jetty server
- Product configuration parameters
- Command line parameters
- Local Preferences
- API
-
CloudBeaver Community
-
CloudBeaver AWS
-
CloudBeaver Enterprise
-
Deployment options
-
Development