-
Notifications
You must be signed in to change notification settings - Fork 2
Design
User data
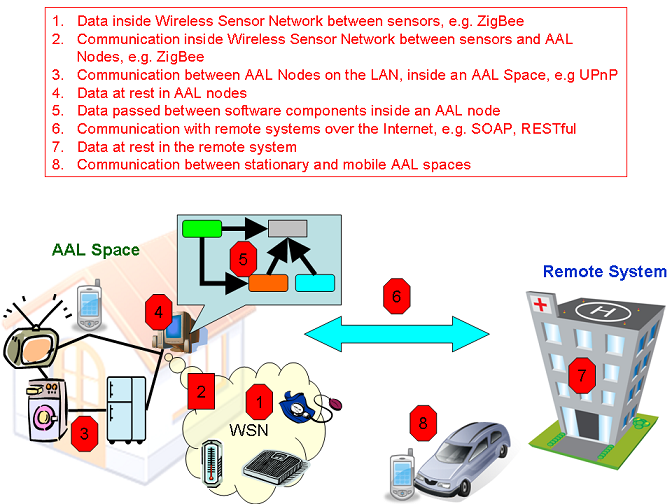
End-users submit all kinds of personal information while using services. This data is stored and processed by the service providers and also exchanged between service providers. The information can range from simple user profiles containing for example a username and an e-mail address to very sensitive data about the health of the assisted person.
Sensor data
A significant part of the information that is submitted to service providers is gathered through all kinds of sensors (e.g. health, position). This data is not sent to the service provider directly by the sensor, but is usually collected and possibly even processed at some kind of gateway first. The raw sensor data that is transferred from the sensor to such a gateway is a sensitive asset itself, before it becomes “user data”, because of the kind of information that is transmitted.
Actuator access
Some services could be linked to actuators placed in the assisted person‟s house or even on the body. The scenarios from OASIS mention actuators that operate lights and household equipment as examples. Unauthorized access to such actuators could cause serious safety issues.
Private communications between end-users
End-users might not only communicate with service providers, but also use the AAL system to have communications directly with each other. Since these communications could be of private nature (i.e. discussing personal information) they are a sensitive asset.
Service membership
The fact that some person is a member of a certain service can already leak sensitive information about that person
| Threats | Actor | Location | Incentives/ Motivation | Description | Probability |
|---|---|---|---|---|---|
| T1 | Family member | uSpace (measurement devices, gateway) | Wants to make use of the devices either for fun or for medical purposes. | Data is not associated with the right patient. | High |
| T2 | Neighbors | PAN/LAN-IF, Gateway | 1) Hacking whizzkids, 2) Hacking devices for fun. | 1) uploading incorrect measurements, taking over control | low |
| T3 | Internet hacker/malware provider | uSpace (gateway) | Hacking devices for fun | Change data. | Low (except if PC). |
| T4 | Internet hacker/malware provider | Remote Server | Fun, Vandalism, Ransom | Corruption and/or deletion of the data. | Medium |
| T5 | Patient | Remote Server | Legal aspects | Claims that the data doesn’t belong to him and sue the service provider for wrong decision | Medium to High |
| T6 | AAL Service Provider | Remote Server | Reimbursement/Turnover | Corrupt data, Misinterpret/misrepresent/selective presentation | Low to medium |
| T7 | IT Staff | Remote Server | Disgruntled employee, Malicious employee | Change data. | Medium |
| T8 | Nurse/ Doctor | Remote Server (EHR) | Unintentional Modification e.g. due to time pressure and bad usability, Intentional harm | Modification of the data (depends on the application, but most likely during the preparation of referral report). | Medium to High |
| T9 | Doctor/Care Management | Remote Server | Competition against other services, Reputation and liability protection, Competition amongst doctors | Misrepresentation of the performance (hiding of the cases), Corruption of the evidence data after the fact | Medium (or High depending on the cases). |
| T10 | Service provider | Remote Server | Reducing cost of the system development | Not well developed, Not following rules and regulations, Miss association of the data. | High |
| T11 | Family member | PAN/LAN-IFs, Gateway | Wants to make use of the devices either for fun or for medical purposes. | Data is not associated with the right patient. | High |
| T12 | End user | uSpace (Home) | unintenctionally introducing virus when end user wants to make use of open port (not controlled by uAAL) on the AAL aware node. | Universaal software can be affected by a virus (e.g. introduced in a usb stick) | High |
| T13 | AAL application developer | Developer Depot | Vandalism | Provide a malicious application that will destroy data, operate on the home appliances with malicious purposes – burn a house, waste electrical power | Medium |
| T14 | A hacker/neighbor/a family member | Inter-node communication on LAN | Vandalism | Plug in a fake AAL node to send fake messages | Medium |
| T16 | A hacker/neighbor/a family member | Playback attack on LAN, Internet | Vandalism | feed wrong data into the uSpace | Medium |
| T17 | A hacker or neighbor | Internet (or WAN-IF) | Vandalism | Interfere with the network flow from the gateway to the Internet and send wrong data on behalf of uSpace to a remote system | High |
| T18 | AAL application developer | Developer Depot | Vandalism | Provide a malicious application that will destroy data, operate on the home appliances with malicious purposes – burn a house, waste electrical power, by overriding parts of universAAL middleware. For example, in OSGi, a ServiceBus OSGi service can be provided by the application, in additional to the ServiceBus OSGi service provided universAAL.org. That additional OSGi service can be given a higher "service.ranking" ranking property, causing it to be selected by the components that use ServiceBus. This way all the context events will be redirected the new malicious ServiceBus that could do operate any universAAL services it wants, overriding any security mechanisms of the ServiceBus provided by universaal.org. | Medium |
| Threats | Actor | Location | Incentives/ Motivation | Description | Probability |
|---|---|---|---|---|---|
| T1 | AAL application developer | Developer Depot | Blackmail/Identity Theft | Provide a malicious application that will steal the data | High |
| T2 | A hacker/neighbor/a family member | WSN: Outside environment near the house, inside the house | Blackmail | Plug a sniffer to sniff the sensor data | Medium |
| T3 | A hacker/neighbor/a family member | Inter-node communication on LAN | Blackmail/Identity Theft | Plug a sniffer to intercept inter-node communication | Medium |
| T4 | A hacker/neighbor/a family member | Inter-node communication on LAN | Blackmail/Identity Theft | Plug in a fake AAL node to intercept inter-node communication | Medium |
| T5 | A family member/guest/ home worker | AAL Node | Blackmail/fun | Login into an AAL Node at home and steal information | Medium |
| T6 | A family member with hacking skills | AAL Node | Blackmail | Copy contents of the disk of AAL node and reverse engineer the contents (e.g. MySQL disk storage) | Low |
| T7 | A hacker | Gateway to outside communication | Blackmail/Identity Theft | Tap the internet cables from the gateway to the Inernet and sniff the passing data | High |
| T8 | A family member/guest/ | AAL Node | Accidental | Hear/see confidential information from one of the output devices at home, during a login session with a legitimate user. For example, a reminder “Take your Prozac” | High |
| T9 | A family member/guest | AAL Node | Blackmail | Copy/lookup information from one of the AAL nodes during the login session of legitimate user | Medium |
| T10 | A hacker | Exporting gateway | Blackmail/Identity Theft | Connect to uSpace through the gateway and steal information | High |
| T11 | A family member, guest/ home worker | AAL Node | Blackmail/Identity Theft | Install a Trojan horse on the AAL Node and steal the information from the disk, network, etc. | High |
| T12 | AAL application developer | Developer Depot | Blackmail/Identity Theft | Provide a malicious application that will steal the data, by overriding parts of universAAL middleware, for example the ContextBus and do anything it wants with the data, overriding any security mechanisms of the ContextBus provided by universaal.org. See the T18 of Integrity threats that explains how this overriding can be done. | High |