-
Notifications
You must be signed in to change notification settings - Fork 3
Commit
This commit does not belong to any branch on this repository, and may belong to a fork outside of the repository.
- Loading branch information
1 parent
8a965fc
commit 1d4d31a
Showing
4 changed files
with
107 additions
and
133 deletions.
There are no files selected for viewing
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -1,66 +1,37 @@ | ||
| --- | ||
| sidebar_position: 6 | ||
| title: Adding Notification and SOAR Endpoints | ||
| description: Adding notification endpoints to Logz.io's SIEM solution | ||
| image: https://dytvr9ot2sszz.cloudfront.net/logz-docs/social-assets/docs-social.jpg | ||
| keywords: [SIEM, Security, Event Management, Endpoints, Notifications, SOAR] | ||
| --- | ||
|
|
||
| A notification endpoint defines where a notification of a rule execution needs to be sent to. Logz.io has a number of pre-configured endpoints, such as Slack or Opsgenie. Otherwise you can easily add any notification endpoint using the **Custom** feature. The latter option is currently used to integrate with SOARs. | ||
| A notification endpoint specifies where to send a notification for a rule execution. Logz.io offers several pre-configured endpoints, and you can easily add custom notification points using the **Custom** feature. Custom notification points are integrated with SOARs (security orchestration, automation, and response). | ||
|
|
||
| ### Add a pre-configured notification endpoint | ||
| :::info note | ||
| You must be an account admin to add a notification endpoint. | ||
| ::: | ||
|
|
||
| To add a pre-configured notification endpoint: | ||
| ## Pre-configured notification endpoint | ||
|
|
||
| 1. Sign in to Logz.io as an administrator user. | ||
|
|
||
| 2. Go to **Settings > Notification endpoints**. | ||
| Navigate to your Logz.io [SIEM account > Settings > Notification endpoints](https://app.logz.io/#/dashboard/alerts/endpoints). | ||
|
|
||
|  | ||
| Select **+ Add endpoint** to open the configuration wizard. Select the **type** of your endpoint, name it, and add a description. Add the required connection data, e.g., API key or Instance URL. You can test your endpoint by clicking **Run the test** or click **Add a new endpoint** to save it. | ||
|
|
||
| 3. Select **+ Add endpoint**. | ||
|  | ||
|
|
||
|  | ||
| ## Custom notification endpoint | ||
|
|
||
| Navigate to your Logz.io [SIEM account > Settings > Notification endpoints](https://app.logz.io/#/dashboard/alerts/endpoints). | ||
|
|
||
| 3. Select your endpoint source from the **Type** menu. | ||
| Select **+ Add endpoint** to open the configuration wizard, and choose the **Custom** option from the dropdown menu. Next: | ||
|
|
||
|  | ||
| * Name your endpoint | ||
| * Add the webhook URL | ||
| * Select the required method | ||
| * Add the webhook header | ||
|
|
||
| You can test your endpoint by clicking **Run the test** or click **Add a new endpoint** to save it. | ||
|
|
||
| * Add a name for this endpoint. | ||
|
|
||
| * If required, add a description for the endpoint. | ||
|
|
||
| * Add the required connection data, e.g. API key or Instance URL. | ||
|
|
||
| * If you want to test the connection, select **Run the test**. | ||
|
|
||
| 4. Select **Add endpoint**. | ||
|
|
||
| ### Add a custom notification endpoint | ||
|
|
||
| To add a custom notification endpoint: | ||
|
|
||
|
|
||
| 1. Sign in to Logz.io as an administrator user. | ||
|
|
||
| 2. Go to **Settings > Notification endpoints**. | ||
|
|
||
|  | ||
|
|
||
|
|
||
| 3. Select **Custom** from the **Type** menu. | ||
|
|
||
|  | ||
|
|
||
| * Add a name for this endpoint. | ||
|
|
||
| * If required, add a description for the endpoint. | ||
|
|
||
| * Add the webhook URL. | ||
|
|
||
| * Select the required method. | ||
|
|
||
| * Select the webhook header. | ||
|
|
||
| * If you want to test the connection, select **Run the test**. | ||
|
|
||
| 4. Select **Add endpoint**. | ||
|  |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -1,52 +1,58 @@ | ||
| --- | ||
| sidebar_position: 8 | ||
| title: Edit Rules and Protected Rules | ||
| title: Manage Security Rules | ||
| image: https://dytvr9ot2sszz.cloudfront.net/logz-docs/social-assets/docs-social.jpg | ||
| description: Manage and edit security rules | ||
| keywords: [SIEM, security rule, rules, cloud security, Security information and event management, Security information] | ||
| --- | ||
|
|
||
|
|
||
| There are two types of rules in Cloud SIEM: | ||
|
|
||
| * A protected rule is a rule defined by Logz.io. These rules appear in the **Rule definitions** list with a **Logz.io rule** tag. You cannot edit the name or logic of a protected rule unless you duplicate the rule as described in this document. You can, however, define what accounts to apply the rule to, edit the trigger conditions, tags and recipient endpoints of a protected rule. | ||
| * A **protected rule** is a rule defined by Logz.io. These rules appear in the **Rule definitions** list with a **Logz.io rule** tag. You can only edit the name or logic of a protected rule if you duplicate the rule as described in this document. You can, however, define what accounts to apply the rule to and edit the trigger conditions, tags, and recipient endpoints of a protected rule. | ||
|
|
||
| * A regular rule is a rule defined by the user. These rules appear in the **Rule definitions** list without a tag. You can edit the name and logic of a regular rule, as well as define what accounts to apply the rule to, edit the trigger conditions, tags and recipient endpoints of the rule. | ||
| * A **custom rule** is a rule defined by the user. These rules appear in the **Rule definitions** list without a tag. You can edit the name and logic of a regular rule, define what accounts to apply the rule to and edit the rule's trigger conditions, tags, and recipient endpoints. | ||
|
|
||
| ## Manage Custom Rules | ||
|
|
||
| ## Edit a regular rule: | ||
| Navigate to your Logz.io [SIEM account > Rules](https://app.logz.io/#/dashboard/security/rules/rule-definitions). | ||
|
|
||
| 1. Sign in to Logz.io. | ||
| Find a custom rule created by you or your team. These rules include the name of the user who created them. | ||
|
|
||
| 2. Go to **SIEM > Rules**. | ||
|  | ||
|
|
||
|  | ||
| Click the pencil icon on the right side of the rule you want to edit. | ||
|
|
||
| 3. Select the three dots menu on the right side of a rule that you need to edit. | ||
|  | ||
|
|
||
|  | ||
| You can review and edit the rule according to your needs. Click **Save** to apply the changes. | ||
|
|
||
|
|
||
| 4. Select **Edit**. | ||
| ## Manage Protected Rules | ||
|
|
||
| 5. Edit the rule. | ||
| Rules that are Preconfigured By Logz.io cannot be edited. However, you **can add** trigger thresholds and notification options. | ||
|
|
||
| 6. Select **Save**. | ||
| Navigate to your Logz.io [SIEM account > Rules](https://app.logz.io/#/dashboard/security/rules/rule-definitions). | ||
|
|
||
| If you need to customize a protected rule, you can clone it, adjust the cloned rule to your needs and then disable the original protected rule. To do tis: | ||
| Choose the rule you want to edit and click the pencil icon on the right side menu. | ||
|
|
||
| ## Clone and edit an existing rule: | ||
| Edit the trigger thresholds or the notification options, and click **Save** to apply the changes. | ||
|
|
||
| 1. Sign in to Logz.io. | ||
|  | ||
|
|
||
| 2. Go to **SIEM > Rules**. | ||
|
|
||
|  | ||
| ## Duplicate and Edit Protected Rules | ||
|
|
||
| 3. Select the three dots menu on the right side of a rule that you need to clone. | ||
| You can edit and change preconfigured Logz.io rules by duplicating them. | ||
|
|
||
| 4. Select **Duplicate**. | ||
| Navigate to your Logz.io [SIEM account > Rules](https://app.logz.io/#/dashboard/security/rules/rule-definitions). | ||
|
|
||
| 5. Edit the rule. | ||
| Choose the rule you want to duplicate, click on the three dots next to it, and choose **Duplicate**. | ||
|
|
||
| 6. Select **Save**. | ||
|  | ||
|
|
||
| 7. In the **State** column of the original protected rule, set the state selector to the disabled mode. | ||
| The rule configuration wizard includes all the settings set by Logz.io, and you can edit, change, or remove elements from each section. | ||
|
|
||
| Click **Save** to apply the changes. | ||
|
|
||
| Navigate to the main [Rules](https://app.logz.io/#/dashboard/security/rules/rule-definitions) page, find the original preconfigured rule you've duplicated, and change its **State** to disable it. |
66 changes: 38 additions & 28 deletions
66
docs/user-guide/cloud-siem/quick-guide/manage-security-events.md
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -1,59 +1,69 @@ | ||
| --- | ||
| sidebar_position: 9 | ||
| title: Managing Security Events | ||
| title: SIEM Event Management | ||
| image: https://dytvr9ot2sszz.cloudfront.net/logz-docs/social-assets/docs-social.jpg | ||
| description: Manage and filter security events in Logz.io | ||
| keywords: [SIEM, security event, events, cloud security, Security information and event management, Security information] | ||
| --- | ||
|
|
||
| Cloud SIEM has an integrated platform for security events management. Here you can view security events that have occured, edit them, assign a security rule to a team member. You can filter the list using the top menu filters and the search bar. | ||
|
|
||
| 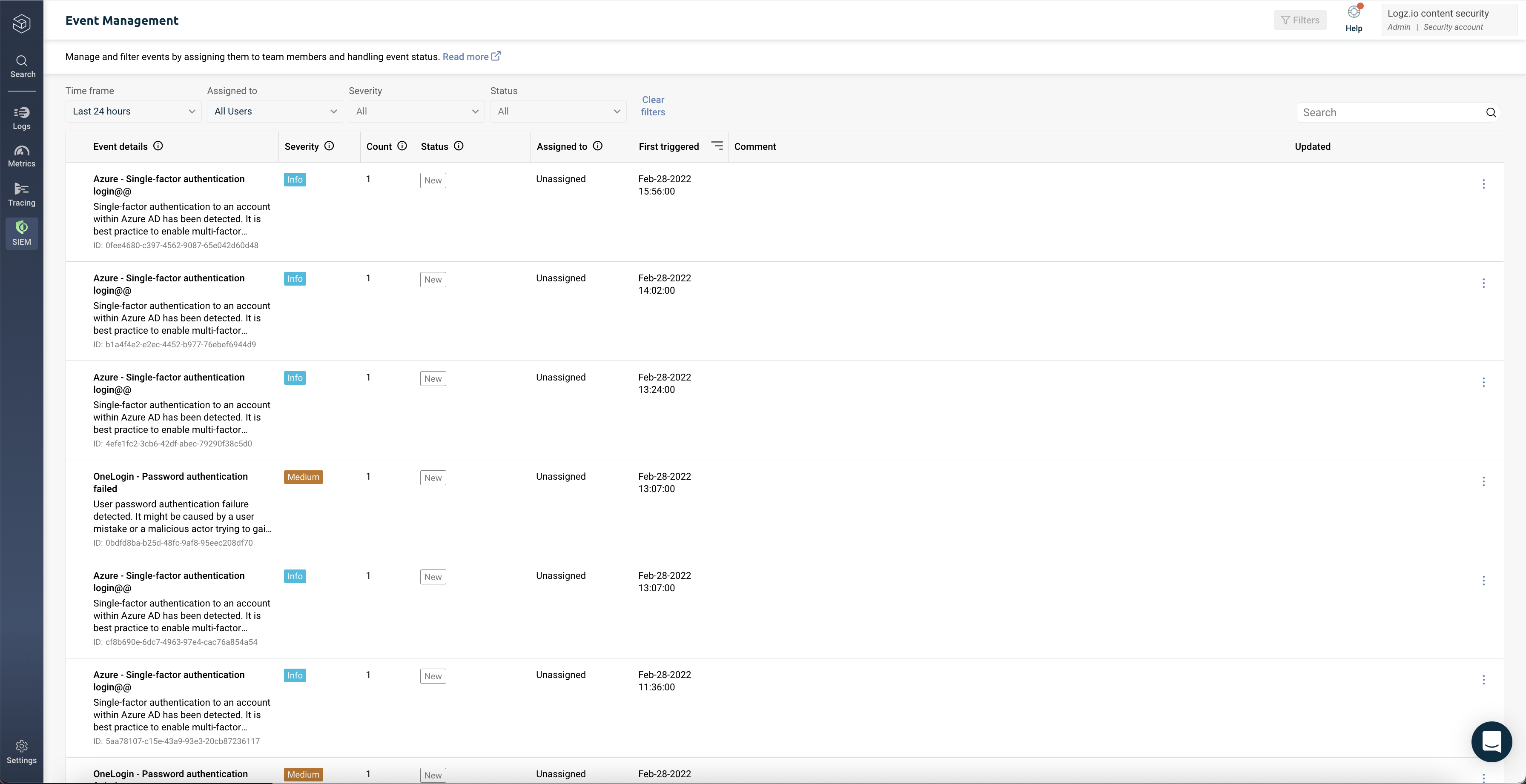 | ||
| Event management is an integrated platform to monitor and manage security events. The table provides an overview of all security events in your environment, where you can view the event's history, investigate it, edit the rule related to the event, and assign the event to one of your team members. | ||
|
|
||
| ## Event Management Overview | ||
|
|
||
|
|
||
| :::note | ||
| The event manager has a retention period of 2 weeks. Older events are **saved as logs** on your security account and can be viewed from OpenSearch Dashboards. | ||
| ::: | ||
|
|
||
|
|
||
| ### Access Event Management | ||
|
|
||
| To access the **Event Management** platform: | ||
|  | ||
|
|
||
|
|
||
| 1. Sign in to Logz.io. | ||
| The event management table presents your latest events with useful information, including: | ||
|
|
||
| 2. Go to **SIEM > Event Management**. | ||
| * **Event details**, such as event ID, title, and description of the triggered event | ||
| * Each event **severity level**, as defined in the rule that triggered it | ||
| * Relevant **status** for each event. The status can be: | ||
| * New - A triggered event that has not been assigned | ||
| * Assigned - Assigned to a handler and is pending investigation | ||
| * In progress - The assigned handler is actively investigating the event | ||
| * Waiting for response - Investigation is on hold pending a reply from external stakeholders | ||
| * False positive - Investigation verified that the detected activity is benign | ||
| * Resolved - The investigation is complete | ||
| * **Assigned to** show the handler handling event investigation and resolution. Once assigned to a team member, you cannot reset the event to "Unassigned" | ||
| * The date and time when the event was **last triggered** | ||
| * You and your team members can add **comments** to each event, which will show in the table | ||
| * Indicated when an event was last **updated** if a team member updated it | ||
|
|
||
|  | ||
|
|
||
| In addition, you can **edit** the assignees and comments for each event, **investigate** it, **edit the rule** that triggered the event, and **view the event's history**. | ||
|
|
||
|  | ||
|
|
||
| :::info note | ||
| The event manager has a retention period of 2 weeks. Older events are **saved as logs** on your security account and can be viewed from OpenSearch Dashboards. | ||
| ::: | ||
|
|
||
| ### Edit an event rule | ||
|
|
||
| To edit a rule for an event: | ||
|
|
||
| ### Investigate Events | ||
|
|
||
| 1. Select the three dots menu on the right side of an event that you need to edit and then select **Edit**. It will open the editor for the event rules. | ||
| Click the **Investigate** button to open the quick view panel with additional details about the event and when it was triggered. The quick view allows you to assign the event to a team member by choosing the relevant memebr from the drop down list. You can dive deeper into each trigger by clicking the **Investigate** button next to it, and opening the relevant logs for each event. | ||
|
|
||
|  | ||
|  | ||
|
|
||
| ### View Event History | ||
|
|
||
| 2. Edit the rule conditions. This is different for regular rules where you can edit any field and a protected rule where some fields are locked. | ||
| Click the three dots to access the **View History** option. The popup includes the event's ID, description, and timeline. | ||
|
|
||
|  | ||
| Event history helps you keep track of what happened to it during the last 2 weeks, including when it was created, who the handler is, and updates regarding its status. | ||
|
|
||
|
|
||
|
|
||
| ### Edit the event information | ||
|
|
||
| To edit the management information on an event: | ||
|
|
||
| ### Grouped Events | ||
|
|
||
| 1. Select **Edit** on the event row. | ||
| Events with the same severity and the same Group By field values, will be grouped together. For example, suppose multiple rules are triggering for the same use case, authentication failed from a malicious IP, and suspicious activity is detected from the same IP. In that case, they will be grouped into a single event. | ||
|
|
||
|  | ||
| You can see in the table an indication of grouped events and the number of events grouped in this rule. | ||
|
|
||
|  | ||
|
|
||
| 2. Change the rule status, assignment or a comment to the rule. | ||
| Some events start as a single event, and as more rules and events occur, they will be grouped. This affects the event's history since grouped events display the history from when the events were grouped and not before. | ||
|
|
||
|  | ||
| Some events may initially appear as individual events, but as additional rules and events occur, they will be combined into a group event. This impacts the event's history because grouped events will display their history from when they were grouped rather than any earlier history of the single event. |