The TOR network's exit nodes are monitored and listed for abuse prevention reasons; this list will be updated hourly. The list is separated into 'last seen' groups. For example, 'torfilter-1d' contains all exit nodes that have been seen in the last 24 hours.
We source our data from https://www.dan.me.uk/tornodes, https://check.torproject.org/torbulkexitlist (a TOR project feed), and from other automated research projects.
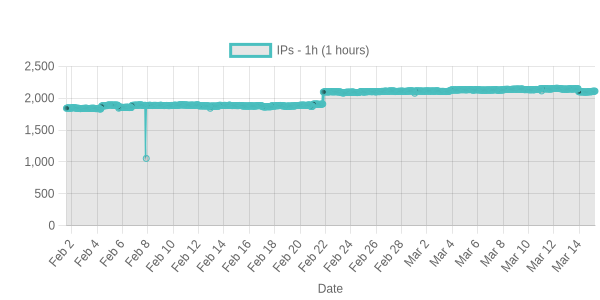
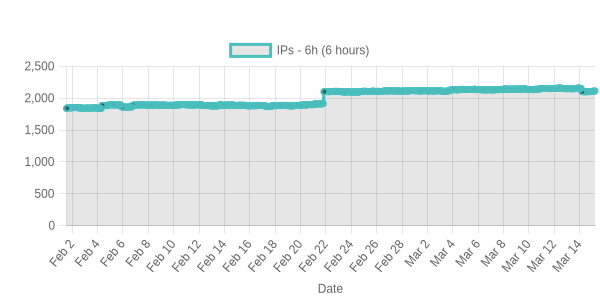
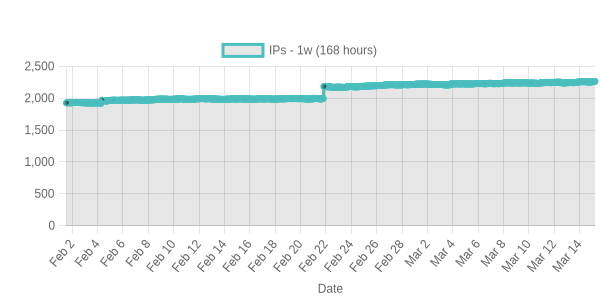
we generate different charts about available data in this repo. For example counts-1h shows the number of IPs updated in the last hour. This means if you took this list as base you can see how many IPs you would have inside.
One IP (IPv4 or IPv6) per line. (current)
...coming soon...
IPv6 especially enables exit nodes to randomize outgoing IP addresses within the large subnets available to them. Since TOR does not expose those CIDRs, it's challenging to identify the networks available to TOR exit nodes.
Flat list of IP addresses. For example:
Markdown version of same IP addresses list. For example:
This format has more details about ip addresses:
....
{
"ip": "23.....100",
"ipversion": 4,
"firstseen": 1648437978,
"lastseen": 1710594950,
"countrycode": "..",
"continentcode": "SA",
"city": "N....",
"ASN": 2x0xx,
"rdns": "tor-exit....."
},
...Disclaimer: We are not responsible for any damage caused by the use of this list. Use it at your own risk. We do not recommend outright banning based on this list alone. Instead, you may want to use this list to help classify incoming requests, packets, or registrations in your services.