The ultimate, yet easy to use, privacy manager for Android
- Description
- Features
- Restrictions
- Limitations
- Compatibility
- Installation
- Upgrading
- Usage
- Permissions
- Frequently asked questions
- Support
- Changelog
- Similar solutions
- News
- Contributing
- License
XPrivacy can prevent applications from leaking privacy sensitive data. XPrivacy can restrict the categories of data an application can access. This is done by feeding an application with no or fake data. There are several data categories which can be restricted, for example contacts or location. For example, if you restrict access to contacts for an application, this will result in sending an empty contact list to the application. Similarly, restricting an application's access to your location will result in a fake location being sent to the application.
XPrivacy doesn't revoke (i.e. block) permissions from an application, which means that most applications will continue to work as before and won't force close. There are two exceptions to this, access to the internet and to external storage (typically an SD card) is restricted by denying access (revoking permissions). There is no other way to implement this, since these permissions are handled by Android in a special way. Android delegates handling of these permission to the underlying Linux network/file system. XPrivacy will fake offline (internet) and/or unmounted (storage) state, but some applications try to access the internet/storage nevertheless, potentially resulting in crashes or error messages.
If restricting a category of data for an application results in problems for the application, it is possible to allow access to the data category again to solve the issue.
By default, all newly installed applications will have no access to any data category at all, to prevent a new application from leaking sensitive data right after installation. Shortly after installing a new application, XPrivacy will ask which data categories you want the new application to have access to. XPrivacy comes with an application browser, which allows you to quickly enable or disable applications' access to a particular data category for example to view your calendar. It is also possible to edit all data categories for one application.
To help you identify potential data leaks, XPrivacy will monitor attempts made by all applications to access sensitive data. XPrivacy will display an orange warning triangle icon as soon as data of a data category has been used. If an application has requested Android permissions to access data in a data category, this will be displayed with a green key icon. XPrivacy will also display if an application has internet access, indicating that the application poses a risk of sharing the data it obtains with an external server.
XPrivacy is built using the Xposed framework. XPrivacy taps into a vast number of carefully selected functions of Android through the Xposed framework. Depending on the function, XPrivacy conditionally skips execution of the original function (for example when an application tries to set a proximity alert) or alters the result of the original function (for example to return an empty message list).
XPrivacy has been tested with Android version 4.0.3 - 4.4.2 (ICS, JellyBean, KitKat), and is reported to work with most Android variants, including stock ROMs. Root access is needed to install the Xposed framework.
XPrivacy was a lot of work, so please support this project
Donate a few dollars for the pro version
OR
buy the pro enabler from Google play
OR
Using XPrivacy is entirely at your own risk
- Simple to use
- No need to patch anything (no source, no smali or anything else)
- For any (stock) variant of Android version 4.0.3 - 4.4.2 (ICS, JellyBean, KitKat)
- Newly installed applications are restricted by default
- Displays data actually used by an application
- Free and open source
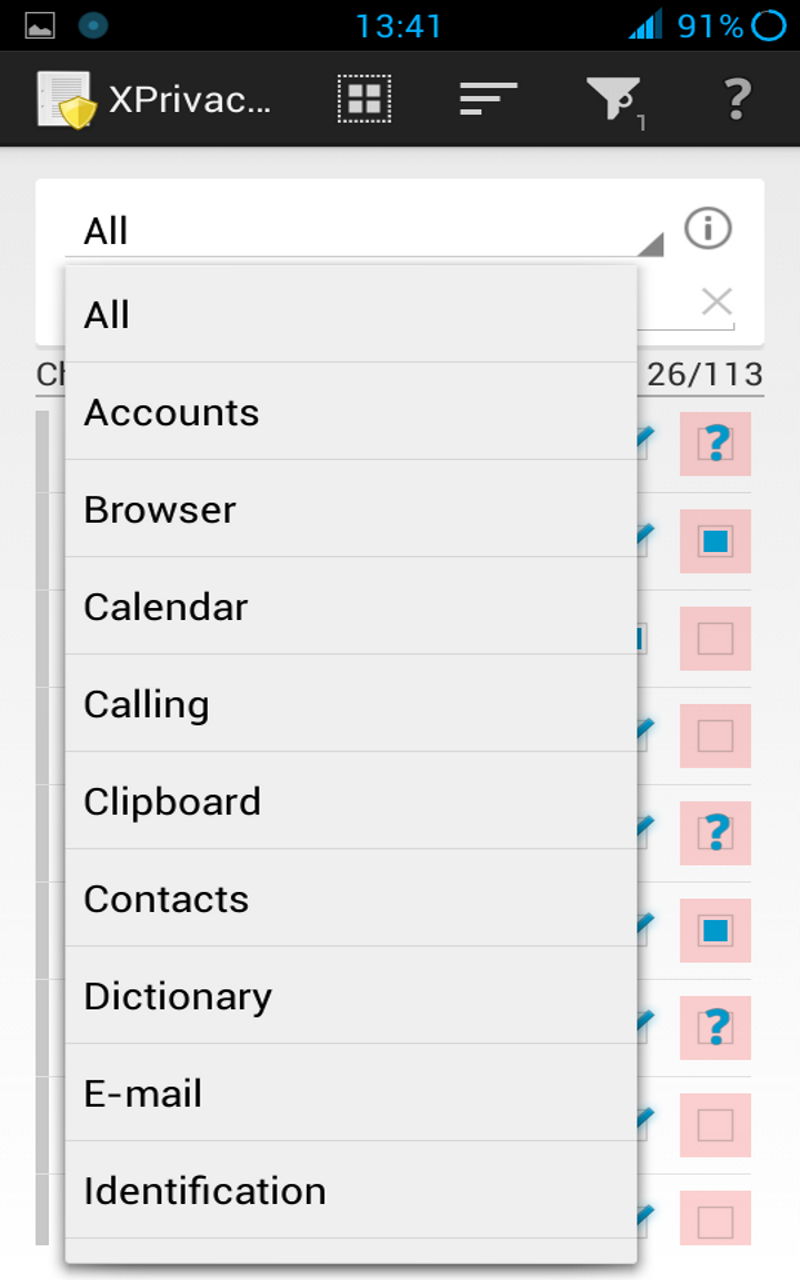
For easy usage, data is restricted by category:
- Accounts
- Browser
- Calendar
- Calling
- Clipboard
- Contacts
- Dictionary
- Identification
- return a fake Android ID
- return a fake device serial number
- return a fake host name
- return a fake Google services framework ID
- return file not found for folder /proc
- return a fake Google advertising ID
- return a fake system property CID (Card Identification Register)
- return file not found for /sys/block/.../cid
- return file not found for /sys/class/.../cid
- return fake input device descriptor
- Internet
- IPC
- Location
- return a random or set location (also for Google Play services)
- return empty cell location
- return an empty list of (neighboring) cell info
- prevents geofences from being set (also for Google Play services)
- prevents proximity alerts from being set
- prevents sending NMEA data to an application
- prevent phone state from being sent to an application
- Cell info changed
- Cell location changed
- prevent sending extra commands (aGPS data)
- return an empty list of Wi-Fi scan results
- prevents connecting to Google Play services
- Media
- Messages
- Network
- NFC
- Notifications
- prevent receiving statusbar notifications (Android 4.3+)
- prevent C2DM messages
- Overlay
- Phone
- return a fake own/in/outgoing/voicemail number
- return a fake subscriber ID (IMSI for a GSM phone)
- return a fake phone device ID (IMEI): 000000000000000
- return a fake phone type: GSM (matching IMEI)
- return a fake network type: unknown
- return an empty ISIM/ISIM domain
- return an empty IMPI/IMPU
- return a fake MSISDN
- return fake mobile network info
- Country: XX
- Operator: 00101 (test network)
- Operator name: fake
- return fake SIM info
- Country: XX
- Operator: 00101
- Operator name: fake
- Serial number (ICCID): fake
- return empty APN list
- return no currently used APN
- return an empty call log
- prevent phone state from being sent to an application
- Call forwarding indication
- Call state changed (ringing, off-hook)
- Mobile data connection state change / being used
- Message waiting indication
- Service state changed (service/no service)
- Signal level changed
- return an empty group identifier level 1
- Sensors
- Shell
- Storage
- revoke permission to the media storage
- revoke permission to the external storage (SD card)
- return fake unmounted state
- System
- return an empty list of installed applications
- return an empty list of recent tasks
- return an empty list of running processes
- return an empty list of running services
- return an empty list of running tasks
- return an empty list of widgets
- return an empty list of applications (provider)
- prevent package add, replace, restart and remove notifications
- View
- prevent links from opening in the browser
- return fake browser user agent string
- Mozilla/5.0 (Linux; U; Android; en-us) AppleWebKit/999+ (KHTML, like Gecko) Safari/999.9
- /proc, CID and system (build) properties cannot be restricted for Android (serial number, IMEI, MAC address, etc), because it will result in bootloops
- /proc/self/cmdline will not be restricted by /proc, because it will result in instability
- Phone number cannot be restricted for the standard phone application
- Internet and storage can only be restricted for applications/providers/services started by the Android package manager
- Due to its static nature Build.SERIAL can only be randomized on application start and there is no usage data
- Due to a bug in Chromium the user agent cannot be restricted in all cases (issue)
- Due to a custom implementation the clipboard cannot be restricted on some Samsung stock ROMs (issue)
- You cannot restrict the Android ID used for submitting restrictions (only pro version)
- It is not possible to restrict hardware MAC addresses or the external IP address
- With LBE Security Master installed, Android cannot be restricted
- You cannot restrict IPC for XPrivacy, because it is needed for internal checks
- You cannot restrict storage for XPrivacy, because it is needed to read the pro license file
- You cannot restrict system fro XPrivacy, because it is needed to get an application list
- You cannot restrict view for XPrivacy, because it is needed to open links to the crowd sourced restrictions
- No on demand restricting for Configuration.MCC/MNC
You can still restrict accounts, contacts and other things for XPrivacy.
XPrivacy has been tested with Android version 4.0.3 - 4.4.2 (ICS, JellyBean, KitKat), and is reported to work with most Android variants, including stock ROMs.
Instead of following the steps below, you can use the XPrivacy Installer.
It seems like a lot of steps, but it is done in no time:
- Requirements:
- Android version 4.0.3 - 4.4.2 (ICS, JellyBean, KitKat); check with System Settings > About phone > Android version
- Custom recovery (CWM, TWRP or similar)
- Read about compatibility before installing
- Make a backup
- If not done already: root your device; the procedure depends on the brand and model of your device
- You can find a guide here for most devices
- Enable System settings > Security > Unknown sources
- Install the Xposed framework
- Be sure to install the latest version
- The Xposed fix is not needed anymore
- Download and install XPrivacy from here
- Alternatively download from here
- Enable XPrivacy from the Xposed installer
- Reboot
I do not recommend using XPrivacy in combination with any of the similar solutions, because it could result in conflicts (with as possible consequence data leakage).
If you want to uninstall XPrivacy, you have two options:
- Disable XPrivacy in the Xposed installer
- Uninstall Xposed using the Xposed installer
- Make a backup
- Do not remove the previous version (else your settings will get lost)
- Download the new version
- Install the new version over the previous version
- Reboot your device
When following this procedure your data will not leak, because the Xposed part of XPrivacy keeps running.
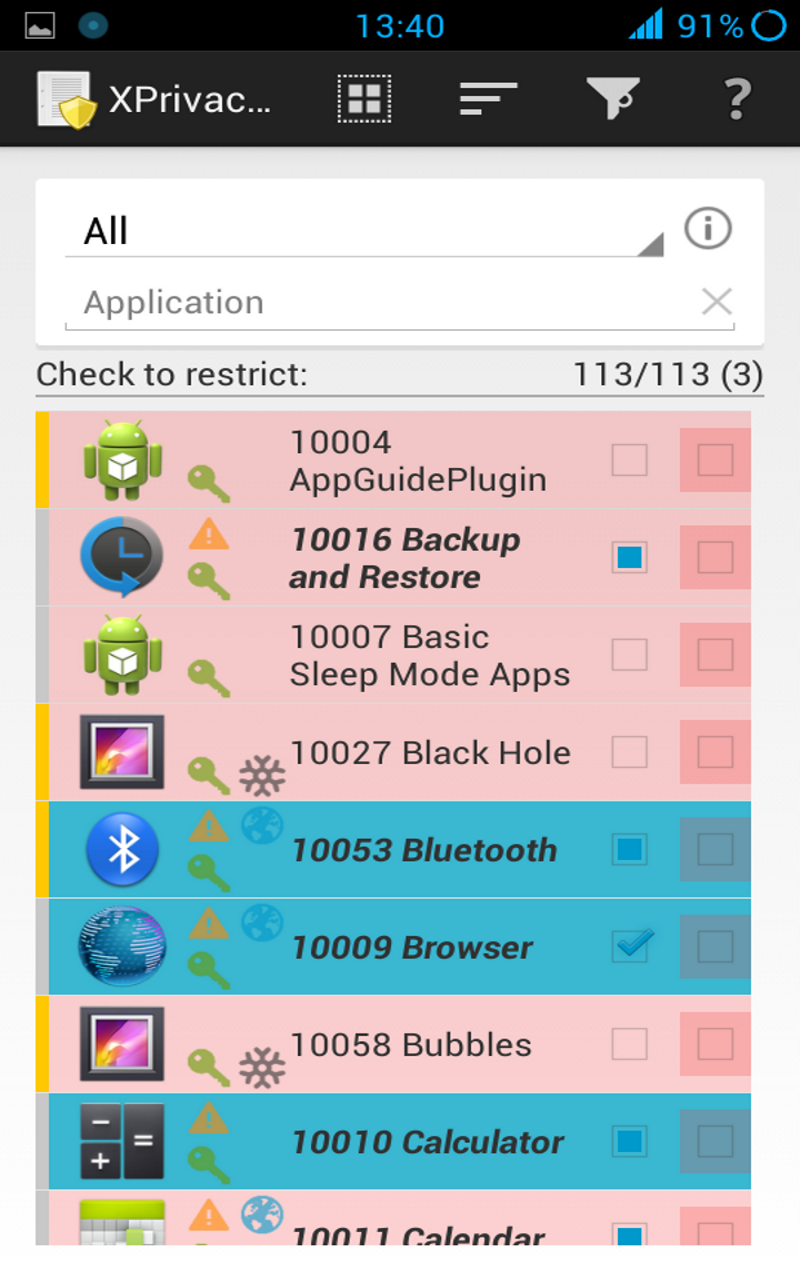
The application starts in the main view, where at the top a data category can be selected. By ticking one or more check boxes in the list below, the selected data category can be restricted for the chosen applications. The default category is All, meaning that all data categories will be restricted.
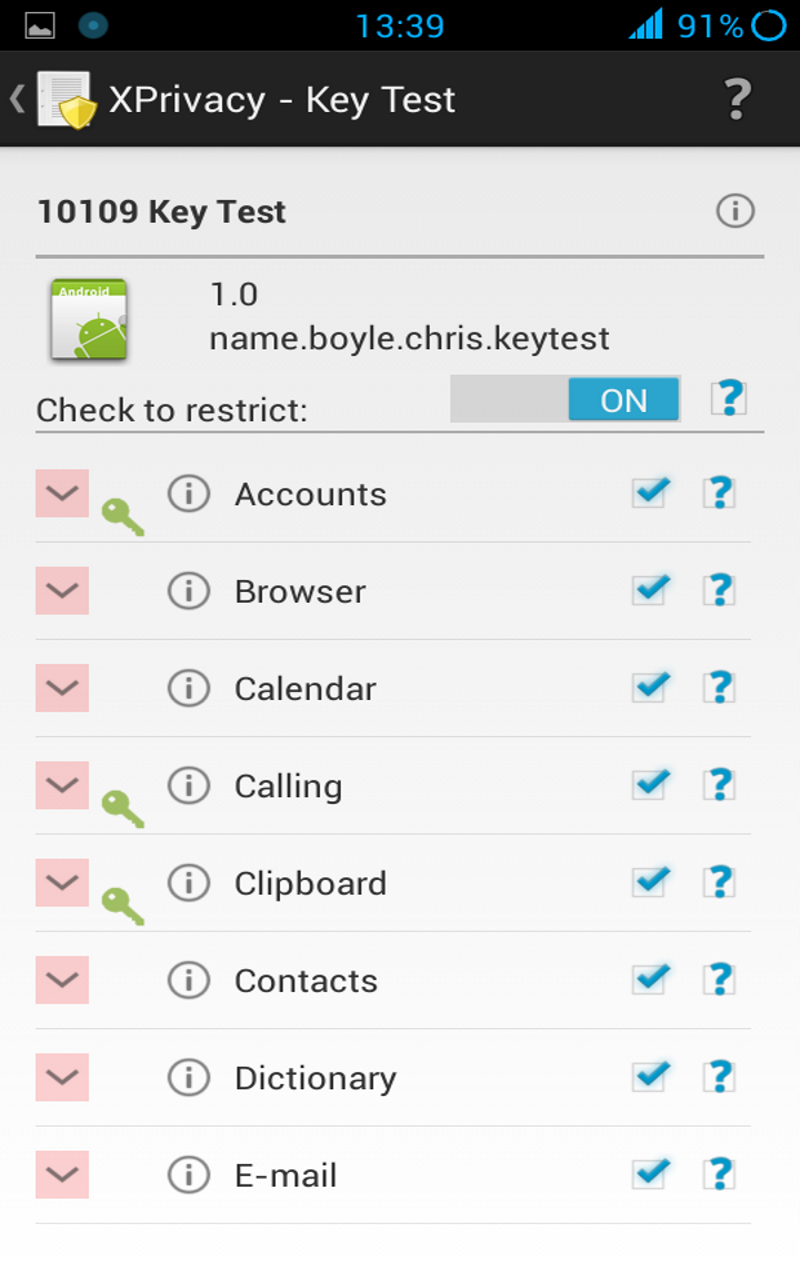
Tapping on an application icon shows the detailed view, where all the data categories for the selected application can be managed. This view will also appear by tapping on the notification that appears after updating or installing an application. By default all data categories will be restricted for new installed applications to prevent leaking privacy sensitive data from the beginning. You can change which data categories will be restricted by changing the Template available from the main menu.
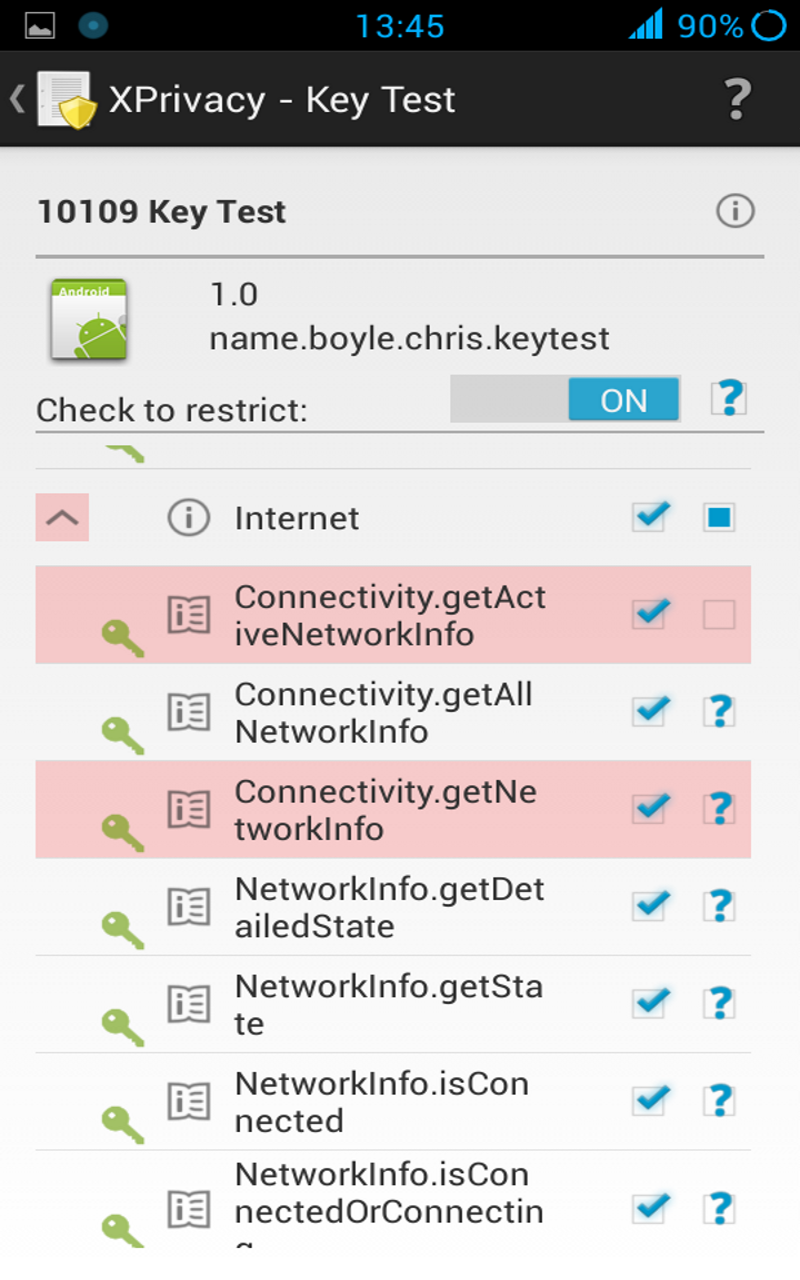
Data categories exist to make it easier to manage restrictions. The data categories in the detailed view can be drilled down to individual functions. If the category is restricted, individual functions can be allowed by clearing the function check boxes.
To see it in action: try restricting the category Identification for Android Id Info or try restriction the category Contacts for the Contacts application.
Applying some restrictions require restarting applications and/or your device
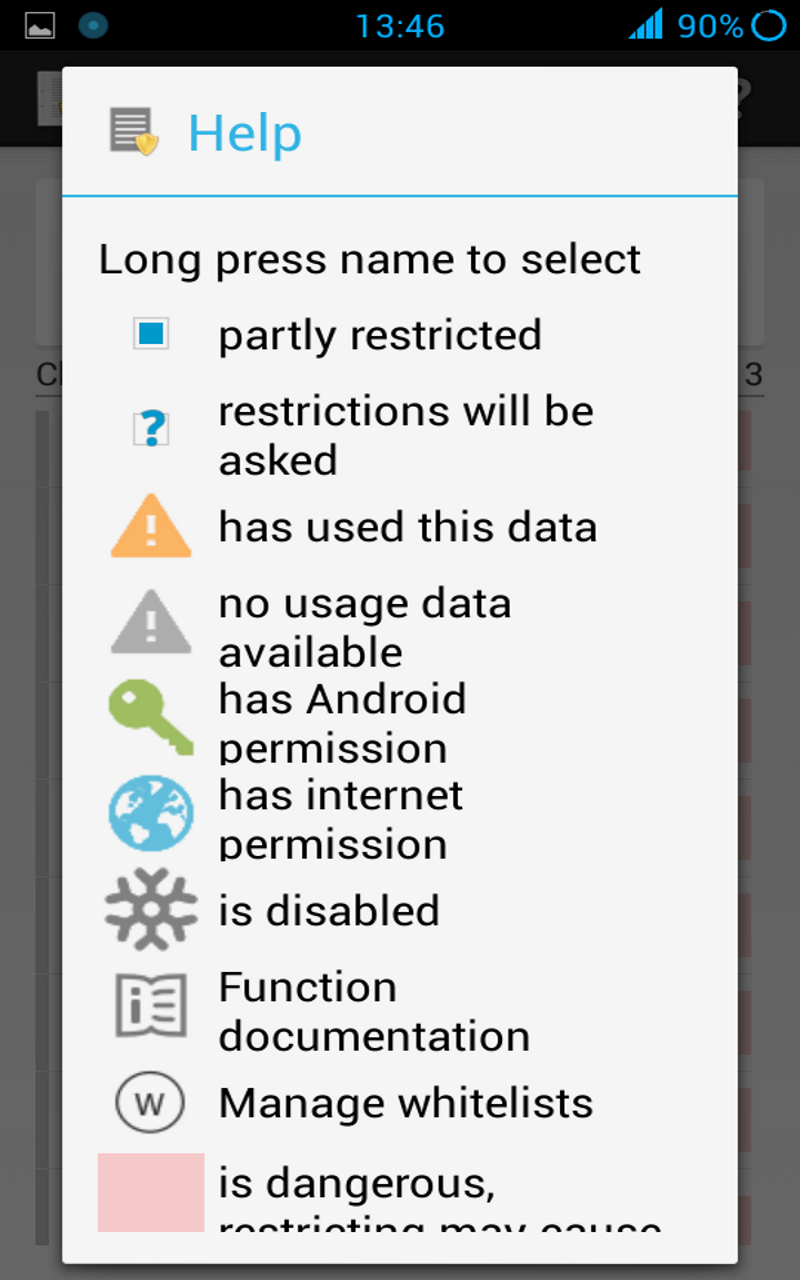
If an application requested Android permissions for a data category, the category will be marked with a green key icon. If an application used/tried to use data, the data category will be marked with an orange warning triangle icon. If an application has internet permissions a world globe icon will be shown. These icons are just a guideline, because an application can access some privacy sensitive data without Android permissions, for example the serial number of your device and because is not possible to monitor data usage in each and every situation, for example not for access to the internet or the external storage. Be aware that an application could access the internet through other (sister) applications.
Enabling the internet or storage restriction means blocking access to the internet or to the external storage (typically the SD card). This may result in error messages and even in forced closes of the application.
Some category and function restrictions are considered dangerous. These categories and functions are marked with a redish background color. Some applications will crash if you restrict these categories and/or functions.
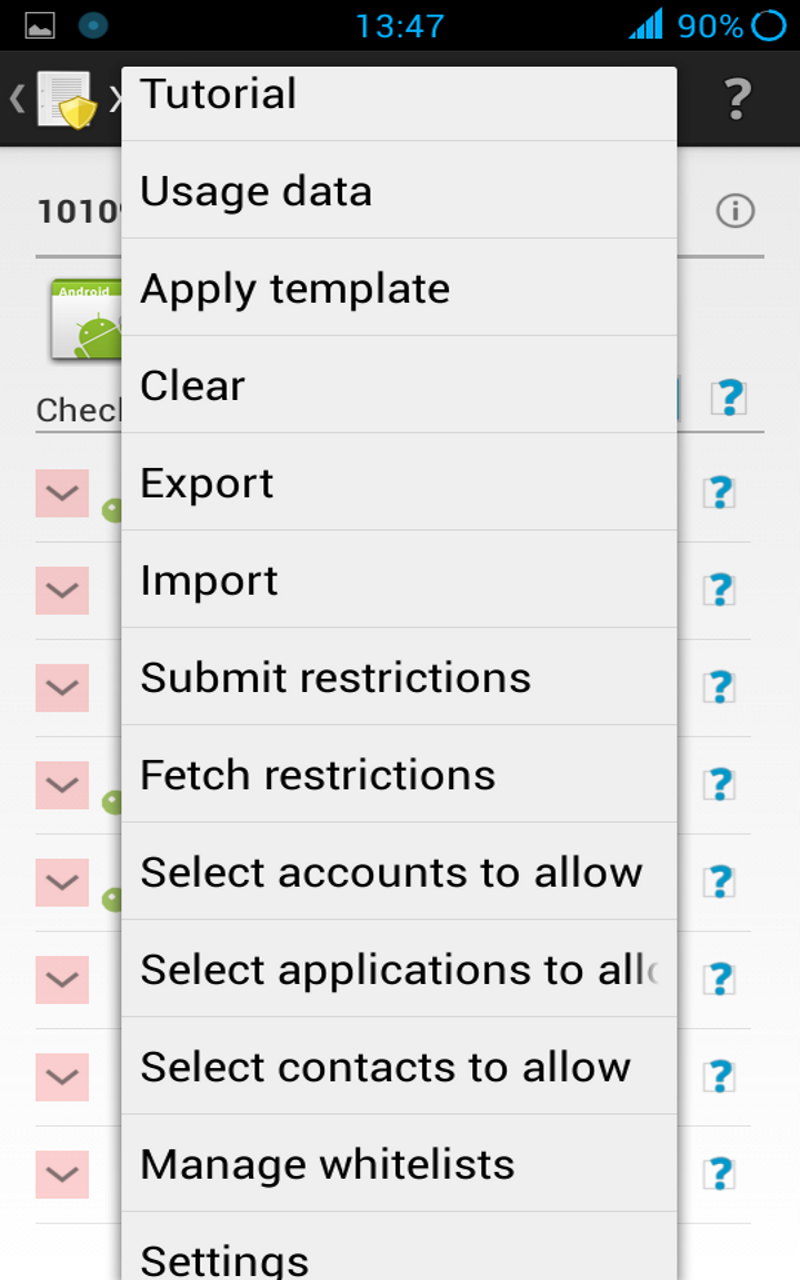
There are global settings and application specific settings, respectively accessible from the menu of the application list and the menu of the application details view. The global settings, like a randomized or set latitude/longitude, apply to all applications, unless you set any application specific setings. In that case all global settings are overriden by the application specific settings. There is one special case: saving empty specific application settings (you can use the clear button) will erase all application specific settings, so that the global settings will be used again.
The template, available from the main menu is applied to newly installed applications or if you use the menu apply template from the application details view.
Using XPrivacy is entirely at your own risk
XPrivacy asks for the following Android permissions:
- Accounts: to select accounts to allow for applications
- Contacts: to select contacts to allow for applications
- Boot: to check if XPrivacy is enabled
- Internet: to submit/fetch crowd sourced restrictions
- Storage: to export settings to the SD card (only pro version)
If you don't like this, you can always restrict XPrivacy itself ...
(1) Will XPrivacy make my device slower?
Maybe a little bit, but it will probably not be noticeable.
(2) Does XPrivacy use a lot of memory or battery?
Almost nothing.
(3) Can you help me with rooting my device?
There are already enough guides to help you to root your device. Use your favorite search engine to find one.
(5) How can I reset all XPrivacy settings?
Menu > Clear all data
Reboot.
(6) Can I backup XPrivacy restrictions, settings and usage data?
You cannot backup XPrivacy data with standard backup tools, like Titanium backup, since version 1.11.13 anymore. This is because the database (new in version 1.11.13) is not stored in the XPrivacy data folder, but in a system folder. I have tried to store the database in the XPrivacy data folder, but this leads to all kind of permission problems.
The best way to backup XPrivacy data is to use the export function, but this requires the pro version.
You can automate backups by sending an intent:
adb shell am start -a biz.bokhorst.xprivacy.action.EXPORT
This can be done with for example with Tasker.
New task: Any name you like Action Category: Misc/Send Intent Action: biz.bokhorst.xprivacy.action.EXPORT Target: Activity
(10) Which functions are exactly restricted?
Many, see here for all details.
Great care has been taken to develop XPrivacy, nevertheless data could leak and applications can crash, although this is fortunately rare.
(14) I get 'Incompatible ...' !
An internal check of XPrivacy failed, resulting in potential data leakage. Please press OK to send me the support information, so I can look into it.
(15) What is the procedure for a ROM update?
The right order for ROM updates is:
- Export XPrivacy settings
- Enable flight mode
- Clear XPrivacy data (please note that this will erase the imported pro license file if any)
- Reboot to recovery
- Flash ROM
- Flash Google apps (optional)
- Re-activate Xposed using Xposed toggle
- Reboot to Android
- Restore the android ID (when needed; with for example Titanium backup)
- Import XPrivacy settings
- Disable flight mode
- Fake network type (Wi-Fi, mobile)
(this assumes no data wipe and Xposed and XPrivacy installed before updating the ROM)
If you skip the XPrivacy import/clear/export steps some system applications can have the wrong restrictions, because the uid's of these applications might have been changed.
For export/importing XPrivacy data you need pro version.
(16) Can I restrict root access?
Yes, you can by restricting su shell access.
(17) Will restrictions be applied immediately?
It can take up to 15 seconds before changes in restrictions will be effective, because of caching. Changing the internet and storage restriction requires an application restart. Please note that in many cases pressing back, only moves the application to the background.
(19) Does XPrivacy have a firewall?
Yes, you can restrict internet access for any application. If you want to partly enable internet, for example for Wi-Fi only, you will have to use a firewall application, like AFWall+. The reason is that XPrivacy works within Android and detailed firewall rules can only be applied within the Linux kernel.
(21) I get 'Unable to parse package'
This means the downloaded apk file is corrupt. Try disabling your popup blocker or download using another computer.
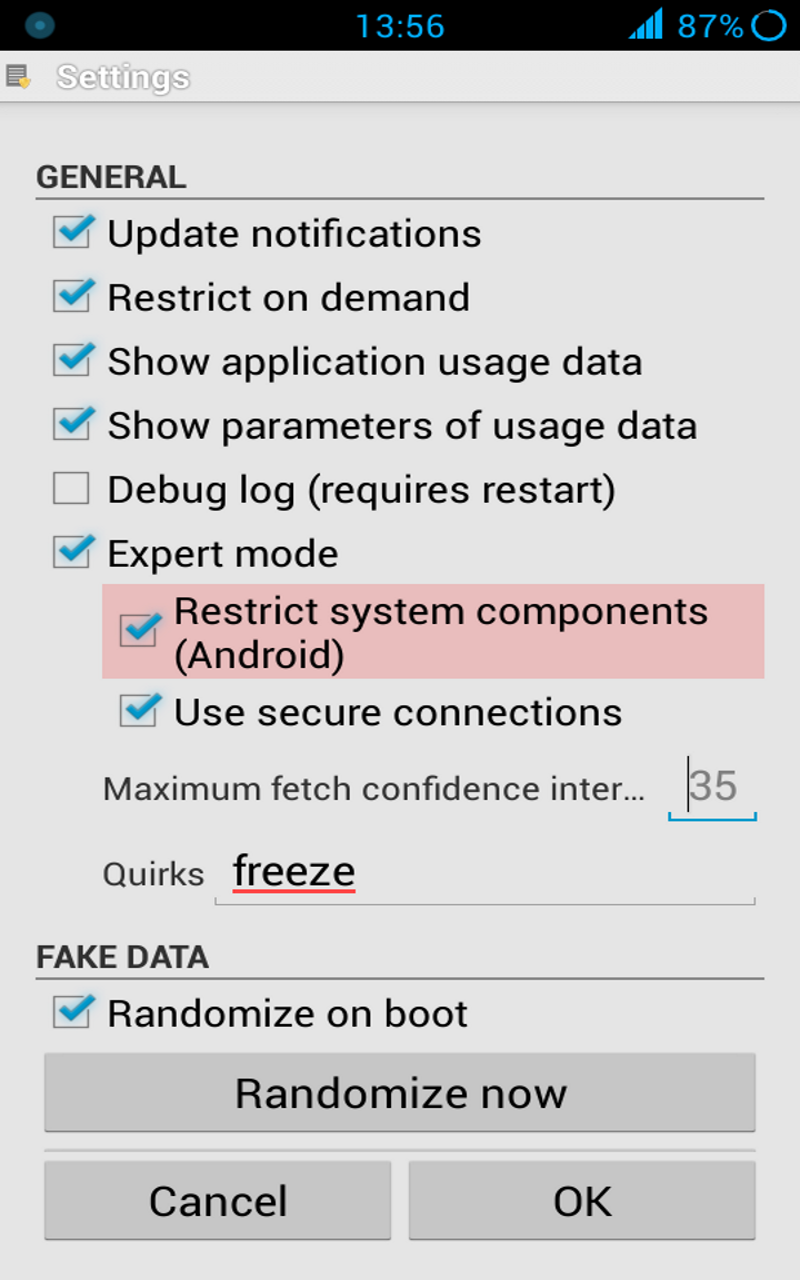
Enable debug logging using the settings menu and see here.
(23) Where are the settings of XPrivacy stored?
The restrictions, settings and usage data of XPrivacy are stored in an sqlite3 database in this folder:
/data/xprivacy
(25) Why doesn't clearing a data category restriction clear the function exceptions too?
If you accidentally undo a data category restriction all the function exception would be lost. The function exceptions only apply when the data category is restricted.
(26) How can I export/import my settings?
For this you need the pro version. Exported settings are stored in the folder .xprivacy in the file XPrivacy.xml. You can copy this file to the same place on a second device. When importing, settings are only applied to applications that exist on the second device. This also applies to system applications.
Note that allowed accounts and allowed contacts (not the accounts and contacts itself) can only be imported when the android ID is the same. See question 15 about what to do when updating your ROM.
(28) I have restricted locations but my GPS status icon still appears
That is correct, XPrivacy only replaces the real location by a fake location. It even uses the real location to randomize the fake location. The idea is that everything should appear as normal as possible to an application.
(29) How about multi-user support?
Additional users can install and use XPrivacy like the primary user.
(30) Why is the location search in the settings disabled?
Because some Google components are not installed.
(31) Do I still need root after installing Xposed?
No.
(32) Why is XPrivacy not available in the Play store anymore?
Read here why.
(33) What is 'Template' used for?
The template is used to apply restrictions to newly installed applications and when you use the menu Apply template.
(34) Will there be a iOS / Window phone version?
No, because these OS'es are to closed to implement something like XPrivacy.
- The device brand/manufacturer
- The device model/product name
- The device (phone) type
- The network type (mobile, Wi-Fi, etc.)
- Synchronization state
- Screen locking
- Display settings
- Wi-Fi settings
- Bluetooth settings
- Shortcuts
- Starting other applications
- Android version
- Vibration
- Checks for root
No, because I don't consider this as privacy sensitive data (=able to identify you and collect data about you). I am happy to add new restrictions for data that is really privacy sensitive.
(36) What are the experimental functions?
See the change log
(37) Does XPrivacy work with SELinux (Fort Knox) ?
Yes.
(39) How does the tri-state check box work?
The tri-state check box follows this pattern:
- Unchecked = no retrictions
- Solid square = some restrictions
- Check mark = all restrictions
Some/all is determined as follows:
- All category: some/all other categories
- Other categories: some/all functions
Be aware that by default categories and functions are filtered by permission, so you may not see all of them. The check box state is independent of this.
(41) Why are not all pro features available with the pro enabler?
The pro enabler is in the Play store on request of some early XPrivacy users. In the beginning there was just one pro feature: export/import of all restrictions and settings. In a later stage fetching crowd sourced restrictions were added as a pro feature. Processing of the crowd sourced restrictions requires a big server which has to be paid for. The low price of the pro enabler, don't forget Google takes already 30%, didn't allow to give this feature for free to existing users. Looking back I would never have put the pro enabler into the Play store, but I cannot remove it anymore now, because of the existing users.
(42) What should I do if an application force closes (crashes)?
Take a look into the usage view of the application, available through the menu in the application details view, to see which functions the application uses. Disable category and/or function restrictions one by one until you have found the one causing the force close. Help others by submitting your working restrictions.
(43) Can XPrivacy handle non-Java applications?
In general, due to the architecture of Android (isolated virtual machines), any call to native libraries and binaries is through Java and can thus be restricted by XPrivacy. As far as known any route to a native library or binary is covered by XPrivacy.
XPrivacy cannot hook into native libraries, but can prevent native libraries from loading. This could break applications, like Facebook, but can prevent malware from doing its work.
XPrivacy can also restrict access to the Linux shell (including superuser), to prevent native binaries from running.
You can find the restrictions in the Shell category.
Version 2.0+ has protection against direct interprocess communication (IPC).
(44) I see data usage without Android permissions!
A lot of functions do not require Android permissions, so this is quite normal. Sometimes an application tries to use a function which it doesn't have Android permission for. Since XPrivacy mostly runs before the function is run, this will be registered.
If you filter on permissions and an application tried to use a function without having these permissions, the application will still be shown.
If you think a function requires permissions, while XPrivacy shows not, please report this.
(45) How can I restrict the hardware/external MAC/IP/IMEI address/number?
You can restrict the IP and MAC addresses and IMEI number for any application.
The external IP is assigned by your provider and can thus not be changed. You could use a VPN or TOR to hide your external IP to a certain extend.
The hardware MAC address can be changed on some devices, but this is device dependent and can only be done on driver or kernel level. XPrivacy works only on Android level and device independent.
The same applies to the IMEI number, with as additional problem legal issues in most countries.
(46) Why do I need to register to submit restrictions?
This is to prevent a malicious application maker from automatically submitting a lot of allow restriction to outvote user submitted restrictions.
If you encounter a bug please create an issue.
Include a logcat when relevant (use pastebin or a similar service).
Do not forget to enable XPrivacy logging using the settings menu!
Please describe the exact steps to reproduce the issue and include information about your device type and Android version.
If you have a feature request, please create an issue.
If you have any question, you can leave a message in the XDA XPrivacy forum thread.
Before submitting any issue please make sure you are running the latest version of XPrivacy.
Before submitting any issue please make sure XPrivacy is causing the problem by disabling XPrivacy.
One bug report / feature request per issue please!
Do not use my personal or XDA e-mail for bug reports, feature requests or questions.
It is okay to use my personal or XDA e-mail for things that cannot be shared in public, such as security reports.
The changelog has been moved here.
- PDroid
- PDroid 2.0
- OpenPDroid
- LBE Privacy Guard
- CyanogenMod Incognito Mode
- Per App Settings Module
- Android 4.3+ Permission Manager
The PDroid family provides fake or no data, more or less in the same way as XPrivacy does. A difference is that you need to patch Android and that there is (therefore) only limited stock ROM support. The PDroid family is open source.
LBE Privacy Guard revokes permissions, which will make some applications unusable. LBE Privacy Guard also features malware protecting and data traffic control. Some consider the closed source code of Chinese origin as a problem.
The members of the PDroid family and XPrivacy hardly use memory, but LBE Privacy Guard does.
The CyanogenMod Incognito Mode seems not to be fine grained and provides only privacy for personal data, if the associated content provider chooses to do so.
The Per App Settings Module revokes permissions like LBE Privacy Guard does. This modules offers a lot of other, interesting features.
Android 4.3+ Permission Manager is like CyanogenMod Incognito Mode.
XPrivacy can restrict more data than any of the above solutions, also for closed source applications and libraries, like Google Play services.
- Manage Individual App Permissions with XPrivacy (June 20, 2013)
- XPrivacy Gives You Massive Control Over What Your Installed Apps Are Allowed To Do (June 23, 2013)
- Protect Your Privacy with XPrivacy - XDA Developer TV (July 17, 2013)
- XPrivacy Android - Schutz gegen Datensammler (August 1, 2013)
- Black Duck Announces Open Source Rookies of the Year Winners (January 28, 2014)
- The Open Source Rookies of the Year Awards (January 28, 2014)
Translations:
- Translate the strings in this file
- Omit lines with translatable="false"
- If you know how to, please create a pull request
- Else send me the translated file via XDA PM
Current translations:
- Bulgarian (bg)
- Catalan (ca)
- Czech (cs)
- Danish (da)
- Dutch/Flemish (nl)
- English
- Estonian (ee)
- Farsi (fa)
- Finnish (fi)
- French (fr)
- German (de)
- Greek (el)
- Hebrew (he/iw)
- Hindi (hi)
- Hungarian (hu)
- Irish (ga)
- Italian (it)
- Japanese (ja)
- Lithuanian (lt)
- Norwegian (nb-rNO, nn-rNO, no-rNO)
- Polish (pl)
- Portuguese (pt)
- Romanian (ro)
- Rusian (ru)
- Serbian (sr)
- Simplified Chinese (zh-rCN)
- Slovak (sk)
- Slovenian (sl)
- Spanish (es)
- Swedish (sv)
- Tagalog (tl-PH)
- Traditional Chinese (zh-rTW)
- Turkish (tr)
- Ukrainian (ua)
- Vietnamese (vi)
Restrict new data:
- Find the package/class/method that exposes the data (look into the Android documentation/sources)
- Create a class that extends XHook
- Hook the method in XPrivacy
- Write a before and/or after method to restrict the data
- Do a pull request if you want to contribute
Using Eclipse:
- Clone the GitHub project to a temporary location
- Import the GitHub project into Eclipse, copy the files
- Close Eclipse and copy the project from the temporary location over the imported project
- Make sure you copy all hidden files
- Add the Xposed library to the build path as described here
- Add the Google Play services library as decribed here
Testing:
Serious contributors do not have to donate for the pro version. New translations are considered as a serious contribution, but translating a few lines of text is not.
GNU General Public License version 3
Copyright (c) 2013-2014 Marcel Bokhorst (M66B)
This file is part of XPrivacy.
XPrivacy is free software: you can redistribute it and/or modify it under the terms of the GNU General Public License as published by the Free Software Foundation, either version 3 of the License, or (at your option) any later version.
XPrivacy is distributed in the hope that it will be useful, but WITHOUT ANY WARRANTY; without even the implied warranty of MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU General Public License for more details.
You should have received a copy of the GNU General Public License along with XPrivacy. If not, see http://www.gnu.org/licenses/.