diff --git a/app/dcs/access/page.md b/app/dcs/access/page.md
index 1dd4d713e..096bff475 100644
--- a/app/dcs/access/page.md
+++ b/app/dcs/access/page.md
@@ -17,7 +17,7 @@ An Access Grant is a security envelope that contains a satellite address, a rest
Learn more about [](docId:bNywu7-9KLjYfk5LBQABx) and [](docId:XKib9SzjtEXTXWvdyYWX6) or check out the [](docId:4qPQxa8HlvDIO1Kgqa2No) and [](docId:DUfoyppOZA756jGFgj9qw).
{% /callout %}
-The Access Grant screen allows you to create or delete Access Grants, generate credentials for the Storj DCS S3-compatible Gateway from an Access Grant, create an API key to generate an access grant in the CLI.
+The Access Grant screen allows you to create or delete Access Grants, generate credentials for the Storj S3-compatible Gateway from an Access Grant, create an API key to generate an access grant in the CLI.
---
@@ -116,7 +116,7 @@ Then confirm that you want to delete the Access Grant by typing its name and con
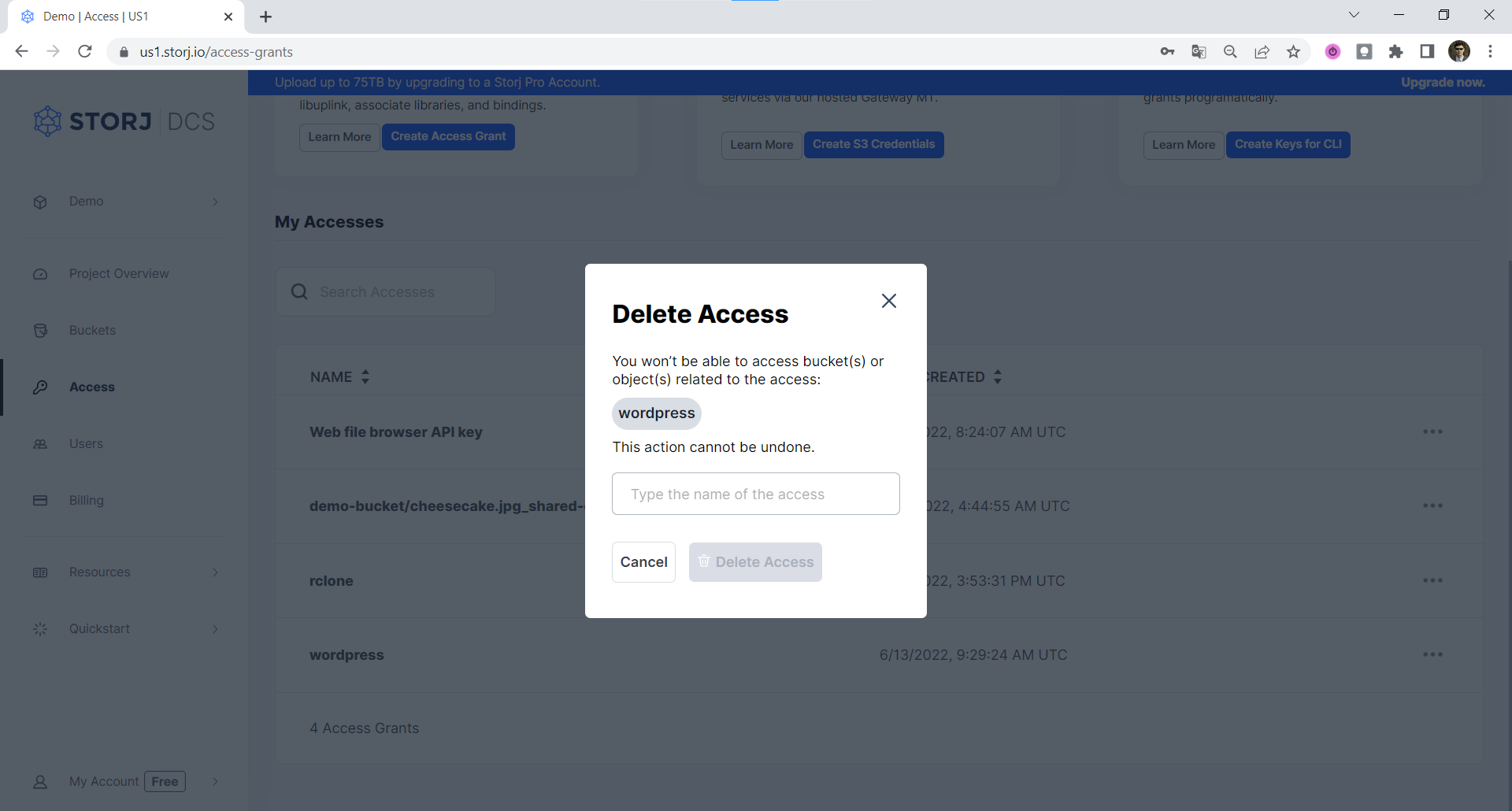
{% callout type="danger" %}
-**Important:** If you delete an Access Grant from the Satellite user interface, that Access Grant will immediately cease to function, and all hierarchically derived child Access Grants and Storj DCS gateway access credentials based on that Access Grant will also cease to function. Any data uploaded with that Access Grant will persist on Storj DCS. If you didn't back up the Encryption Passphrase used with the Access Grant you are deleting, you will not be able to decrypt that data without that Encryption Passphrase, and it will be effectively unrecoverable.
+**Important:** If you delete an Access Grant from the Satellite user interface, that Access Grant will immediately cease to function, and all hierarchically derived child Access Grants and Storj gateway access credentials based on that Access Grant will also cease to function. Any data uploaded with that Access Grant will persist on Storj. If you didn't back up the Encryption Passphrase used with the Access Grant you are deleting, you will not be able to decrypt that data without that Encryption Passphrase, and it will be effectively unrecoverable.
{% /callout %}
You don't need to know everything in the whitepaper about our Access Grants, macaroon-based API Keys or our encryption implementation, but if you understand the general principles, you'll find these are some very sophisticated (but easy to use) tools for creating more secure and private applications.
diff --git a/app/dcs/api/s3/multipart-upload/multipart-part-size/page.md b/app/dcs/api/s3/multipart-upload/multipart-part-size/page.md
index fde7be60f..077fd953e 100644
--- a/app/dcs/api/s3/multipart-upload/multipart-part-size/page.md
+++ b/app/dcs/api/s3/multipart-upload/multipart-part-size/page.md
@@ -10,10 +10,10 @@ metadata:
performance and control costs. Recommended size is 64MB.
---
-The site of the Multipart Parts your application uploads can impact the performance and potentially the cost of your storage on Storj DCS.
+The site of the Multipart Parts your application uploads can impact the performance and potentially the cost of your storage on Storj.
{% callout type="info" %}
-For best performance and cost with Storj DCS, you should plan to configure your AWS S3 client library to use a larger part size than standard. Not doing so could result in much higher fees.
+For best performance and cost with Storj, you should plan to configure your AWS S3 client library to use a larger part size than standard. Not doing so could result in much higher fees.
We recommend 64MB.
{% /callout %}
@@ -22,13 +22,13 @@ We recommend 64MB.
When an object is uploaded using Multipart Upload, a file is first broken into parts, each part of a Multipart Upload is also stored as one or more Segments. With Multipart Upload, a single object is uploaded as a set of parts.
-The ideal part size for large files is 64MB, so that there is one Segment per part. Using a smaller Part size will result in a significant increase in the number of segments stored on Storj DCS. At large scale, this could impact both the performance and cost of your storage.
+The ideal part size for large files is 64MB, so that there is one Segment per part. Using a smaller Part size will result in a significant increase in the number of segments stored on Storj. At large scale, this could impact both the performance and cost of your storage.
Learn more about [](docId:A4kUGYhfgGbVhlQ2ZHXVS).
Each part is an integral portion of the data comprising the object. The object parts may be uploaded independently, in parallel, and in any order. Uploads may be paused and resumed by uploading an initial set of parts, then resuming and uploading the remaining parts. If the upload of any part fails, that part may be re-uploaded without impacting the upload of other parts.
-All of these parts are broken into one or more Segments by the Storj DCS Gateway based on whether the Part Size is smaller or larger than the default Segment size. While Multipart Upload is most appropriate for files larger than the 64MB default Segment size, the Part Size is configurable in applications that use Multipart Upload.
+All of these parts are broken into one or more Segments by the Storj Gateway based on whether the Part Size is smaller or larger than the default Segment size. While Multipart Upload is most appropriate for files larger than the 64MB default Segment size, the Part Size is configurable in applications that use Multipart Upload.
### Configuration for the AWS CLI
diff --git a/app/dcs/api/s3/multipart-upload/page.md b/app/dcs/api/s3/multipart-upload/page.md
index 5ff23c122..9d3c085e7 100644
--- a/app/dcs/api/s3/multipart-upload/page.md
+++ b/app/dcs/api/s3/multipart-upload/page.md
@@ -10,13 +10,13 @@ metadata:
file uploads on the globally distributed, S3-compatible gateway.
---
-Understanding how to use Multipart Upload with the Storj DCS globally distributed, multi-region cloud-hosted S3-compatible gateway
+Understanding how to use Multipart Upload with the Storj globally distributed, multi-region cloud-hosted S3-compatible gateway
Multipart Upload is a function that allows large files to be broken up into smaller pieces for more efficient uploads. When an object is uploaded using Multipart Upload, a file is first broken into parts, each part of a Multipart Upload is also stored as one or more Segments. With Multipart Upload, a single object is uploaded as a set of parts.
Each part is an integral portion of the data comprising the object. The object parts may be uploaded independently, in parallel, and in any order. Uploads may be paused and resumed by uploading an initial set of parts, then resuming and uploading the remaining parts. If the upload of any part fails, that part may be re-uploaded without impacting the upload of other parts.
-All of these parts are broken into one or more Segments by the Storj DCS Gateway based on whether the Part Size is smaller or larger than the default Segment size. While Multipart Upload is most appropriate for files larger than the 64MB default Segment size, the Part Size is configurable in applications that use Multipart Upload.
+All of these parts are broken into one or more Segments by the Storj Gateway based on whether the Part Size is smaller or larger than the default Segment size. While Multipart Upload is most appropriate for files larger than the 64MB default Segment size, the Part Size is configurable in applications that use Multipart Upload.
## Using Multipart Upload
@@ -32,23 +32,23 @@ Multipart upload takes a single object and divides it into encapsulated pieces t
## Workflow for Multipart upload
-As described below, mutlipart upload is a process consisting of: starting the upload, transferring each piece, and finally completing the multipart upload. Upon successful upload of the final piece, Storj DCS will logically reassemble the object, apply metadata and make the object accessible. During the multipart upload operation, you can get status of active upload operations and get lists of parts you have uploaded. More detail on multipart operations is provided in the sections below.
+As described below, mutlipart upload is a process consisting of: starting the upload, transferring each piece, and finally completing the multipart upload. Upon successful upload of the final piece, Storj will logically reassemble the object, apply metadata and make the object accessible. During the multipart upload operation, you can get status of active upload operations and get lists of parts you have uploaded. More detail on multipart operations is provided in the sections below.
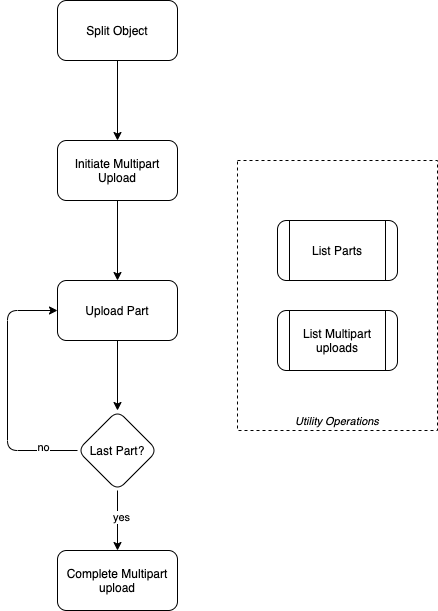
## Initiate Multipart upload
-At the start of a multipart upload, Storj DCS will return an ID that you use to reference your multipart upload; you need to include this ID when working with the object. Operations such as uploading parts, listing parts and canceling the multipart operation.
+At the start of a multipart upload, Storj will return an ID that you use to reference your multipart upload; you need to include this ID when working with the object. Operations such as uploading parts, listing parts and canceling the multipart operation.
### Upload Part
-While uploading an object part you need to specify the ID received when you created the multipart upload along with a unique part number that your specific call will be sending to the platform. Because of the capability of multipart upload to work non sequentially, you can upload any part at any time before the multipart upload is completed. Additionally, you can over right existing parts numbers you've previously transferred as long as the multipart upload has not been completed. Part numbers are chosen by the client and are between 1 and 2^31. When a part is uploaded, the Storj DCS platform will return several items, one of which is an ETag. To complete the multipart upload process you will need to provide a list of part IDs and their corresponding ETags.
+While uploading an object part you need to specify the ID received when you created the multipart upload along with a unique part number that your specific call will be sending to the platform. Because of the capability of multipart upload to work non sequentially, you can upload any part at any time before the multipart upload is completed. Additionally, you can over right existing parts numbers you've previously transferred as long as the multipart upload has not been completed. Part numbers are chosen by the client and are between 1 and 2^31. When a part is uploaded, the Storj platform will return several items, one of which is an ETag. To complete the multipart upload process you will need to provide a list of part IDs and their corresponding ETags.
-Be advised that billing occurs when data is stored on the Storj DCS platform - as such - when you initiate a multipart upload and begin uploading parts, charges will be applied based on the amount of space the parts occupy. Billing will occur regardless of a multipart upload being completed.
+Be advised that billing occurs when data is stored on the Storj platform - as such - when you initiate a multipart upload and begin uploading parts, charges will be applied based on the amount of space the parts occupy. Billing will occur regardless of a multipart upload being completed.
### Completing a multipart upload
-When you upload the final part of a multipart upload you need to call the complete operation to tell Storj DCS to reconstitute the object from the individual parts you have uploaded. When the complete operation concludes all metadata and individual parts will be consolidated into a single object.
+When you upload the final part of a multipart upload you need to call the complete operation to tell Storj to reconstitute the object from the individual parts you have uploaded. When the complete operation concludes all metadata and individual parts will be consolidated into a single object.
To call the complete operation you need to provide the list of ETags and their corresponding part IDs. You should maintain this list in your application.
@@ -56,7 +56,7 @@ If you decide to cancel the multipart operation, you must provide the object key
### Listing for multipart uploads
-During a multipart upload you can list active upload transactions or the parts that have been successfully uploaded. For a single list parts request, storage DCS will return information up to a maximum of 1000 parts. For objects with more than 1000 parts, multiple requests are required. Because of the distributed nature of Storj DCS, you should not use the response from listing multipart uploads as input to complete in multipart upload operation. Be advised that part listing requests will only return completed part uploads - any active part uploads will not be returned.
+During a multipart upload you can list active upload transactions or the parts that have been successfully uploaded. For a single list parts request, storage DCS will return information up to a maximum of 1000 parts. For objects with more than 1000 parts, multiple requests are required. Because of the distributed nature of Storj, you should not use the response from listing multipart uploads as input to complete in multipart upload operation. Be advised that part listing requests will only return completed part uploads - any active part uploads will not be returned.
## Multipart upload for distributed systems
@@ -64,7 +64,7 @@ Depending on the behavior of your application it may be possible for multiple co
## Cost for Multipart upload
-When a multipart upload is initiated, storage DCS processes and makes available all constituent parts of the multipart object. Multipart object is either made available by completing the multipart upload process or cancelled by explicitly stopping the multipart upload process through API call. Storj DCS will measure resource usage on multipart upload operations unless they are explicitly cancelled. only when a multipart upload is explicitly cancelled are the associated resources freed.
+When a multipart upload is initiated, storage DCS processes and makes available all constituent parts of the multipart object. Multipart object is either made available by completing the multipart upload process or cancelled by explicitly stopping the multipart upload process through API call. Storj will measure resource usage on multipart upload operations unless they are explicitly cancelled. only when a multipart upload is explicitly cancelled are the associated resources freed.
## Multipart upload limits
diff --git a/app/dcs/api/s3/presigned-urls/page.md b/app/dcs/api/s3/presigned-urls/page.md
index 68e54dbcd..45b299454 100644
--- a/app/dcs/api/s3/presigned-urls/page.md
+++ b/app/dcs/api/s3/presigned-urls/page.md
@@ -12,7 +12,7 @@ metadata:
## Introduction
-Creating presigned URLs for Storj DCS - HTTP POST & GET to a URL
+Creating presigned URLs for Storj - HTTP POST & GET to a URL
All objects and paths are private and encrypted by default. However, it is possible to use a pre-signed URL via our S3-compatible gateway to enable unauthenticated customers/users to upload objects to buckets or access objects in buckets without providing an [](docId:XKib9SzjtEXTXWvdyYWX6) or [](docId:AsyYcUJFbO1JI8-Tu8tW3).
diff --git a/app/dcs/api/s3/s3-compatible-gateway/page.md b/app/dcs/api/s3/s3-compatible-gateway/page.md
index 7b0abfdc4..f41620644 100644
--- a/app/dcs/api/s3/s3-compatible-gateway/page.md
+++ b/app/dcs/api/s3/s3-compatible-gateway/page.md
@@ -13,7 +13,7 @@ metadata:
instructions on how to get started with it.
---
-The Storj DCS globally distributed, multi-region cloud-hosted S3-compatible gateway
+The Storj globally distributed, multi-region cloud-hosted S3-compatible gateway
## S3 compatibility
diff --git a/app/dcs/api/sdk/page.md b/app/dcs/api/sdk/page.md
index 4016358bf..aa9a30dc7 100644
--- a/app/dcs/api/sdk/page.md
+++ b/app/dcs/api/sdk/page.md
@@ -11,7 +11,7 @@ The `libuplink` developer library is written for the Go language. This will allo
`libuplink` contains a number of interesting components, including pre-written code and subroutines, classes, values or type specifications, message templates, configuration walkthroughs, and great documentation.
-Storj DCS currently has community contributed bindings for Python, Swift, .Net, PHP, and Node.js.
+Storj currently has community contributed bindings for Python, Swift, .Net, PHP, and Node.js.
Below are Storj's provided bindings:
diff --git a/app/dcs/api/storj-ipfs-pinning/page.md b/app/dcs/api/storj-ipfs-pinning/page.md
index 0707b6c8b..6b33377aa 100644
--- a/app/dcs/api/storj-ipfs-pinning/page.md
+++ b/app/dcs/api/storj-ipfs-pinning/page.md
@@ -26,7 +26,7 @@ Uploading content follows the [IPFS HTTP RPC for /api/v0/add](https://docs.ipfs.
2. You must specify the credentials given when invited to participate in the beta as _HTTP basic authentication._
{% callout type="warning" %}
-**_This is not the same as your Storj DCS username and password. Do not use your Storj DCS username and password to try and use the IPFS Pinning Service._**
+**_This is not the same as your Storj username and password. Do not use your Storj username and password to try and use the IPFS Pinning Service._**
{% /callout %}
### Example for pinning a single file using cURL
@@ -288,7 +288,7 @@ For those applications that do not support IPFS natively, you can use any [publi
### HTTP via Storj IPFS Gateway
-For best performance, we have provided a Storj IPFS Gateway. This gateway will only host content pinned to Storj DCS, so it is not like other public IPFS gateways.
+For best performance, we have provided a Storj IPFS Gateway. This gateway will only host content pinned to Storj, so it is not like other public IPFS gateways.
You can construct a link like this:
@@ -351,7 +351,7 @@ Listing pinned content follows the [IPFS HTTP RPC for /api/v0/pin/ls](https://do
2. You must specify the credentials given when invited to participate in the beta as _HTTP basic authentication._
{% callout type="warning" %}
-**_This is not the same as your Storj DCS username and password. Do not use your Storj DCS username and password to try and use the IPFS Pinning Service._**
+**_This is not the same as your Storj username and password. Do not use your Storj username and password to try and use the IPFS Pinning Service._**
{% /callout %}
### Example for listing pins using cURL
@@ -371,7 +371,7 @@ Unpinning content follows the [IPFS HTTP RPC for /api/v0/pin/rm](https://docs.ip
2. You must specify the credentials given when invited to participate in the beta as _HTTP basic authentication._
{% callout type="warning" %}
-**_This is not the same as your Storj DCS username and password. Do not use your Storj DCS username and password to try and use the IPFS Pinning Service._**
+**_This is not the same as your Storj username and password. Do not use your Storj username and password to try and use the IPFS Pinning Service._**
{% /callout %}
{% callout type="info" %}
@@ -409,7 +409,7 @@ Importing CAR content follows the [IPFS HTTP RPC for /api/v0/dag/import](https:/
2. You must specify the credentials given when invited to participate in the beta as _HTTP basic authentication._
{% callout type="warning" %}
-**_This is not the same as your Storj DCS username and password. Do not use your Storj DCS username and password to try and use the IPFS Pinning Service._**
+**_This is not the same as your Storj username and password. Do not use your Storj username and password to try and use the IPFS Pinning Service._**
{% /callout %}
### Example for pinning a single file using cURL
diff --git a/app/dcs/api/uplink-cli/cp-command/page.md b/app/dcs/api/uplink-cli/cp-command/page.md
index 96625ce1a..97ad6621c 100644
--- a/app/dcs/api/uplink-cli/cp-command/page.md
+++ b/app/dcs/api/uplink-cli/cp-command/page.md
@@ -5,7 +5,7 @@ redirects:
- /dcs/api-reference/uplink-cli/cp-command
---
-Copies a local file or Storj object to another location locally or in Storj DCS
+Copies a local file or Storj object to another location locally or in Storj
## Usage
@@ -46,7 +46,7 @@ The `cp` command is used to upload and download objects. The `cp` command abstra
## Copy a local file into an existing bucket
-When the `cp` command is used to copy a file to Storj DCS (upload), the CLI first encrypts the file client-side, then splits it into a minimum of x erasure-coded pieces, and finally, the x pieces are uploaded in parallel to x different storage nodes. x currently equals 80 but is subject to change depending on continuous optimization.
+When the `cp` command is used to copy a file to Storj (upload), the CLI first encrypts the file client-side, then splits it into a minimum of x erasure-coded pieces, and finally, the x pieces are uploaded in parallel to x different storage nodes. x currently equals 80 but is subject to change depending on continuous optimization.
To copy `cheesecake.jpg` into the existing bucket `cakes`, use the following command:
@@ -76,7 +76,7 @@ Output:
### Copy a file from a bucket to a local drive
-When the `cp` command is used to copy a file from Storj DCS (download), the CLI first downloads the minimum number of pieces to reconstitute a file (typically 29 pieces), then re-encodes the pieces into a single file, and finally decrypts the file client-side.
+When the `cp` command is used to copy a file from Storj (download), the CLI first downloads the minimum number of pieces to reconstitute a file (typically 29 pieces), then re-encodes the pieces into a single file, and finally decrypts the file client-side.
To copy a file from a project to a local drive, use:
@@ -179,11 +179,11 @@ upload /home/user/receipts/cheescake.jpg to sj://cakes/cheescake.jpg
upload /home/user/receipts/pancake.jpg to sj://cakes/pancake.jpg
```
-### Copy an object from one location to another within Storj DCS
+### Copy an object from one location to another within Storj
-It is possible to copy a file from one Storj DCS location to another Storj DCS location within the same project.
+It is possible to copy a file from one Storj location to another Storj location within the same project.
-When the `cp` command is used to copy a file from one Storj DCS location to another Storj DCS location, the object will be copied entirely on the "server" side - **this will not count against your egress limits, as the object is not being downloaded**.
+When the `cp` command is used to copy a file from one Storj location to another Storj location, the object will be copied entirely on the "server" side - **this will not count against your egress limits, as the object is not being downloaded**.
{% callout type="info" %}
You need to have at least version 1.54.1 of Uplink installed to support server-side copy
@@ -239,4 +239,4 @@ Sample Output:
upload sj://cakes/cheesecake.jpg sj://new-recipes/cakes/cheesecake.jpg
```
-There is no progress bar shown since nothing was downloaded or uploaded, as the copying happens on the "server" side (within a Storj DCS project.)
+There is no progress bar shown since nothing was downloaded or uploaded, as the copying happens on the "server" side (within a Storj project.)
diff --git a/app/dcs/api/uplink-cli/installation/page.md b/app/dcs/api/uplink-cli/installation/page.md
index f18a620ea..fd74a84cb 100644
--- a/app/dcs/api/uplink-cli/installation/page.md
+++ b/app/dcs/api/uplink-cli/installation/page.md
@@ -8,7 +8,7 @@ metadata:
title: Download and install uplink
---
-The native CLI tool for Storj DCS/OSP
+The native CLI tool for Storj
First, [](docId:HeEf9wiMdlQx9ZdS_-oZS).
diff --git a/app/dcs/api/uplink-cli/mv/page.md b/app/dcs/api/uplink-cli/mv/page.md
index 68da177c8..49cedd623 100644
--- a/app/dcs/api/uplink-cli/mv/page.md
+++ b/app/dcs/api/uplink-cli/mv/page.md
@@ -5,7 +5,7 @@ redirects:
- /dcs/api-reference/uplink-cli/mv
---
-Moves a Storj object to another location in Storj DCS
+Moves a Storj object to another location in Storj
## Usage
@@ -25,7 +25,7 @@ uplink mv SOURCE DESTINATION [flags]
{% /code-group %}
-The `mv` command is used to move or rename objects within the same Storj DCS project. The `mv` command uses a server-side move (rename) method, it does not incur a fee for downloading and will be performed with no delay.
+The `mv` command is used to move or rename objects within the same Storj project. The `mv` command uses a server-side move (rename) method, it does not incur a fee for downloading and will be performed with no delay.
## Flags
@@ -50,7 +50,7 @@ The `mv` command is used to move or rename objects within the same Storj DCS pro
### Move an object within an existing bucket
-When the `mv` command is used to move a file within Storj DCS, the CLI will move (rename) the object using the server-side method to rename the object.
+When the `mv` command is used to move a file within Storj, the CLI will move (rename) the object using the server-side method to rename the object.
To move `cheesecake.jpg` within the existing bucket `cakes`, use the following command:
@@ -80,7 +80,7 @@ Sample Output:
### Move an object from a one bucket to another
-When the `mv` command is used to move an object from one Storj DCS bucket to another Storj DCS bucket, the CLI will use a server-side move method.
+When the `mv` command is used to move an object from one Storj bucket to another Storj bucket, the CLI will use a server-side move method.
To create a new bucket, we will use the `mb` command, as a move is possible only to an existing bucket.
diff --git a/app/dcs/api/uplink-cli/page.md b/app/dcs/api/uplink-cli/page.md
index cef02f042..db5a65a15 100644
--- a/app/dcs/api/uplink-cli/page.md
+++ b/app/dcs/api/uplink-cli/page.md
@@ -29,7 +29,7 @@ The `uplink` command can take the following child commands:
| [](docId:Df-CVmCCHmt6r3_c1PLn4) | list objects and prefixes or all buckets |
| [](docId:F77kaGpjXx7w-JYv2rkhf) | make a new bucket |
| [](docId:kyMG3B16kKc3gpCxRNe1K) | metadata related commands |
-| [](docId:PIfV271UghKvJecT-zQ4d) | moves a Storj object to another location in Storj DCS |
+| [](docId:PIfV271UghKvJecT-zQ4d) | moves a Storj object to another location in Storj |
| [](docId:Wo5-shT0hZDNMeyM1kA12) | remove a bucket |
| [](docId:eavv_906IH-39ylIXq30d) | remove a file from a Storj bucket |
| [](docId:OuoKJl9KqbJVQB9Xkdy3g) | create an uplink config file |
diff --git a/app/dcs/code/partner-program-tools/page.md b/app/dcs/code/partner-program-tools/page.md
index 8943adde2..b18212e30 100644
--- a/app/dcs/code/partner-program-tools/page.md
+++ b/app/dcs/code/partner-program-tools/page.md
@@ -17,9 +17,9 @@ How to configure the User agent for partner value attribution from commandline,
## Partner Program
-The Storj Partner Ecosystem enables developers to build Storj DCS Connectors, which their customers can use to store data on Storj DSC.
+The Storj Partner Ecosystem enables developers to build Storj Connectors, which their customers can use to store data on Storj.
-The data itself is client-side encrypted, however we are able to measure the aggregate volume of storage and bandwidth usage. When a user of a Storj DCS Connector stores data in a bucket, we are able to give the partner attribution for the stored data and the used bandwidth for the Connector Integration, and provide programmatic revenue share.
+The data itself is client-side encrypted, however we are able to measure the aggregate volume of storage and bandwidth usage. When a user of a Storj Connector stores data in a bucket, we are able to give the partner attribution for the stored data and the used bandwidth for the Connector Integration, and provide programmatic revenue share.
You can learn more about our partner program [here](https://www.storj.io/partners/).
diff --git a/app/dcs/code/static-site-hosting/page.md b/app/dcs/code/static-site-hosting/page.md
index 7a3f6ea2c..9fdc1ebc1 100644
--- a/app/dcs/code/static-site-hosting/page.md
+++ b/app/dcs/code/static-site-hosting/page.md
@@ -19,7 +19,7 @@ You can use your own domain name and host your own static website on Storj
## Part 1: Uplink CLI
-1. Download the uplink binary ([](docId:h3RyJymEIi4gf2S9wVJg8)) and upload your static site files to Storj DCS. You may also upload your files in any other manner, but you will need the Uplink CLI for the remaining steps.
+1. Download the uplink binary ([](docId:h3RyJymEIi4gf2S9wVJg8)) and upload your static site files to Storj. You may also upload your files in any other manner, but you will need the Uplink CLI for the remaining steps.
2. Share the bucket or object prefix (not individual objects) that will be the root of your website/subdomain. At the root, name your home page `index.html`. The website will serve the index.html file automatically e.g. `http://www.example.test` and `http://www.example.test/index.html` will serve the same content. Anything shared with `--dns` will be _readonly_ and available _publicly_ (no secret key needed).
3. Finally, you can optionally add the `--tls` flag in order to return an additional DNS entry used for securing your domain with TLS.
diff --git a/app/dcs/pricing/page.md b/app/dcs/pricing/page.md
index 4ffb5122b..49a876a25 100644
--- a/app/dcs/pricing/page.md
+++ b/app/dcs/pricing/page.md
@@ -30,7 +30,7 @@ The following section describes how the charges listed in the table above are ca
## Object Storage
-Object storage is priced per GB per month in increments of byte hours. The calculation of object storage fees is based on a standard 720-hour month. Actual storage is metered in bytes uploaded. Bytes uploaded include the bytes associated with actual objects plus any nominal overhead associated with encryption. Byte hours are calculated based on the number of hours bytes are stored on the Storj DCS Platform from when an object is uploaded to when it is deleted. The calculated number of bytes is then multiplied by the byte hour price. The byte hour price is derived from the GB month price divided by the standard 720-hour month and base 10 conversion of GB to bytes.
+Object storage is priced per GB per month in increments of byte hours. The calculation of object storage fees is based on a standard 720-hour month. Actual storage is metered in bytes uploaded. Bytes uploaded include the bytes associated with actual objects plus any nominal overhead associated with encryption. Byte hours are calculated based on the number of hours bytes are stored on the Storj Platform from when an object is uploaded to when it is deleted. The calculated number of bytes is then multiplied by the byte hour price. The byte hour price is derived from the GB month price divided by the standard 720-hour month and base 10 conversion of GB to bytes.
**Example**
@@ -46,7 +46,7 @@ When an object is downloaded, there are a number of factors that can impact the
A user downloads one 1 TB file. Based on the long tail elimination, up to 1.3 TB of download bandwidth may be used. The 1.3 TB of download bandwidth is accounted for as 1,300,000,000 bytes. In this example, the price per GB is $0.007 and per byte is $0.000000045. The total amount charged for the egress is $9.10.
-Unlike other cloud object storage vendors, we don't use high egress fees to create vendor lock-in. If you discover that Storj DCS isn't a fit for your project or application and you transfer your data to another service, use our support portal to submit a ticket and let us know. As long as you follow the process, we won't charge you for that egress bandwidth.
+Unlike other cloud object storage vendors, we don't use high egress fees to create vendor lock-in. If you discover that Storj isn't a fit for your project or application and you transfer your data to another service, use our support portal to submit a ticket and let us know. As long as you follow the process, we won't charge you for that egress bandwidth.
## Per Segment Fee
@@ -56,13 +56,13 @@ Each Segment stored on the network in excess of the default Segment Project Limi
The Paid Tier includes 50,000 Segments per month, which is represented as 36,000,000 Segment Hours. Any increase in Segment Limit will be billed at a rate of $0.0000088 per Segment per month, equivalent to a rate of $0.00000001222 per Segment Hour.
-The Storj DCS Platform distinguishes between two types of object storage: remote and inline. Remote objects are large enough to erasure code and store the pieces of the file on storage nodes. Inline objects are smaller than the metadata associated with the actual object. In the case of objects that are smaller than the associated metadata, it is more efficient to store the object inline in the satellite metadata database. When storing a large number of tiny files, the best practice is to employ a packing strategy to store larger blocks of small files as a single object.
+The Storj Platform distinguishes between two types of object storage: remote and inline. Remote objects are large enough to erasure code and store the pieces of the file on storage nodes. Inline objects are smaller than the metadata associated with the actual object. In the case of objects that are smaller than the associated metadata, it is more efficient to store the object inline in the satellite metadata database. When storing a large number of tiny files, the best practice is to employ a packing strategy to store larger blocks of small files as a single object.
-The Per Segment Fee is priced per Segment per month in increments of Segment hours. The calculation of per segment fees is based on a standard 720-hour month. Actual Per Segment Fees are metered in Segments uploaded. Per Segment Fee hours are calculated based on the number of hours Segments are stored on the Storj DCS Platform from when a Segment is uploaded to when it is deleted. The number of hours each Segment is stored on the platform during the month then is multiplied by the Segment hour price. The segment hour price is derived from the Segment month price divided by the standard 720-hour month.
+The Per Segment Fee is priced per Segment per month in increments of Segment hours. The calculation of per segment fees is based on a standard 720-hour month. Actual Per Segment Fees are metered in Segments uploaded. Per Segment Fee hours are calculated based on the number of hours Segments are stored on the Storj Platform from when a Segment is uploaded to when it is deleted. The number of hours each Segment is stored on the platform during the month then is multiplied by the Segment hour price. The segment hour price is derived from the Segment month price divided by the standard 720-hour month.
-As described elsewhere in this documentation, objects stored on Storj DCS are encrypted and erasure coded, with the encrypted, erasure coded pieces stored on various Storage Nodes on the distributed and decentralized network. Each object stored on the network is represented as at least one Segment.
+As described elsewhere in this documentation, objects stored on Storj are encrypted and erasure coded, with the encrypted, erasure coded pieces stored on various Storage Nodes on the distributed and decentralized network. Each object stored on the network is represented as at least one Segment.
-A Segment is a single array of bytes, between 0 and a user-configurable maximum segment size. The default Segment size on Storj DCS Satellites is 64MB. A File smaller than 64MB is stored as one segment. Files larger than 64MB are stored in multiple 64MB Segments. Each Segment is stored as pieces on the network. Only a subset of pieces of the total pieces (e.g. 29 of the 80) are required to reconstitute a Segment . All Segments are required to reconstitute a File.
+A Segment is a single array of bytes, between 0 and a user-configurable maximum segment size. The default Segment size on Storj Satellites is 64MB. A File smaller than 64MB is stored as one segment. Files larger than 64MB are stored in multiple 64MB Segments. Each Segment is stored as pieces on the network. Only a subset of pieces of the total pieces (e.g. 29 of the 80) are required to reconstitute a Segment . All Segments are required to reconstitute a File.
**Examples:**
@@ -94,7 +94,7 @@ Note that the number of segments for 100TB of 1GB files and 1.6TB of 1MB files i
## Multipart Upload Impact on Segments
-When an object is uploaded using Multipart Upload, a file is first broken into parts, each part of a Multipart Upload is also stored as one or more Segments. With Multipart Upload, a single object is uploaded as a set of parts. Each part is an integral portion of the data comprising the object. The object parts may be uploaded independently, in parallel, and in any order. Uploads may be paused and resumed by uploading an initial set of parts, then resuming and uploading the remaining parts. If the upload of any part fails, that part may be re-uploaded without impacting the upload of other parts. All of these parts are broken into one or more Segments by the Storj DCS Gateway based on whether the Part Size is smaller or larger than the default Segment size. While Multipart Upload is most appropriate for files larger than the 64MB default Segment size, the Part Size is configurable in applications that use Multipart Upload.
+When an object is uploaded using Multipart Upload, a file is first broken into parts, each part of a Multipart Upload is also stored as one or more Segments. With Multipart Upload, a single object is uploaded as a set of parts. Each part is an integral portion of the data comprising the object. The object parts may be uploaded independently, in parallel, and in any order. Uploads may be paused and resumed by uploading an initial set of parts, then resuming and uploading the remaining parts. If the upload of any part fails, that part may be re-uploaded without impacting the upload of other parts. All of these parts are broken into one or more Segments by the Storj Gateway based on whether the Part Size is smaller or larger than the default Segment size. While Multipart Upload is most appropriate for files larger than the 64MB default Segment size, the Part Size is configurable in applications that use Multipart Upload.
**Examples:**
@@ -102,7 +102,7 @@ A single 128MB file using a 64MB Part Size is uploaded as 2 parts, with each par
A single 128MB file using a 5MB Part Size is uploaded as 26 Parts (25 5MB Parts and one 3MB Part), with each part stored as one Segment, for a total of 26 Segments.
-The default Part Size for Multipart Upload for some applications is 5MB. The difference between using the default 5MB Part Size instead of the default size of 64MB for Storj DCS is impactful.
+The default Part Size for Multipart Upload for some applications is 5MB. The difference between using the default 5MB Part Size instead of the default size of 64MB for Storj is impactful.
Assuming a 1TB data set comprised of 1,000 1GB files is stored for an entire month, the difference between using 64MB Part Size vs. 5MB Part Size is described below:
@@ -121,11 +121,11 @@ A user uploads 1PB of one GB objects using multipart upload with a 5MB Part Size
## Project limits
-All Projects have Project Limits on certain important constructs. Increases in Project Limits may impact the price of your use of Storj DCS. To learn more, check out the [](docId:Zrbz4XYhIOm99hhRShWHg) and [](docId:A4kUGYhfgGbVhlQ2ZHXVS) sections of this Documentation.
+All Projects have Project Limits on certain important constructs. Increases in Project Limits may impact the price of your use of Storj. To learn more, check out the [](docId:Zrbz4XYhIOm99hhRShWHg) and [](docId:A4kUGYhfgGbVhlQ2ZHXVS) sections of this Documentation.
## Free tier
-Storj DCS currently offers a free level of access for developers to try out the service. When a customer creates a new account, the user automatically is able to use the Storj DCS service at no cost up to specified limits of service. The free level of service is limited to the level of service for a single project as described below:
+Storj currently offers a free level of access for developers to try out the service. When a customer creates a new account, the user automatically is able to use the Storj service at no cost up to specified limits of service. The free level of service is limited to the level of service for a single project as described below:
- 25GB of static object storage for a single project.
diff --git a/app/dcs/third-party-tools/arq/page.md b/app/dcs/third-party-tools/arq/page.md
index e8a109f8e..563f3b0e9 100644
--- a/app/dcs/third-party-tools/arq/page.md
+++ b/app/dcs/third-party-tools/arq/page.md
@@ -73,4 +73,4 @@ Once you have your Storj account you can create a bucket for your data to be sto
-Congratulations, you have successfully configured Arq to back up your data to Storj DCS!
+Congratulations, you have successfully configured Arq to back up your data to Storj!
diff --git a/app/dcs/third-party-tools/chainstate-snapshots/page.md b/app/dcs/third-party-tools/chainstate-snapshots/page.md
index c1d20b1f1..3f4f9a403 100644
--- a/app/dcs/third-party-tools/chainstate-snapshots/page.md
+++ b/app/dcs/third-party-tools/chainstate-snapshots/page.md
@@ -17,7 +17,7 @@ Host snapshots at reduced cost when spinning up new node.
## Create Storj account
-After [creating an account](https://www.storj.io/signup) on Storj DCS, you’ll need to setup the uplink cli.
+After [creating an account](https://www.storj.io/signup) on Storj, you’ll need to setup the uplink cli.
### Setup uplink CLI
@@ -93,7 +93,7 @@ Compress small files/directories to a single compressed file (e.g use `tar`).
tar cf snapshot.tar /path/to/snapshot
```
-Use `uplink cp` to upload your snapshot to Storj DCS. Scale parallelism starting at 4 on powerful servers. Scale up by 2 until throughput no longer improves. You should have at least one cpu core for each parallelism. Parallelism 8 will require 8 cores or 16 threads.
+Use `uplink cp` to upload your snapshot to Storj. Scale parallelism starting at 4 on powerful servers. Scale up by 2 until throughput no longer improves. You should have at least one cpu core for each parallelism. Parallelism 8 will require 8 cores or 16 threads.
```Text
uplink cp --parallelism 4 snapshot.tar sj://snapshots/snapshot.tar
diff --git a/app/dcs/third-party-tools/comet-backup/page.md b/app/dcs/third-party-tools/comet-backup/page.md
index 5acfbf226..c5c0f660e 100644
--- a/app/dcs/third-party-tools/comet-backup/page.md
+++ b/app/dcs/third-party-tools/comet-backup/page.md
@@ -129,7 +129,7 @@ To complete the integration, you will need the credentials (bucket name and pass
-3\. Change the “Type” to Storj DCS and then fill in the fields as described below:
+3\. Change the “Type” to Storj and then fill in the fields as described below:
1. **Description:** What you will call the storage on the Comet Server
diff --git a/app/dcs/third-party-tools/cyberduck/page.md b/app/dcs/third-party-tools/cyberduck/page.md
index 1c5a1e7f9..ffe3b2589 100644
--- a/app/dcs/third-party-tools/cyberduck/page.md
+++ b/app/dcs/third-party-tools/cyberduck/page.md
@@ -14,13 +14,13 @@ metadata:
## Introduction
-Cyberduck is a free, open-source libre server - a small server system that enables you to run your own internet services independently - cloud storage browser for macOS, Windows, and Linux that supports FTP and SFTP, WebDAV, and cloud storage such as **Storj DCS** and other cloud storage providers.
+Cyberduck is a free, open-source libre server - a small server system that enables you to run your own internet services independently - cloud storage browser for macOS, Windows, and Linux that supports FTP and SFTP, WebDAV, and cloud storage such as **Storj** and other cloud storage providers.
Users can leverage the Cyberduck services via the user interface (GUI) or CLI (for Linux), including file transfer by drag and drop and notifications via Growl. It is also able to open some files in external text editors.
-Users can choose **Storj DCS** to act as a decentralized cloud storage network target to send files to via the Cyberduck file manager interface, available via Storj's hosted multitenant gateway ([](docId:AsyYcUJFbO1JI8-Tu8tW3) that is backward compatible with S3. This means you’ll be able to integrate with the Storj network via HTTP, and you won’t have to run anything extra on your end.
+Users can choose **Storj** to act as a decentralized cloud storage network target to send files to via the Cyberduck file manager interface, available via Storj's hosted multitenant gateway ([](docId:AsyYcUJFbO1JI8-Tu8tW3) that is backward compatible with S3. This means you’ll be able to integrate with the Storj network via HTTP, and you won’t have to run anything extra on your end.
-In this brief tutorial, we'll go over downloading and setting up Cyberduck to integrate with Storj DCS, facilitating easy and intuitive drag-and-drop file transfer to Storj DCS.
+In this brief tutorial, we'll go over downloading and setting up Cyberduck to integrate with Storj, facilitating easy and intuitive drag-and-drop file transfer to Storj.
## Downloading Cyberduck
@@ -96,11 +96,11 @@ Once the download is complete, you'll be able to open the CyberDuck client. By s
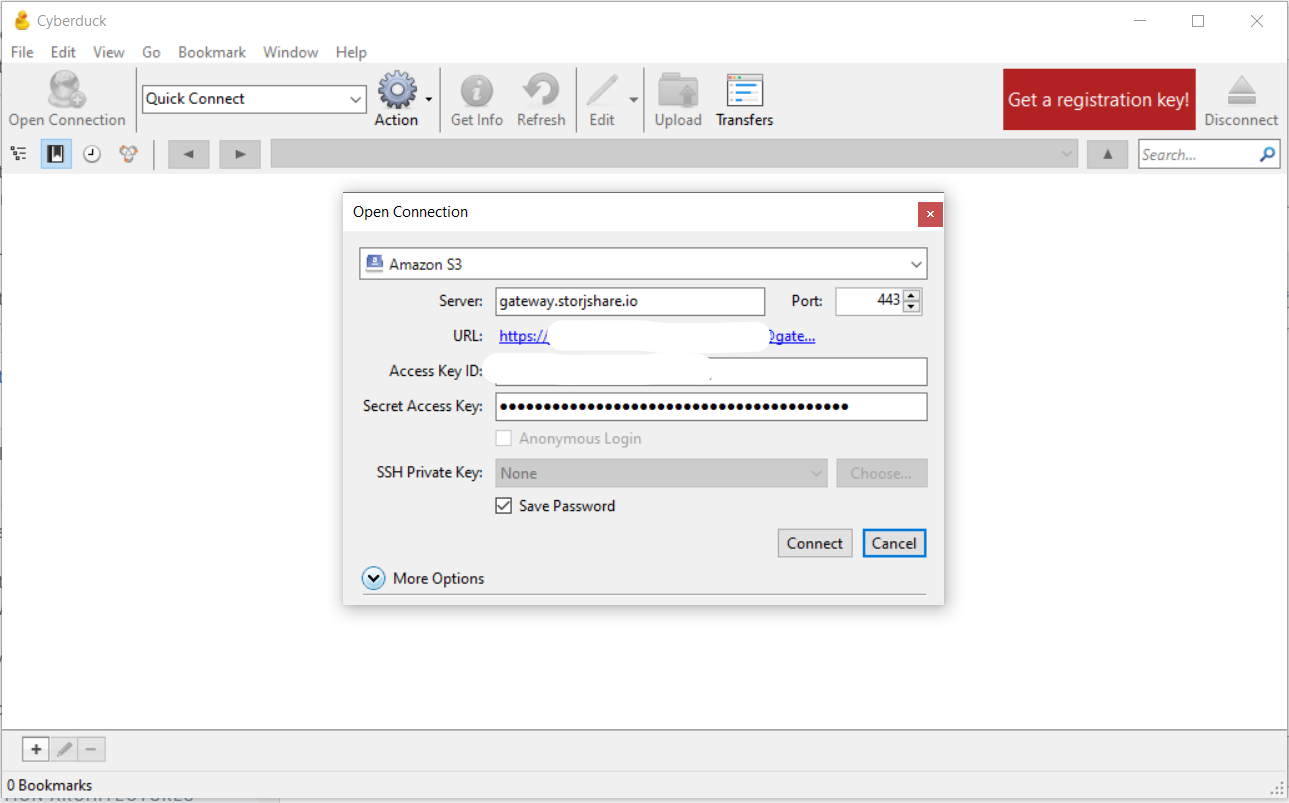
-To configure **Storj DCS** as the decentralized cloud storage network target, you’ll need to generate Storj credentials.
+To configure **Storj** as the decentralized cloud storage network target, you’ll need to generate Storj credentials.
### Using CyberDuck with Storj - macOS
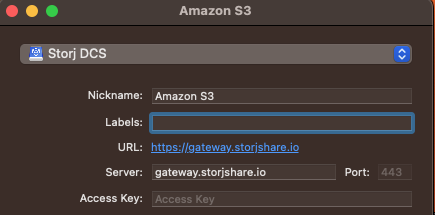
-Once the download is complete, you'll be able to open the CyberDuck client. By selecting the **+** button in the bottom left-hand corner of the client, you'll be able to add a connection bookmark, facilitating the connection between CyberDuck and Storj DCS. Select **Storj DCS** from the drop-down.
+Once the download is complete, you'll be able to open the CyberDuck client. By selecting the **+** button in the bottom left-hand corner of the client, you'll be able to add a connection bookmark, facilitating the connection between CyberDuck and Storj. Select **Storj** from the drop-down.
@@ -108,11 +108,11 @@ This is where you will add **Server, Access Key ID, and the Secret Access Key**
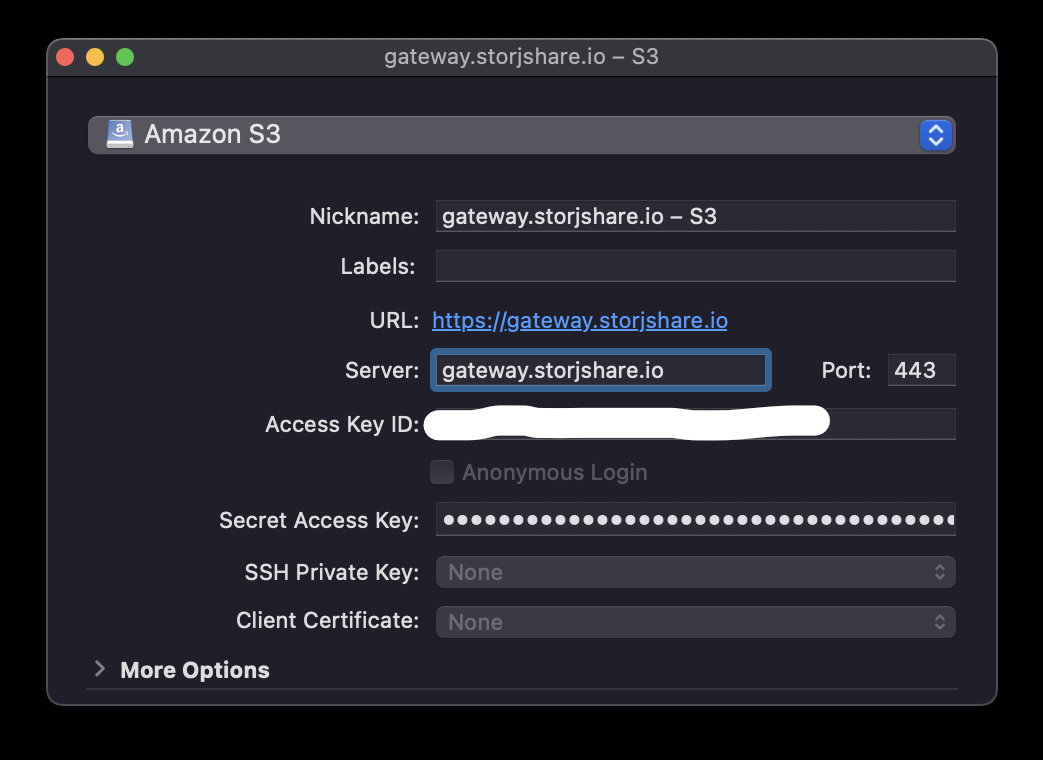
-To configure **Storj DCS** as the decentralized cloud storage network target, you’ll need to generate Storj credentials.
+To configure **Storj** as the decentralized cloud storage network target, you’ll need to generate Storj credentials.
### Generate Credentials to the Gateway MT
-One of the most versatile ways to get up and running with **Storj DCS** is through the [](docId:EGM8O-1xt2Az03eBWT8Rf)
+One of the most versatile ways to get up and running with **Storj** is through the [](docId:EGM8O-1xt2Az03eBWT8Rf)
**Gateway MT offers the following:**
@@ -183,7 +183,7 @@ As seen here:
### **For Mac OS**
-Back to the open connection in Cyberduck as we referenced above in [](docId:QQGzEDU8o-IodQWmr7xP3) you now have all the information you need to send files to your **Storj DCS** network.
+Back to the open connection in Cyberduck as we referenced above in [](docId:QQGzEDU8o-IodQWmr7xP3) you now have all the information you need to send files to your **Storj** network.
- **Select your saved bookmark** Here, you'll see the Amazon S3 server window reopen. To move forward, you'll simply just add in your Storj Gateway S3 credentials that we previously configured.
@@ -195,4 +195,4 @@ Back to the open connection in Cyberduck as we referenced above in [](docId:QQGz
Close the modal window and click the modified bookmark.
-If you’ve added your S3 Gateway Credentials properly, you’ll see your **Storj DCS** buckets, and you can now drag and drop files to your **Storj DCS** network seamlessly and easily via the Cyberduck GUI. Congrats!
+If you’ve added your S3 Gateway Credentials properly, you’ll see your **Storj** buckets, and you can now drag and drop files to your **Storj** network seamlessly and easily via the Cyberduck GUI. Congrats!
diff --git a/app/dcs/third-party-tools/dataverse/page.md b/app/dcs/third-party-tools/dataverse/page.md
index 964d0c1fa..99ae9a959 100644
--- a/app/dcs/third-party-tools/dataverse/page.md
+++ b/app/dcs/third-party-tools/dataverse/page.md
@@ -15,7 +15,7 @@ metadata:
## Storj Setup
-After [creating an account](https://storj.io/signup?partner=dataverse) on Storj DCS, you'll need to generate an access grant in order to get S3 credentials.
+After [creating an account](https://storj.io/signup?partner=dataverse) on Storj, you'll need to generate an access grant in order to get S3 credentials.
## Generate S3 credentials
diff --git a/app/dcs/third-party-tools/docker/page.md b/app/dcs/third-party-tools/docker/page.md
index 78a6efdc6..9b4b9fb39 100644
--- a/app/dcs/third-party-tools/docker/page.md
+++ b/app/dcs/third-party-tools/docker/page.md
@@ -15,7 +15,7 @@ metadata:
Containers are wonderful: Containers provide a powerful way to package and deploy an application and make the runtime environment immutable and reproducible. But using containers also requires more infrastructure - distributing containers requires a docker registry, either a public one (like Dockerhub) or a private instance.
-Under the hood, the container registry serves simple REST requests. As Storj DCS also can serve files via HTTP, it can be used as a container registry if the pieces are uploaded in the right order and mode.
+Under the hood, the container registry serves simple REST requests. As Storj also can serve files via HTTP, it can be used as a container registry if the pieces are uploaded in the right order and mode.
## The structure of a container registry
@@ -65,7 +65,7 @@ So let’s see an example. What is the publishing process, assuming we have a lo
The process is simple:
-1. Create/prepare all the JSON / blob files to upload to Storj DCS with uplink CLI (or UI)
+1. Create/prepare all the JSON / blob files to upload to Storj with uplink CLI (or UI)
2. During the upload, define the custom HTTP header for the manifests
diff --git a/app/dcs/third-party-tools/duplicati/page.md b/app/dcs/third-party-tools/duplicati/page.md
index 22ed8462c..1e42991f3 100644
--- a/app/dcs/third-party-tools/duplicati/page.md
+++ b/app/dcs/third-party-tools/duplicati/page.md
@@ -35,11 +35,11 @@ To restore a small file, Duplicati has to download the entire block it is contai
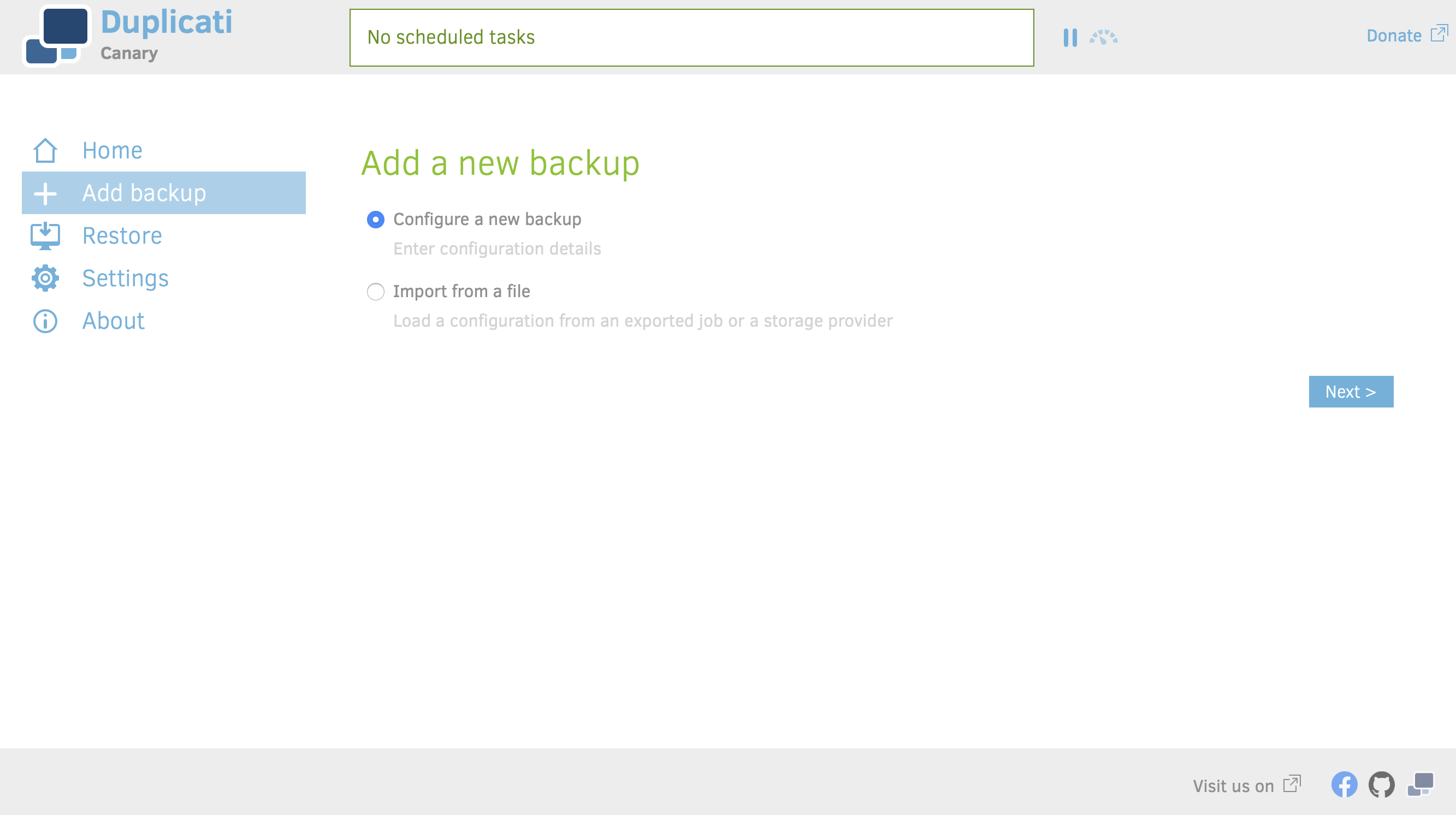
-2\. Enter a name for this backup. For this example, we'll call it "My Backup Job." The Storj DCS plugin will encrypt all files before they get uploaded. We don't want to encrypt each file twice. Disable the Duplicati encryption.
+2\. Enter a name for this backup. For this example, we'll call it "My Backup Job." The Storj plugin will encrypt all files before they get uploaded. We don't want to encrypt each file twice. Disable the Duplicati encryption.
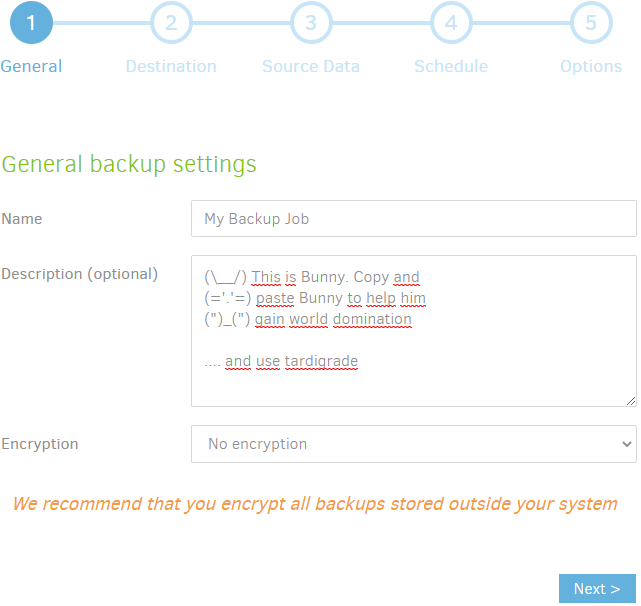
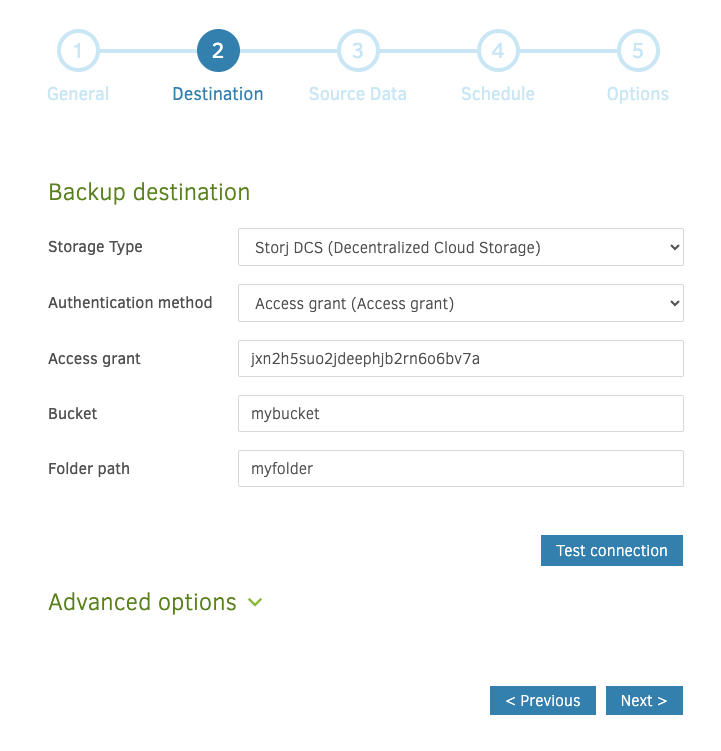
-3\. Click the storage type dropdown and select "Storj DCS (Decentralized Cloud Storage)." The authentication method should be Access Grant (Access Grant). Enter an Access Grant, see [](docId:OXSINcFRuVMBacPvswwNU), bucket, and, optionally, a folder.
+3\. Click the storage type dropdown and select "Storj (Decentralized Cloud Storage)." The authentication method should be Access Grant (Access Grant). Enter an Access Grant, see [](docId:OXSINcFRuVMBacPvswwNU), bucket, and, optionally, a folder.
@@ -67,7 +67,7 @@ To restore a small file, Duplicati has to download the entire block it is contai
| backup-test-samples=0 | The Storj protocol checks the hash at the end of every file upload. An additional test sample is not needed. Use list-verify-uploads instead. |
| list-verify-uploads=true | If a file upload fails for any reason, a final listing will catch it. |
| no-auto-compact=true | If a large number of small files are detected during a backup, or wasted space is found after deleting backups, the remote data will be compacted. This will cause a lot of unnecessary and expensive download traffic. |
-| threshold | As files are changed, some data stored at the remote destination may not be required. This option controls how much wasted space the destination can contain before being reclaimed. Depending on the use case, the threshold can be reduced to 0. Storj DCS doesn't charge you for the additional delete and re-upload operations. |
+| threshold | As files are changed, some data stored at the remote destination may not be required. This option controls how much wasted space the destination can contain before being reclaimed. Depending on the use case, the threshold can be reduced to 0. Storj doesn't charge you for the additional delete and re-upload operations. |
| zip-compression-method | This option can be used to set up an alternative compression method, such as LZMA. |
8\. Click "Save", and you should see the "My Backup Job" we created on the Duplicati homepage.
@@ -76,4 +76,4 @@ To restore a small file, Duplicati has to download the entire block it is contai
9\. You can select "Run now" if you would like to do a backup instantly.
-Congrats, you've set up Duplicati Backup to Storj DCS! 🎉
+Congrats, you've set up Duplicati Backup to Storj! 🎉
diff --git a/app/dcs/third-party-tools/fastly/page.md b/app/dcs/third-party-tools/fastly/page.md
index 2dfdc5cf0..ce18584a8 100644
--- a/app/dcs/third-party-tools/fastly/page.md
+++ b/app/dcs/third-party-tools/fastly/page.md
@@ -164,4 +164,4 @@ if (req.method == "GET" && !req.backend.is_shield) {
Note that, as mentioned above, if you have an **override host** specified in your Fastly service settings, that value will cause the `http.host` header to be overwritten which could be invalid for AWS authentication.
-See also [Storj DCS Object Storage on Fastly](https://docs.fastly.com/en/guides/storj-dcs-object-storage).
+See also [Storj Object Storage on Fastly](https://docs.fastly.com/en/guides/storj-dcs-object-storage).
diff --git a/app/dcs/third-party-tools/file-transfer-performance/page.md b/app/dcs/third-party-tools/file-transfer-performance/page.md
index c6c5d9ca5..5d7e729e0 100644
--- a/app/dcs/third-party-tools/file-transfer-performance/page.md
+++ b/app/dcs/third-party-tools/file-transfer-performance/page.md
@@ -20,7 +20,7 @@ The exact optimal settings for parallel file transfers vary based on your own co
## Parallelism on Storj
-Storj DCS achieves decentralization by breaking files into chunks and distributing those chunks among nodes. First, files are broken into 64MB segments. Each segment is then distributed as 80 smaller pieces to different nodes. These chunks of segments and pieces are the fundamental ideas that form the basis for parallelism in file transfers with the Storj network.
+Storj achieves decentralization by breaking files into chunks and distributing those chunks among nodes. First, files are broken into 64MB segments. Each segment is then distributed as 80 smaller pieces to different nodes. These chunks of segments and pieces are the fundamental ideas that form the basis for parallelism in file transfers with the Storj network.
When files are transferred between your local system and the Storj network, each segment of the file is usually sent to the network serially. However, within each segment, the individual pieces are transferred in parallel. This is Storj's Base Parallelism model for parallel transfer.
@@ -30,7 +30,7 @@ With these two concepts in mind, we can begin considering the available tools fo
## Tools
-The two main tools available to transfer files between a local system and Storj DCS are [](docId:TbMdOGCAXNWyPpQmH6EOq) and [](docId:LdrqSoECrAyE_LQMvj3aF)
+The two main tools available to transfer files between a local system and Storj are [](docId:TbMdOGCAXNWyPpQmH6EOq) and [](docId:LdrqSoECrAyE_LQMvj3aF)
Uplink is Storj's command line tool for transferring directly with the Storj network. As a native CLI tool, Uplink is able to bypass the Storj network's edge service layer and connect directly to nodes on the network. This allows for more efficient transfers and higher throughput.
diff --git a/app/dcs/third-party-tools/filezilla/filezilla-native/page.md b/app/dcs/third-party-tools/filezilla/filezilla-native/page.md
index 79a8f71cb..adb2a3f5b 100644
--- a/app/dcs/third-party-tools/filezilla/filezilla-native/page.md
+++ b/app/dcs/third-party-tools/filezilla/filezilla-native/page.md
@@ -13,7 +13,7 @@ metadata:
## Introduction
-This guide walks users through the process of setting up FileZilla to transfer files over Storj DCS.
+This guide walks users through the process of setting up FileZilla to transfer files over Storj.
{% callout type="info" %}
The native integration uses [](docId:Pksf8d0TCLY2tBgXeT18d) for your object data, including metadata and path data.
@@ -27,11 +27,11 @@ The **_ FileZilla_** Client is a fast and reliable cross-platform (Windows, Linu
It includes a site manager to store all your connection details and logins, as well as an Explorer-style interface that shows the local and remote folders and can be customized independently.
-With the launch of the native Storj DCS Integration into the FileZilla client, developers can use the client configured to transfer files point-to-point using the decentralized cloud.
+With the launch of the native Storj Integration into the FileZilla client, developers can use the client configured to transfer files point-to-point using the decentralized cloud.
## Getting Started
-
+
## Create an Access Grant
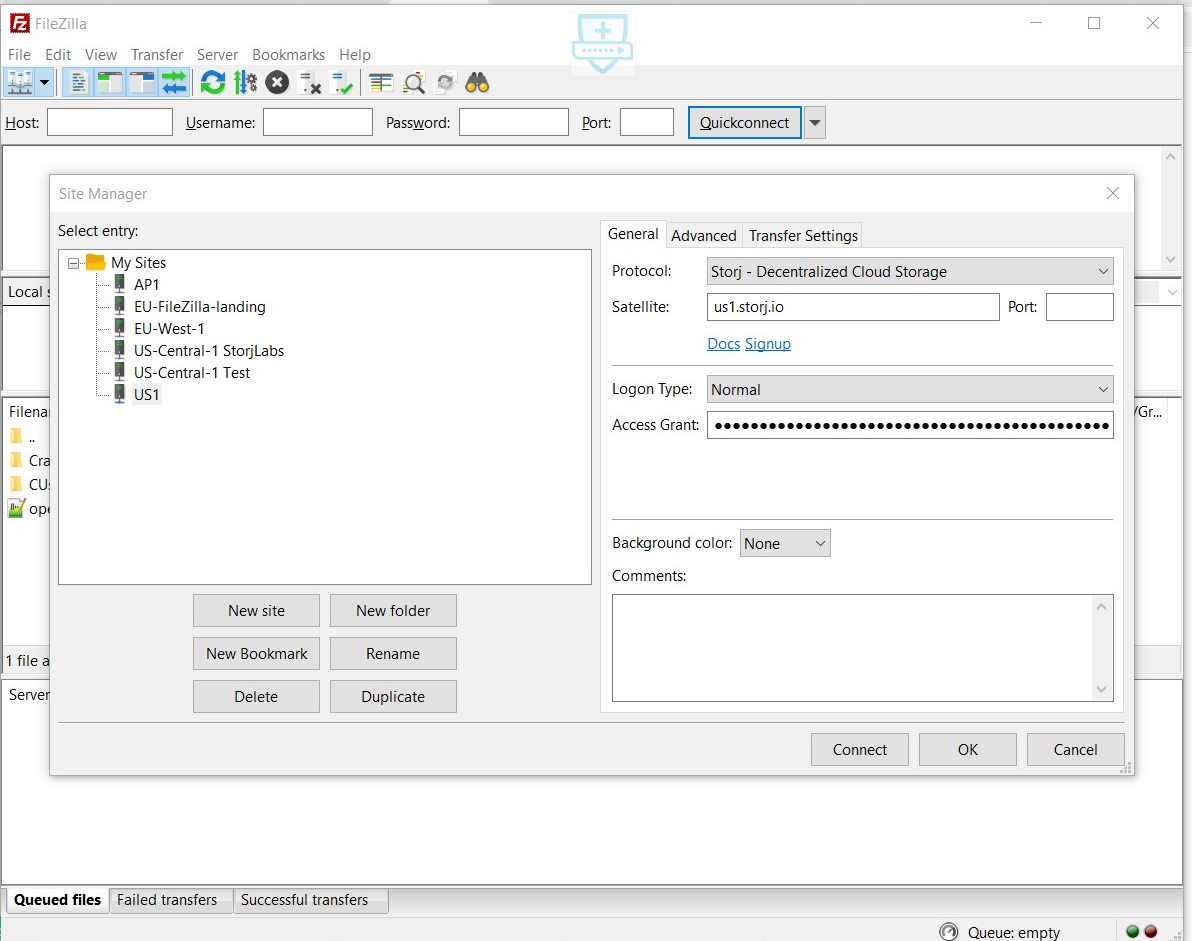
@@ -63,7 +63,7 @@ Now enter the **Satellite** and **Access Grant** as shown below (Entering the po
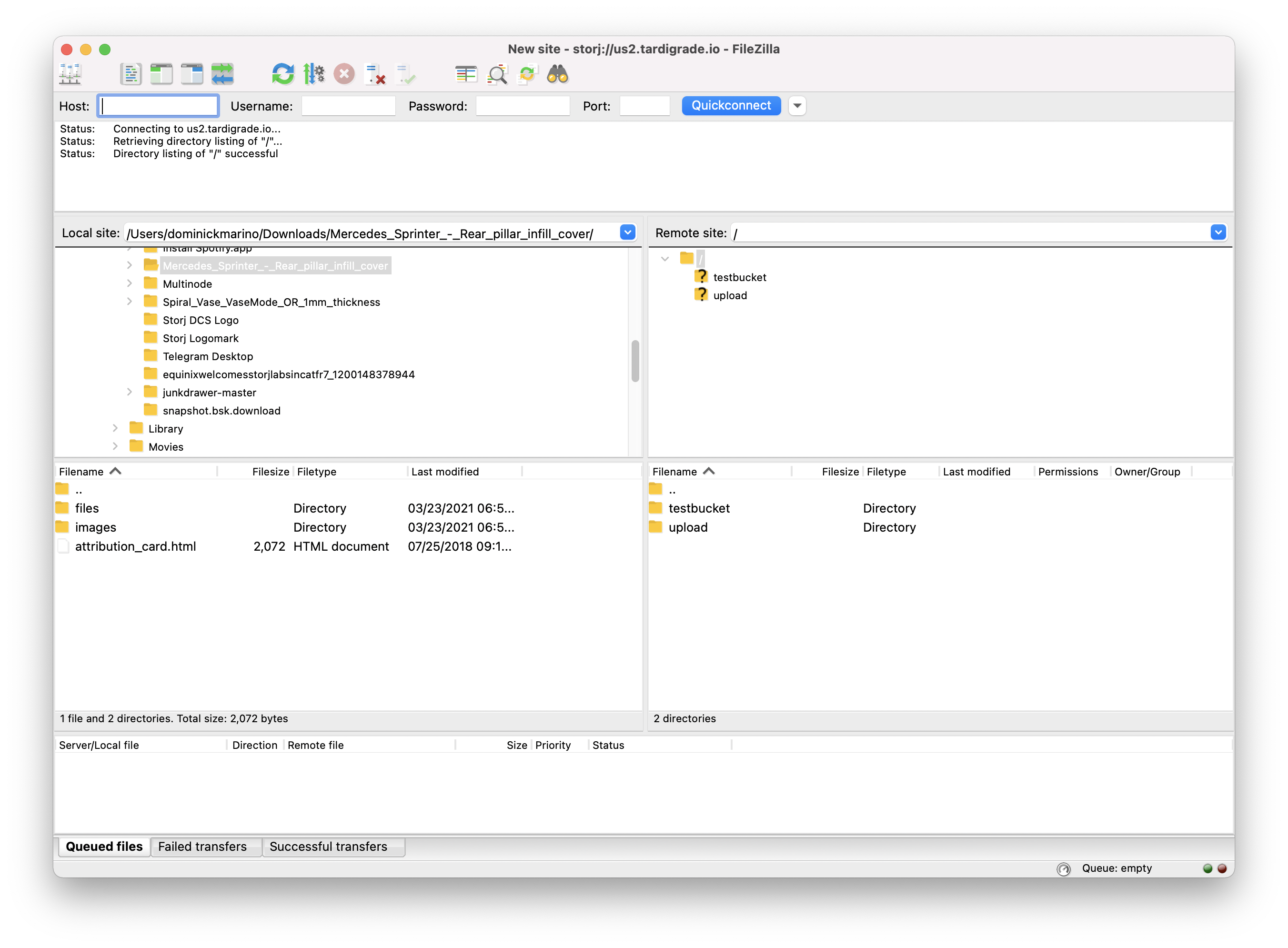
-After you enter the above information, hit the "Connect" button, and FileZilla will connect directly to the remote site. You should see a screen showing your local site vs. Storj DCS, like so:
+After you enter the above information, hit the "Connect" button, and FileZilla will connect directly to the remote site. You should see a screen showing your local site vs. Storj, like so:
diff --git a/app/dcs/third-party-tools/filezilla/filezilla-pro/page.md b/app/dcs/third-party-tools/filezilla/filezilla-pro/page.md
index 4239c3fa1..651b38390 100644
--- a/app/dcs/third-party-tools/filezilla/filezilla-pro/page.md
+++ b/app/dcs/third-party-tools/filezilla/filezilla-pro/page.md
@@ -11,25 +11,25 @@ metadata:
file transfers.
---
-## How to Integrate Filezilla Pro with Storj DCS to Easily Find, Transfer and Download All Of Your Files
+## How to Integrate Filezilla Pro with Storj to Easily Find, Transfer and Download All Of Your Files
At a quick glance, FileZilla provides a fast and reliable cross-platform (Windows, Linux and Mac OS X) FTP, FTPS and SFTP client that supports connections, file transfers and file structure browsing for many of today’s cloud data storage services, including Storj. This integration is beneficial for developers as it allows them to use the FileZilla Pro client to transfer files point-to-point using the decentralized cloud.
-However, there are some caveats around using FileZilla that Storj DCS users should take into consideration, namely what version of FileZilla supports integration with Storj.
+However, there are some caveats around using FileZilla that Storj users should take into consideration, namely what version of FileZilla supports integration with Storj.
## What Is the Difference Between FileZilla and FileZilla Pro and How Does This Influence Integration with Storj?
-FileZilla is available in a free version known as FileZilla Standard. It supports Storj DCS, FTP, and FTP over TLS (FTPS) and SFTP. It is open-source software distributed free of charge under the terms of the GNU General Public License.
+FileZilla is available in a free version known as FileZilla Standard. It supports Storj, FTP, and FTP over TLS (FTPS) and SFTP. It is open-source software distributed free of charge under the terms of the GNU General Public License.
-[**FileZillaPro**](https://filezillapro.com) is a paid upgrade that delivers all of the base functionality of [**FileZilla Standard**](https://filezilla-project.org), while adding additional support for many of today’s popular cloud data storage services like Amazon S3, OneDrive, Dropbox, WebDAV, Microsoft Azure, OneDrive for Business and SharePoint, Google Cloud, Backblaze and, of course, Storj DCS.
+[**FileZillaPro**](https://filezillapro.com) is a paid upgrade that delivers all of the base functionality of [**FileZilla Standard**](https://filezilla-project.org), while adding additional support for many of today’s popular cloud data storage services like Amazon S3, OneDrive, Dropbox, WebDAV, Microsoft Azure, OneDrive for Business and SharePoint, Google Cloud, Backblaze and, of course, Storj.
-You can use FileZilla Standard with the Storj DCS native connector—as long as you don’t use a package manager to [](docId:OkJongWeLGhPy4KKz34W4). To learn how to use the Storj integration with FileZilla Standard, check out this [](docId:OkJongWeLGhPy4KKz34W4). To leverage the FileZillaPro functionality, you can integrate it with Storj using a native connector or our backwards S3-compatible Gateway MT. Below we will focus on the integration between Storj and FileZilla Pro.
+You can use FileZilla Standard with the Storj native connector—as long as you don’t use a package manager to [](docId:OkJongWeLGhPy4KKz34W4). To learn how to use the Storj integration with FileZilla Standard, check out this [](docId:OkJongWeLGhPy4KKz34W4). To leverage the FileZillaPro functionality, you can integrate it with Storj using a native connector or our backwards S3-compatible Gateway MT. Below we will focus on the integration between Storj and FileZilla Pro.
## Storj + FileZilla Pro Integration
-FileZilla Pro gives users the option to send files to a Storj DCS account in two ways, either via native uplink or via [](docId:AsyYcUJFbO1JI8-Tu8tW3). Let’s take a look at some of the specs of both Native Uplink and Gateway MT, providing a clearer understanding of which integration method will work better for unique use cases.
+FileZilla Pro gives users the option to send files to a Storj account in two ways, either via native uplink or via [](docId:AsyYcUJFbO1JI8-Tu8tW3). Let’s take a look at some of the specs of both Native Uplink and Gateway MT, providing a clearer understanding of which integration method will work better for unique use cases.
-## Native Uplink specs regarding integration with Storj DCS:
+## Native Uplink specs regarding integration with Storj:
- Native Integration (Fastest for downloading large files)
@@ -39,7 +39,7 @@ FileZilla Pro gives users the option to send files to a Storj DCS account in two
- Has a 2.68x upload multiplier for uploads and does not support segment parallelism
-### GatewayMT specs regarding integration with Storj DCS:
+### GatewayMT specs regarding integration with Storj:
- Gateway MT (Fastest for uploading large files)
@@ -49,7 +49,7 @@ FileZilla Pro gives users the option to send files to a Storj DCS account in two
- A 1GB upload will result in 1GB of data being uploaded to storage nodes across the network, based on S3 standard
-There are benefits to each method of integration. To provide users with the best value as they look to make the most out of their Storj and FileZillaPro integration, we’ve put together dedicated sections on integrating Storj DCS with FileZillaPro via native uplink as well as through Gateway MT.
+There are benefits to each method of integration. To provide users with the best value as they look to make the most out of their Storj and FileZillaPro integration, we’ve put together dedicated sections on integrating Storj with FileZillaPro via native uplink as well as through Gateway MT.
### Storj + FileZilla Pro Via Native Uplink
@@ -103,11 +103,11 @@ Once the FileZilla Pro client is open, select the **Open the Site Manager** icon
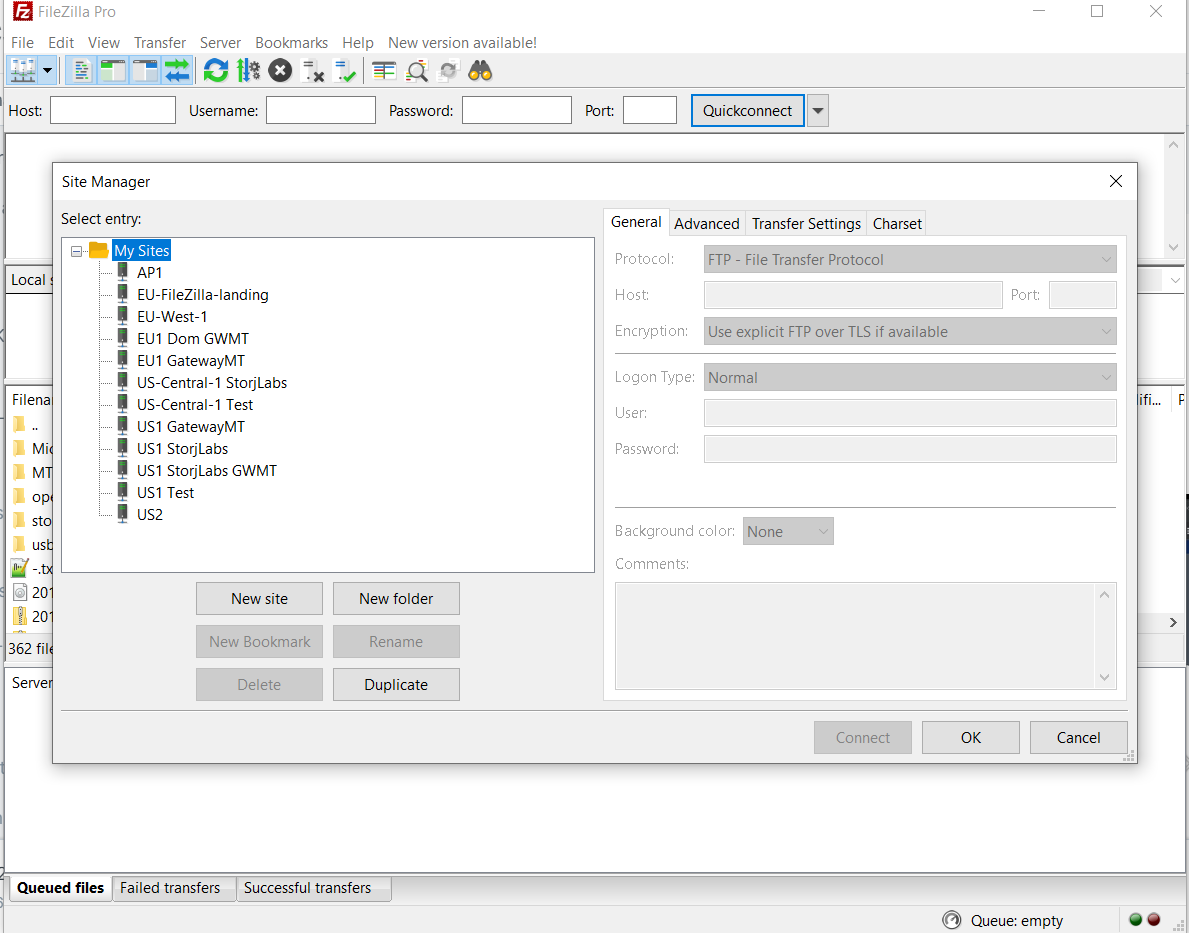
-Now, add the appropriate **Satellite** url (without adding `htpps://`) and simply copy your Access Grant that was previously generated within your Storj DCS account to the **Access Grant** field:
+Now, add the appropriate **Satellite** url (without adding `htpps://`) and simply copy your Access Grant that was previously generated within your Storj account to the **Access Grant** field:
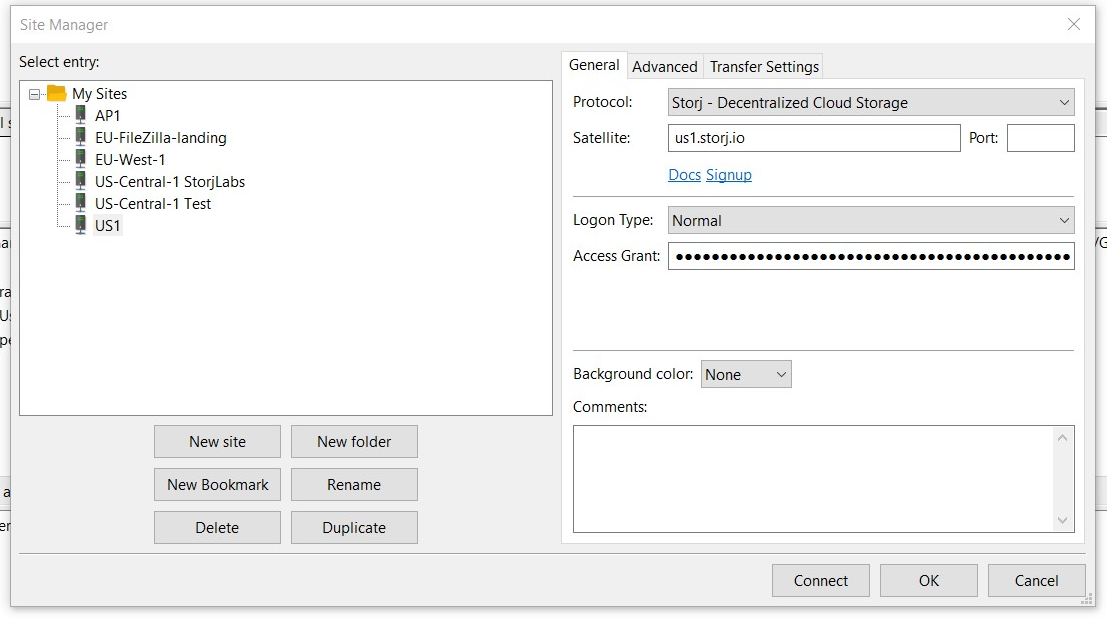
-Hit **Connect**, and access to your Storj DCS account should be established.
+Hit **Connect**, and access to your Storj account should be established.
### Storj + FileZilla Pro via Gateway MT
@@ -167,7 +167,7 @@ Copy your **Access Key**, **Secret Key**, and **Endpoint** to a safe location. s
9\. Optionally, you can enter a description here.
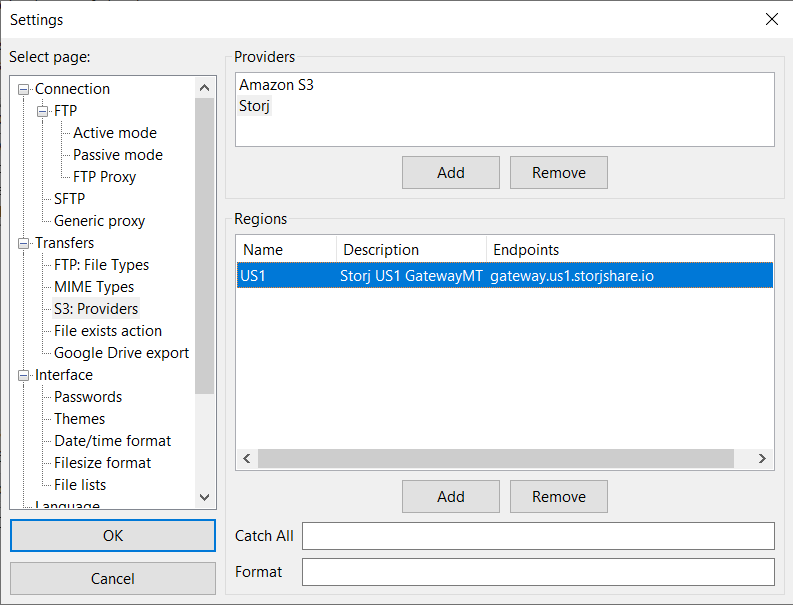
-10\. Click on the **Endpoints** column of the new region row and enter the **_Endpoint address_** for Storj DCS, generated earlier during the creation of the Storj Gateway MT credentials (without adding `https://`).
+10\. Click on the **Endpoints** column of the new region row and enter the **_Endpoint address_** for Storj, generated earlier during the creation of the Storj Gateway MT credentials (without adding `https://`).
diff --git a/app/dcs/third-party-tools/filezilla/page.md b/app/dcs/third-party-tools/filezilla/page.md
index 0d787431a..51adcf9b9 100644
--- a/app/dcs/third-party-tools/filezilla/page.md
+++ b/app/dcs/third-party-tools/filezilla/page.md
@@ -16,11 +16,11 @@ metadata:
{% quick-links %}
{% quick-link href="docId:OkJongWeLGhPy4KKz34W4" %}
-How to set up FileZilla to transfer files over Storj DCS
+How to set up FileZilla to transfer files over Storj
{% /quick-link %}
{% quick-link href="docId:APk9353kCNcg5PKRPQ06u" %}
-How to Integrate Filezilla Pro with Storj DCS to Easily Find, Transfer and Download All Of Your Files
+How to Integrate Filezilla Pro with Storj to Easily Find, Transfer and Download All Of Your Files
{% /quick-link %}
{% /quick-links %}
diff --git a/app/dcs/third-party-tools/hashbackup/page.md b/app/dcs/third-party-tools/hashbackup/page.md
index e93017b1d..a0b4e0ed4 100644
--- a/app/dcs/third-party-tools/hashbackup/page.md
+++ b/app/dcs/third-party-tools/hashbackup/page.md
@@ -20,11 +20,11 @@ The best way to benefit from data backups is to do them regularly. However, freq
These are some of the problems that [HashBackup](https://www.hashbackup.com/hashbackup/overview.html) tries to solve. HashBackup addresses the issues of security and storage by not only encrypting backups but also compressing them. This approach offers an efficient, reliable solution for performing backups regularly which doesn't need compromise due to storage or compute limitations.
-The benefits of HashBackup can be enhanced with the supplemental storage and accessibility offered by Storj DCS. This document will describe how to configure Storj as a backup destination for HashBackup.
+The benefits of HashBackup can be enhanced with the supplemental storage and accessibility offered by Storj. This document will describe how to configure Storj as a backup destination for HashBackup.
## Running HashBackup with Storj as a Destination
-While HashBackup compresses backups to limit the storage requirements necessary for local storage, there are still use cases for backing up data externally to cloud services like Storj. For example, the decentralized network of Storj DCS nodes increases availability and security when accessing your backups.
+While HashBackup compresses backups to limit the storage requirements necessary for local storage, there are still use cases for backing up data externally to cloud services like Storj. For example, the decentralized network of Storj nodes increases availability and security when accessing your backups.
HashBackup allows the configuration of additional storage destinations through a `dest.conf` file which contains information about the destination and access keys to upload data. Before that, however, you must first ensure that HashBackup is properly installed to perform local backups.
@@ -36,7 +36,7 @@ To install HashBackup on your local system, follow these steps [as shown in the
3. Move the `hb` binary to your local search path (on Linux, `sudo mv hb /usr/local/bin/`)
-Now, we must create a bucket in Storj DCS that will hold the backup data uploaded by HashBackup. While doing this, it will be important to also create access keys for the bucket which can be used by HashBackup to securely access the Storj bucket.
+Now, we must create a bucket in Storj that will hold the backup data uploaded by HashBackup. While doing this, it will be important to also create access keys for the bucket which can be used by HashBackup to securely access the Storj bucket.
1. Follow [](docId:quai3ugaP9paich3ai5e) to get an **Access Key**, **Secret Key**, and **End Point**. Keep them in a safe location as these will be used later to authenticate HashBackup with Storj.
@@ -46,7 +46,7 @@ Now it is time to create the local backup directory with HashBackup. This step w
2. Create a file called `dest.conf` within the `backup` directory
-The `dest.conf` file will hold all of the external configuration details as listed in the [HashBackup S3 Destination docs](https://www.hashbackup.com/hashbackup/destinations/s3.html). For Storj DCS, this file should look as follows:
+The `dest.conf` file will hold all of the external configuration details as listed in the [HashBackup S3 Destination docs](https://www.hashbackup.com/hashbackup/destinations/s3.html). For Storj, this file should look as follows:
```Text
destname storj
@@ -73,9 +73,9 @@ This file contains a few key definitions:
- **secretkey**: this is the **Secret Key** from earlier
-- **bucket**: the name of the bucket in Storj DCS, for example **"hashbackup"**
+- **bucket**: the name of the bucket in Storj, for example **"hashbackup"**
-With HashBackup now configured to send remote backups to Storj, any new files that are backed up will create a local copy as well as a remote copy. For example, running the following command will back up a local directory called `data` both in the local `backup` folder as well as in the `hashbackup` Storj DCS bucket we just configured:
+With HashBackup now configured to send remote backups to Storj, any new files that are backed up will create a local copy as well as a remote copy. For example, running the following command will back up a local directory called `data` both in the local `backup` folder as well as in the `hashbackup` Storj bucket we just configured:
```Text
hb backup -c backup data
@@ -85,4 +85,4 @@ If the local backup is lost, damaged, or pruned but later needed, the remote bac
### Conclusion
-Storj DCS offers an excellent option for decentralized, distributed, cloud-based file storage. With a global distribution of network nodes and inherently secure decentralized access, Storj is a great platform for hosting files and data. These same benefits extend to backups of data, which is where an automated tool like HashBackup can combine with Storj to ensure that your files are always accessible locally. In this article, we showed how to do just that by installing HashBackup and configuring it to use Storj as a remote destination. Now, the power of encrypted and compressed backups are able to be hosted on the distributed Storj platform, with all of the benefits that brings.
+Storj offers an excellent option for decentralized, distributed, cloud-based file storage. With a global distribution of network nodes and inherently secure decentralized access, Storj is a great platform for hosting files and data. These same benefits extend to backups of data, which is where an automated tool like HashBackup can combine with Storj to ensure that your files are always accessible locally. In this article, we showed how to do just that by installing HashBackup and configuring it to use Storj as a remote destination. Now, the power of encrypted and compressed backups are able to be hosted on the distributed Storj platform, with all of the benefits that brings.
diff --git a/app/dcs/third-party-tools/kerberos-vault/page.md b/app/dcs/third-party-tools/kerberos-vault/page.md
index 5da9d477f..c8f7e9614 100644
--- a/app/dcs/third-party-tools/kerberos-vault/page.md
+++ b/app/dcs/third-party-tools/kerberos-vault/page.md
@@ -17,13 +17,13 @@ metadata:
The [Kerberos.io](https://kerberos.io) project (not to be confused with the authentication protocol of the same name) offers an open-source platform for video analytics and monitoring. With a modular system design focused on minimal startup requirements and additional components available to add later, Kerberos.io is built to work for everything from small, personal systems to complex enterprise configurations. This makes it a useful solution that is relevant at all scales.
-The modularity of Kerberos.io includes optional components that help integrate it into any cloud architecture. One of these components is [Kerberos Vault](https://kerberos.io/product/vault/), which provides a flexible and extensible storage solution for video files. Kerberos Vault is designed to work with several different cloud providers, including Storj DCS, to allow for customized storage options where users can bring their own providers.
+The modularity of Kerberos.io includes optional components that help integrate it into any cloud architecture. One of these components is [Kerberos Vault](https://kerberos.io/product/vault/), which provides a flexible and extensible storage solution for video files. Kerberos Vault is designed to work with several different cloud providers, including Storj, to allow for customized storage options where users can bring their own providers.
-## Storj DCS and Kerberos
+## Storj and Kerberos
-Storj's decentralized cloud storage platform offers a great video storage backend for integration with Kerberos.io and Kerberos Vault. This is because the distributed storage design that Storj DCS is built on offers both high availability access to video files (thanks to its network of nodes across multiple regions) and secure, reliable hosting with no single-point-of-failure.
+Storj's decentralized cloud storage platform offers a great video storage backend for integration with Kerberos.io and Kerberos Vault. This is because the distributed storage design that Storj is built on offers both high availability access to video files (thanks to its network of nodes across multiple regions) and secure, reliable hosting with no single-point-of-failure.
-Conveniently, it is fairly simple to configure Storj DCS to work with Kerberos Vault. This doc will show the steps necessary to do so.
+Conveniently, it is fairly simple to configure Storj to work with Kerberos Vault. This doc will show the steps necessary to do so.
### Prerequisites
@@ -39,13 +39,13 @@ With these prerequisites satisfied, we can begin configuring Kerberos Vault to u
### Creating a Storj Bucket and Access Credentials
-The first step in configuring Storj as the storage backend for Kerberos.io is to create a bucket in your Storj DCS account and [](docId:AsyYcUJFbO1JI8-Tu8tW3) for the bucket.
+The first step in configuring Storj as the storage backend for Kerberos.io is to create a bucket in your Storj account and [](docId:AsyYcUJFbO1JI8-Tu8tW3) for the bucket.
Kerberos Vault will then use the bucket information and access grant to connect with Storj.
For this, do the following steps:
-1\) Log in to your Storj DCS account
+1\) Log in to your Storj account
2\) On the main dashboard, click [](docId:pxdnqsVDjCLZgeEXt2S6x) and **"New Bucket"**
@@ -133,6 +133,6 @@ Now it is time to tell Kerberos where to store videos (your Storj bucket) and ho
### Summary
-The flexibility of Kerberos.io and its components like Kerberos Vault are what make it a versatile platform for video monitoring and analytics. From single-camera setups to advanced cloud-based enterprise installations, the Kerberos.io video technology is adaptable to any configuration. This adaptability includes the option to customize your choice for video storage with the platform, which is where Storj DCS makes an excellent choice.
+The flexibility of Kerberos.io and its components like Kerberos Vault are what make it a versatile platform for video monitoring and analytics. From single-camera setups to advanced cloud-based enterprise installations, the Kerberos.io video technology is adaptable to any configuration. This adaptability includes the option to customize your choice for video storage with the platform, which is where Storj makes an excellent choice.
-In this tutorial, we demonstrated the steps to set up a Storj bucket and create access credentials for that bucket. We then showed how to update a Kerberos Vault installation to use Storj as a storage provider. Doing all of this allows Kerberos.io to leverage the distributed storage network provided by Storj DCS, taking advantage of all the benefits it provides. Your video monitoring and analytics solution is now enhanced with the power of decentralized media storage.
+In this tutorial, we demonstrated the steps to set up a Storj bucket and create access credentials for that bucket. We then showed how to update a Kerberos Vault installation to use Storj as a storage provider. Doing all of this allows Kerberos.io to leverage the distributed storage network provided by Storj, taking advantage of all the benefits it provides. Your video monitoring and analytics solution is now enhanced with the power of decentralized media storage.
diff --git a/app/dcs/third-party-tools/mongodb/page.md b/app/dcs/third-party-tools/mongodb/page.md
index cb39a7c43..0b7a05f73 100644
--- a/app/dcs/third-party-tools/mongodb/page.md
+++ b/app/dcs/third-party-tools/mongodb/page.md
@@ -7,10 +7,10 @@ redirects:
- /dcs/how-tos/mongodb-ops-manager-backup
- /how-tos/mongodb-ops-manager-backup
metadata:
- title: Guide on Deploying MongoDB Ops Manager with Storj DCS
+ title: Guide on Deploying MongoDB Ops Manager with Storj
description:
Step-by-step tutorial on how to deploy, monitor, and scale MongoDB
- using Ops Manager on your own infrastructure with Storj DCS.
+ using Ops Manager on your own infrastructure with Storj.
---
## Introduction
@@ -25,7 +25,7 @@ For the complete documentation for the service, see:
@@ -22,7 +22,7 @@ Mobile app download links:
- Google Play Store:
-## Configure Photos+ to use Storj DCS
+## Configure Photos+ to use Storj
1. When starting **Photos+**, you will be shown an empty Library.
@@ -36,7 +36,7 @@ Mobile app download links:
-4\. Click **Configure** to begin setting up Storj DCS for Photos+.
+4\. Click **Configure** to begin setting up Storj for Photos+.
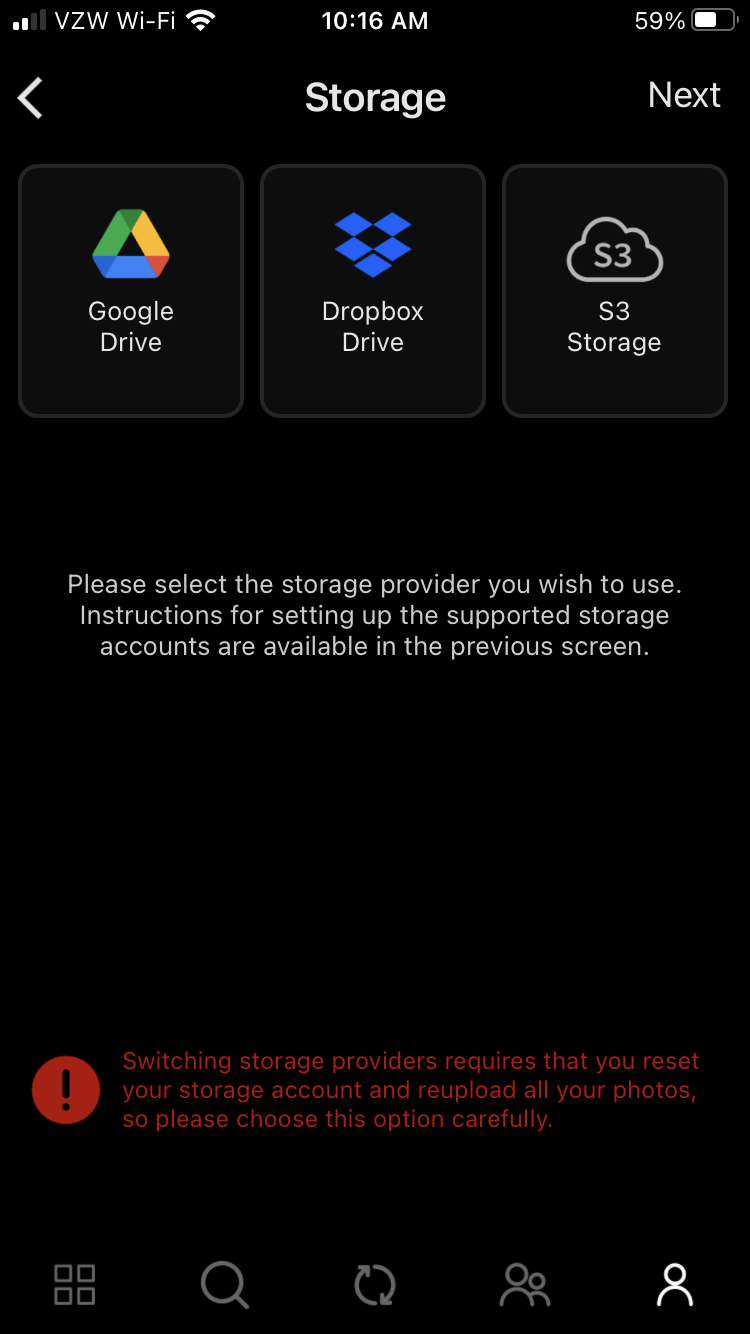
@@ -44,7 +44,7 @@ Mobile app download links:
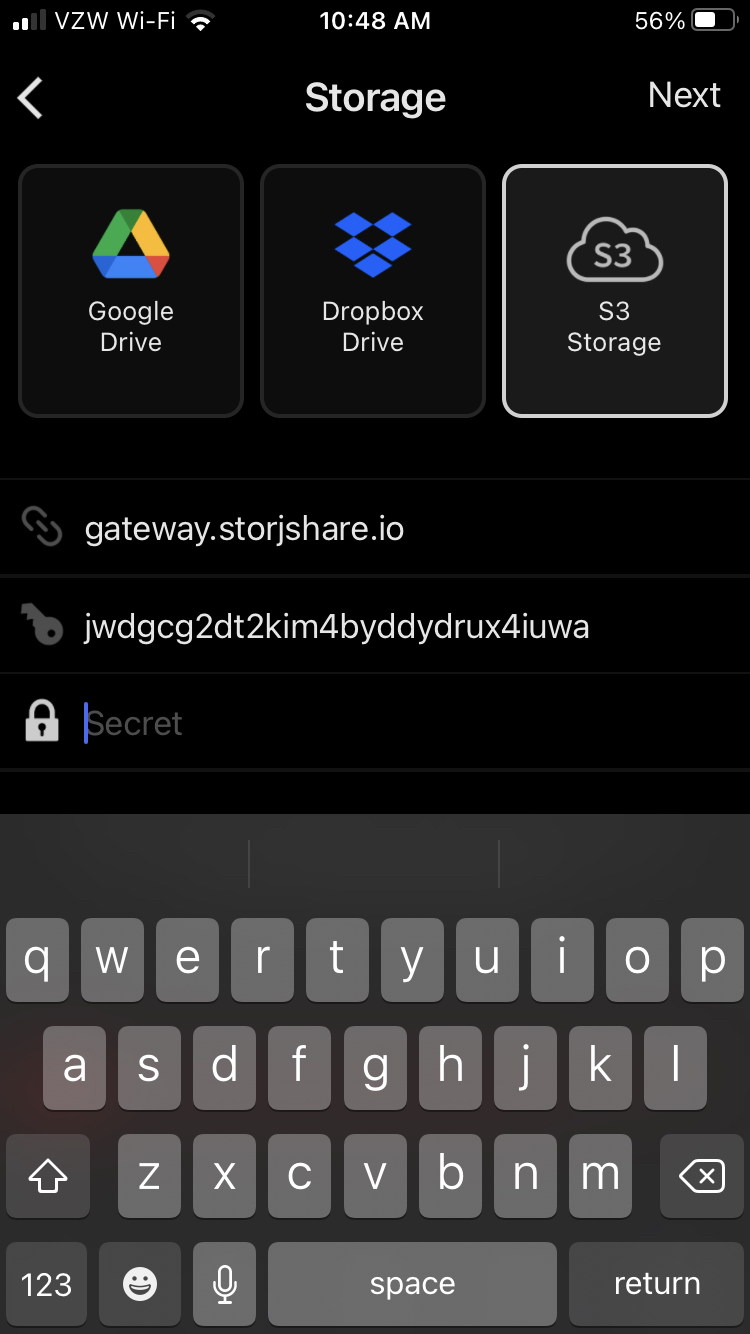
-6\. Once you’ve completed configuring Storj DCS as your Cloud Storage Provider, to see Storj in action, you’ll need to click the icon in the lower right corner composed of four squares to return to your Library. From there, click the three-dot icon in the upper right corner.
+6\. Once you’ve completed configuring Storj as your Cloud Storage Provider, to see Storj in action, you’ll need to click the icon in the lower right corner composed of four squares to return to your Library. From there, click the three-dot icon in the upper right corner.
@@ -64,6 +64,6 @@ Mobile app download links:
-11\. Click **Start** to begin synchronizing your library. You may check via the Storj DCS dashboard or use any of our command line tools to see if your library has been backed up to Storj.
+11\. Click **Start** to begin synchronizing your library. You may check via the Storj dashboard or use any of our command line tools to see if your library has been backed up to Storj.
diff --git a/app/dcs/third-party-tools/plex/page.md b/app/dcs/third-party-tools/plex/page.md
index 778c26cfc..65ebe618d 100644
--- a/app/dcs/third-party-tools/plex/page.md
+++ b/app/dcs/third-party-tools/plex/page.md
@@ -19,7 +19,7 @@ Managing a multimedia library can be tedious and time-consuming. Organizing your
## Video Playback from Anywhere
-With the Storj DCS decentralized video storage service, your multimedia objects are available anywhere, at any time. Decentralized video storage offers many advantages over traditional centralized storage. These include higher availability, better security, and a lower operating budget.
+With the Storj decentralized video storage service, your multimedia objects are available anywhere, at any time. Decentralized video storage offers many advantages over traditional centralized storage. These include higher availability, better security, and a lower operating budget.
With decentralized storage, your videos are distributed across a global network of nodes. This ensures more reliable access with fewer single points of failure. For that same reason, your files are not vulnerable to the security measures that may or may not exist for one central data repository. Additionally, Storj's network eliminates many of the maintenance and engineering costs of centralized object storage services.
@@ -29,7 +29,7 @@ The ability to store and retrieve your video files from anywhere using Storj's g
[Rclone](https://rclone.org) is a program that helps with the management of files on various cloud storage services. It provides a command called [`rclone mount`](https://rclone.org/commands/rclone_mount/) that allows files on cloud storage to be mounted as a local filesystem.
-For this guide, we are going to show how to set up Rclone to sync your local files with Storj DCS. This can then serve as your storage backend for a service like Plex.
+For this guide, we are going to show how to set up Rclone to sync your local files with Storj. This can then serve as your storage backend for a service like Plex.
## Getting Started
@@ -91,7 +91,7 @@ This recursively refreshes the root directory of the Rclone mount to pick up the
## Wrapping Up
-Now that you've set up Rclone to read and write to your Storj DCS buckets, you can configure Plex to use your mounted buckets as a storage location. Some tips for configuring Plex with this setup are:
+Now that you've set up Rclone to read and write to your Storj buckets, you can configure Plex to use your mounted buckets as a storage location. Some tips for configuring Plex with this setup are:
- Under Settings > Library, uncheck "empty trash automatically after each scan"
@@ -99,4 +99,4 @@ Now that you've set up Rclone to read and write to your Storj DCS buckets, you c
These, along with the other steps we took while setting up the mount, will help optimize Plex performance when reading from Storj.
-With Plex configured to use Storj DCS for storage, you now have a convenient streaming and organization platform backed by reliable, decentralized object storage.
+With Plex configured to use Storj for storage, you now have a convenient streaming and organization platform backed by reliable, decentralized object storage.
diff --git a/app/dcs/third-party-tools/rclone/rclone-native/page.md b/app/dcs/third-party-tools/rclone/rclone-native/page.md
index 18806363d..9e54424c9 100644
--- a/app/dcs/third-party-tools/rclone/rclone-native/page.md
+++ b/app/dcs/third-party-tools/rclone/rclone-native/page.md
@@ -141,7 +141,7 @@ passphrase> your-secret-encryption-phrase
```
{% callout type="info" %}
-The passphrase is used for encrypting and decrypting the data stored on Storj DCS (formerly known as Tardigrade). If you have any data previously uploaded to this project, you must enter the same passphrase in order to download it successfully.
+The passphrase is used for encrypting and decrypting the data stored on Storj (formerly known as Tardigrade). If you have any data previously uploaded to this project, you must enter the same passphrase in order to download it successfully.
{% /callout %}
A summary of the remote configuration will prompt. Type `y`and hit `Enter` to confirm it.
diff --git a/app/dcs/third-party-tools/rclone/rclone-s3/page.md b/app/dcs/third-party-tools/rclone/rclone-s3/page.md
index 841d46a4c..a2018d2a5 100644
--- a/app/dcs/third-party-tools/rclone/rclone-s3/page.md
+++ b/app/dcs/third-party-tools/rclone/rclone-s3/page.md
@@ -150,19 +150,19 @@ Since this can cause data loss, test first with the `--dry-run` flag to see exac
rclone sync --progress ~/Videos/ waterbear:mybucket/videos/
```
-The sync can also be done from Storj DCS to the local file system.
+The sync can also be done from Storj to the local file system.
```bash
rclone sync --progress waterbear:mybucket/videos/ ~/Videos/
```
-Or between two Storj DCS buckets.
+Or between two Storj buckets.
```bash
rclone sync --progress waterbear-us:mybucket/videos/ waterbear-europe:mybucket/videos/
```
-Or even between another cloud storage and Storj DCS.
+Or even between another cloud storage and Storj.
```bash
rclone sync --progress s3:mybucket/videos/ waterbear:mybucket/videos/
diff --git a/app/dcs/third-party-tools/restic/page.md b/app/dcs/third-party-tools/restic/page.md
index 58b7a32de..11794bb01 100644
--- a/app/dcs/third-party-tools/restic/page.md
+++ b/app/dcs/third-party-tools/restic/page.md
@@ -17,7 +17,7 @@ metadata:
**Restic** is a backup client written in Go language, it is highly secure and efficient. Each **Restic** backup is a snapshot of the server/files/directory, deduplicated from what was stored before. Any restore to a given backup will restore the server/files/directories to the exact state they were at that time.
-This is a quick-start tutorial that covers [Restic](https://restic.net) usage with Storj DCS.
+This is a quick-start tutorial that covers [Restic](https://restic.net) usage with Storj.
In this guide, we will cover only some of the basic features of the tool. The complete documentation for Restic is located here, at their [complete command reference](https://restic.readthedocs.io/en/latest/manual_rest.html).
@@ -27,7 +27,7 @@ This guide is experimental. The main functionality appears to work, but there ar
## Before you begin
-If you haven't yet, [create a Storj DCS account](https://storj.io/signup?partner=restic) before following the rest of the tutorial.
+If you haven't yet, [create a Storj account](https://storj.io/signup?partner=restic) before following the rest of the tutorial.
You will need the following:
diff --git a/app/dcs/third-party-tools/s3fs/page.md b/app/dcs/third-party-tools/s3fs/page.md
index a951818e0..a6a039fc6 100644
--- a/app/dcs/third-party-tools/s3fs/page.md
+++ b/app/dcs/third-party-tools/s3fs/page.md
@@ -20,7 +20,7 @@ metadata:
See [https://github.com/s3fs-fuse/s3fs-fuse](https://github.com/s3fs-fuse/s3fs-fuse#installation) for installation instructions for your OS.
-## Configure s3fs to use Storj DCS S3 Gateway
+## Configure s3fs to use Storj S3 Gateway
You can use either [](docId:EGM8O-1xt2Az03eBWT8Rf) or [](docId:yYCzPT8HHcbEZZMvfoCFa). You only need S3 compatible credentials and endpoint.
@@ -75,7 +75,7 @@ Check that it is working - The command:
sudo mount -a
```
-should not return any error. Next, check that your Storj DCS bucket is mounted:
+should not return any error. Next, check that your Storj bucket is mounted:
```Text
df -HT
diff --git a/app/dcs/third-party-tools/tesla-sentry-mode-teslausb/page.md b/app/dcs/third-party-tools/tesla-sentry-mode-teslausb/page.md
index 41aa98566..853d1242e 100644
--- a/app/dcs/third-party-tools/tesla-sentry-mode-teslausb/page.md
+++ b/app/dcs/third-party-tools/tesla-sentry-mode-teslausb/page.md
@@ -50,7 +50,7 @@ If you have not yet signed up, please [do so now](https://storj.io/signup).
Using the software in the [teslausb](https://github.com/marcone/teslausb) project with Storj is a multipart process, we will accomplish the following:
-- Generate Credentials for Storj DSC
+- Generate Credentials for Storj
- This occurs through the [storj.io]() website
diff --git a/app/dcs/third-party-tools/velero/page.md b/app/dcs/third-party-tools/velero/page.md
index 22fcb99c2..2bc113f18 100644
--- a/app/dcs/third-party-tools/velero/page.md
+++ b/app/dcs/third-party-tools/velero/page.md
@@ -28,14 +28,14 @@ Velero lets you:
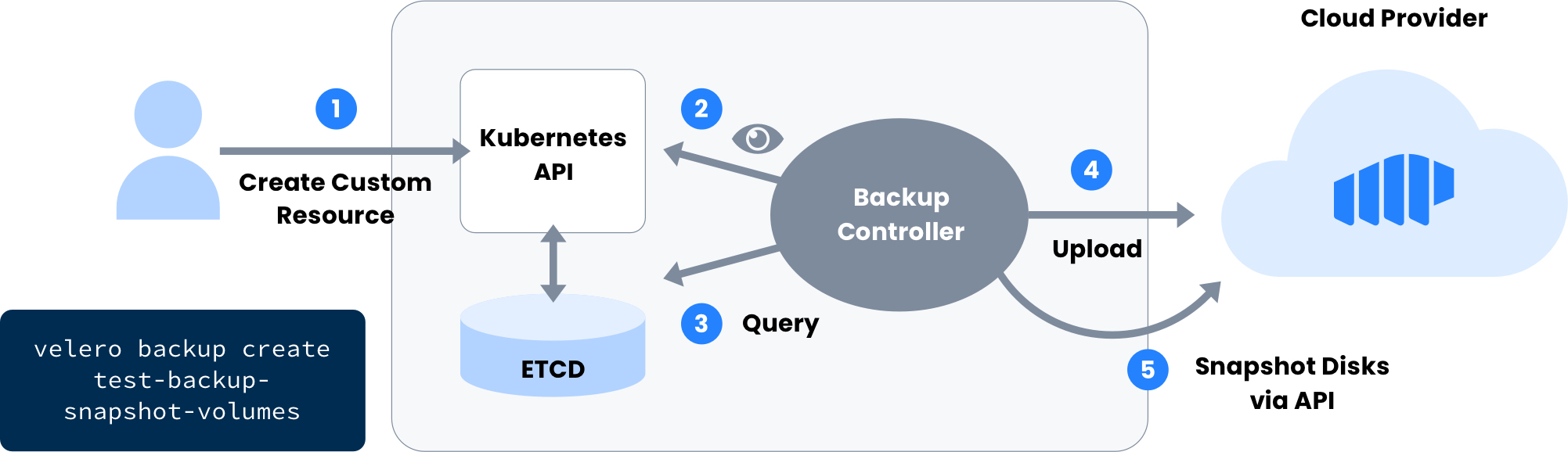
{% callout type="info" %}
-The Storj DCS Velero plugin does not support volume snapshots for now.
+The Storj Velero plugin does not support volume snapshots for now.
{% /callout %}
## Prerequisites
- [Complete Velero Prerequisites and install the CLI](https://velero.io/docs/main/basic-install/)
-- [Create a Storj DCS account](https://storj.io/signup)
+- [Create a Storj account](https://storj.io/signup)
- [](docId:OXSINcFRuVMBacPvswwNU) for the project or create an access grant with the [](docId:TbMdOGCAXNWyPpQmH6EOq)
@@ -79,7 +79,7 @@ The complete Velero documentation is [located here.](https://velero.io/docs/main
## Multicloud Architecture for Disaster Prevention and Migration
-Because Storj DCS is a globally distributed hot object store, you can store and recover your Kubernetes volumes from anywhere in the world, instantly, without having to replicate data across regions. For DevOps managers, this can mean better resilience for your cluster, reduced global RTO (recovery time objective), cost-savings, and improved native security over centralized alternatives.
+Because Storj is a globally distributed hot object store, you can store and recover your Kubernetes volumes from anywhere in the world, instantly, without having to replicate data across regions. For DevOps managers, this can mean better resilience for your cluster, reduced global RTO (recovery time objective), cost-savings, and improved native security over centralized alternatives.
In the example below, we can see a Disaster Recovery scenario where we might need to migrate into a new cluster:
diff --git a/app/dcs/third-party-tools/wordpress-site-with-updraftplus/page.md b/app/dcs/third-party-tools/wordpress-site-with-updraftplus/page.md
index 5b7bf2c83..b93137851 100644
--- a/app/dcs/third-party-tools/wordpress-site-with-updraftplus/page.md
+++ b/app/dcs/third-party-tools/wordpress-site-with-updraftplus/page.md
@@ -24,7 +24,7 @@ We will continue configuring the UpdraftPlus plugin after we have created the Ga
## Generate Gateway MT credentials
-Please sign in to your Storj DCS account **Navigate to the Access** page within your project and then click on **Create S3 Credentials**. A modal window will pop up where you should enter a name for this access grant.
+Please sign in to your Storj account **Navigate to the Access** page within your project and then click on **Create S3 Credentials**. A modal window will pop up where you should enter a name for this access grant.
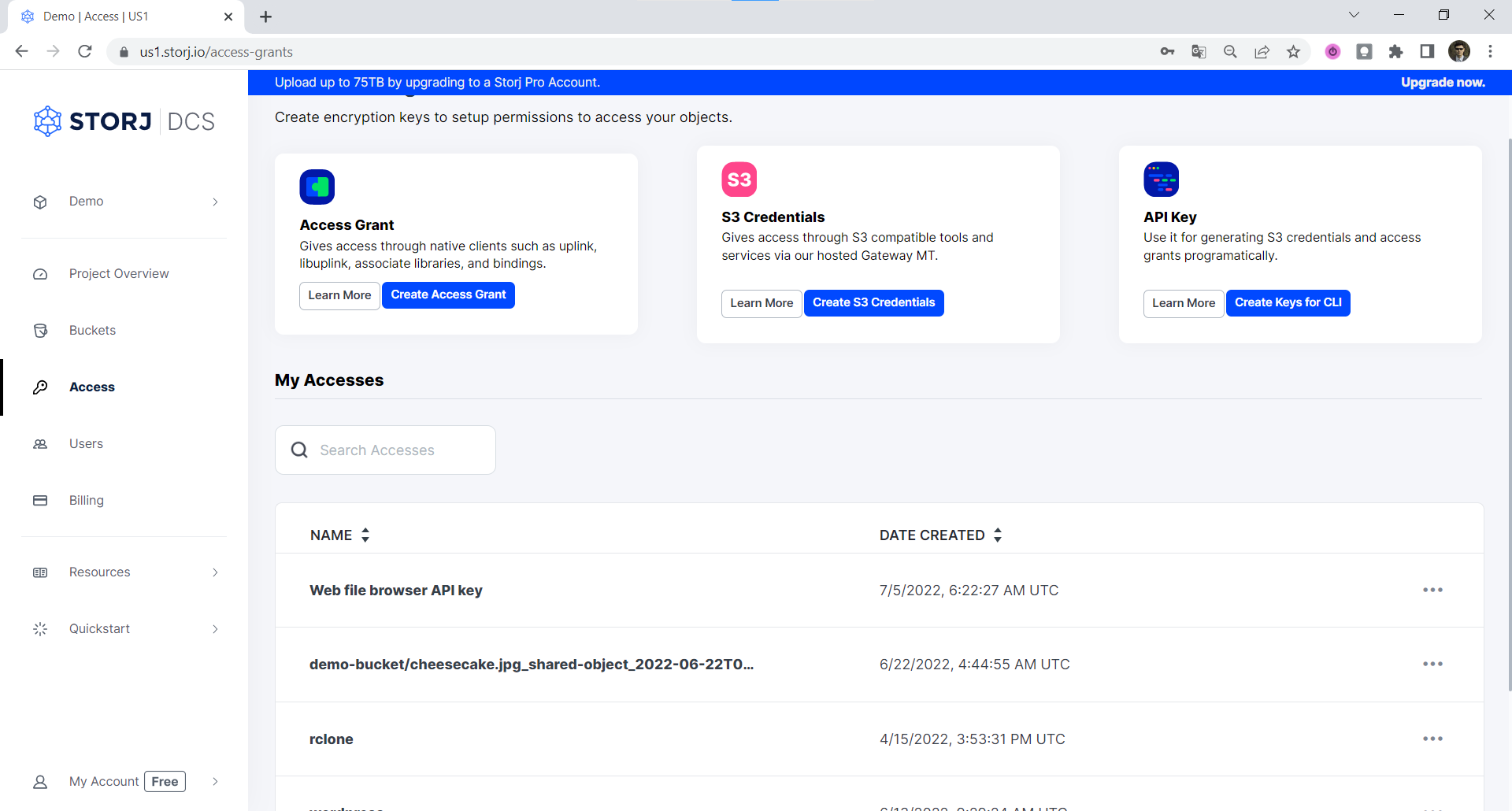
@@ -50,7 +50,7 @@ Copy your **Access Key**, **Secret Key**, and **Endpoint** to a safe location or
Now you are ready to configure **UpdraftPlus** plugin.
-## Configuring UpdraftPlus plugin to work with Storj DCS
+## Configuring UpdraftPlus plugin to work with Storj
Now that we have finished generating the Gateway MT credentials, let´s go back to the UpdraftPlus configuration. Once the plugin has been activated, you should open its settings:
@@ -74,4 +74,4 @@ Now that we have finished generating the Gateway MT credentials, let´s go back
-After you successfully configured Storj DCS as your storage back end in the **UpdraftPlus** plugin and saved your configuration, you can return back to the **_Backup / Restore_** tab to start your backup manually right away.
+After you successfully configured Storj as your storage back end in the **UpdraftPlus** plugin and saved your configuration, you can return back to the **_Backup / Restore_** tab to start your backup manually right away.
diff --git a/app/dcs/third-party-tools/zerto/page.md b/app/dcs/third-party-tools/zerto/page.md
index b6f60fe98..3b28e8d63 100644
--- a/app/dcs/third-party-tools/zerto/page.md
+++ b/app/dcs/third-party-tools/zerto/page.md
@@ -16,13 +16,13 @@ metadata:
[**Zerto**](https://www.zerto.com) brings together disaster recovery and data protection. It provides a single, scalable solution that offers simple cloud data management and protection across on-premises, hybrid, and multi-cloud environments.
-- You can use **Zerto** with **Storj DCS** S3-compatible storage.
+- You can use **Zerto** with **Storj** S3-compatible storage.
- You can download a free trial [here](https://www.zerto.com/try-or-buy/try-zerto-free/).
- Demo site: [Zerto’s Hands on Labs](https://www.zerto.com/page/labs/?z_campaign=2020_Google_Ads_Training_Labs_On_demand&z_content=Labs&z_leadsource=Google_Adwords&z_referrer=Adwords&z_source=7012I000001hzgP&gclid=CjwKCAjwj42UBhAAEiwACIhADqQ1Xo-tUPvM5qy8Pe1U2IxOnx-KBzpTQAgevDJYc42LYIXwgLIJTRoCDkUQAvD_BwE)
-## Configure Zerto to use Storj DCS
+## Configure Zerto to use Storj
Log into Zerto Virtual Manager (ZVM).
@@ -50,15 +50,15 @@ On the `New Repository` wizard screen:
- Bucket Name: enter the name of your bucket, for example, ¨demo-bucket
- - Access Key: provided in [](docId:AsyYcUJFbO1JI8-Tu8tW3) you generated with Storj DCS
+ - Access Key: provided in [](docId:AsyYcUJFbO1JI8-Tu8tW3) you generated with Storj
- - Secret Access Key: provided in [](docId:AsyYcUJFbO1JI8-Tu8tW3) you generated with Storj DCS
+ - Secret Access Key: provided in [](docId:AsyYcUJFbO1JI8-Tu8tW3) you generated with Storj
After populating all fields, click `Save`. You should now see the Storj Repo as part of your LTR repository list.
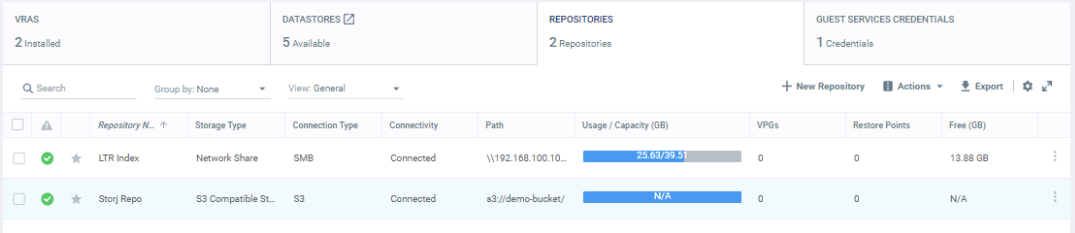
-You may optionally verify Zerto's connection via the Storj DCS website. To do so, please sign in to your Storj DCS account, click on `Buckets` on the left-hand side, then select your demo-bucket from the `Buckets` view, and provide the encryption passphrase. You will be taken to this bucket’s page, where you will see a _repository.config_ file, confirming the connection.
+You may optionally verify Zerto's connection via the Storj website. To do so, please sign in to your Storj account, click on `Buckets` on the left-hand side, then select your demo-bucket from the `Buckets` view, and provide the encryption passphrase. You will be taken to this bucket’s page, where you will see a _repository.config_ file, confirming the connection.
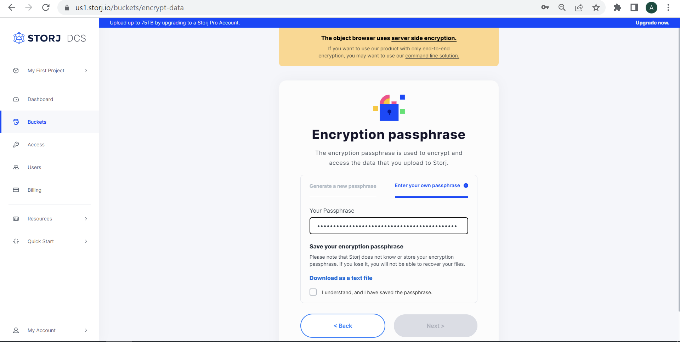
@@ -74,7 +74,7 @@ Returning to the VPG management page, click `Actions`, then `Run Retention Proce
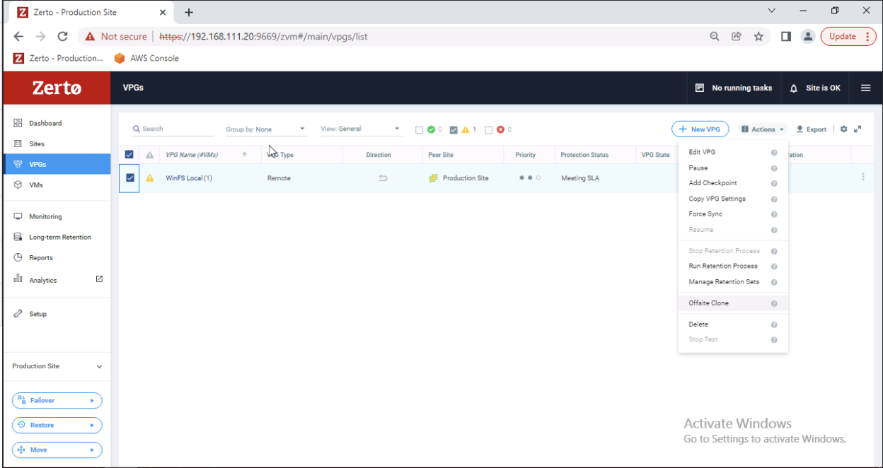
-You may return to the Storj DCS website to see a copy of the Windows File Server in the Storj demo-bucket.
+You may return to the Storj website to see a copy of the Windows File Server in the Storj demo-bucket.
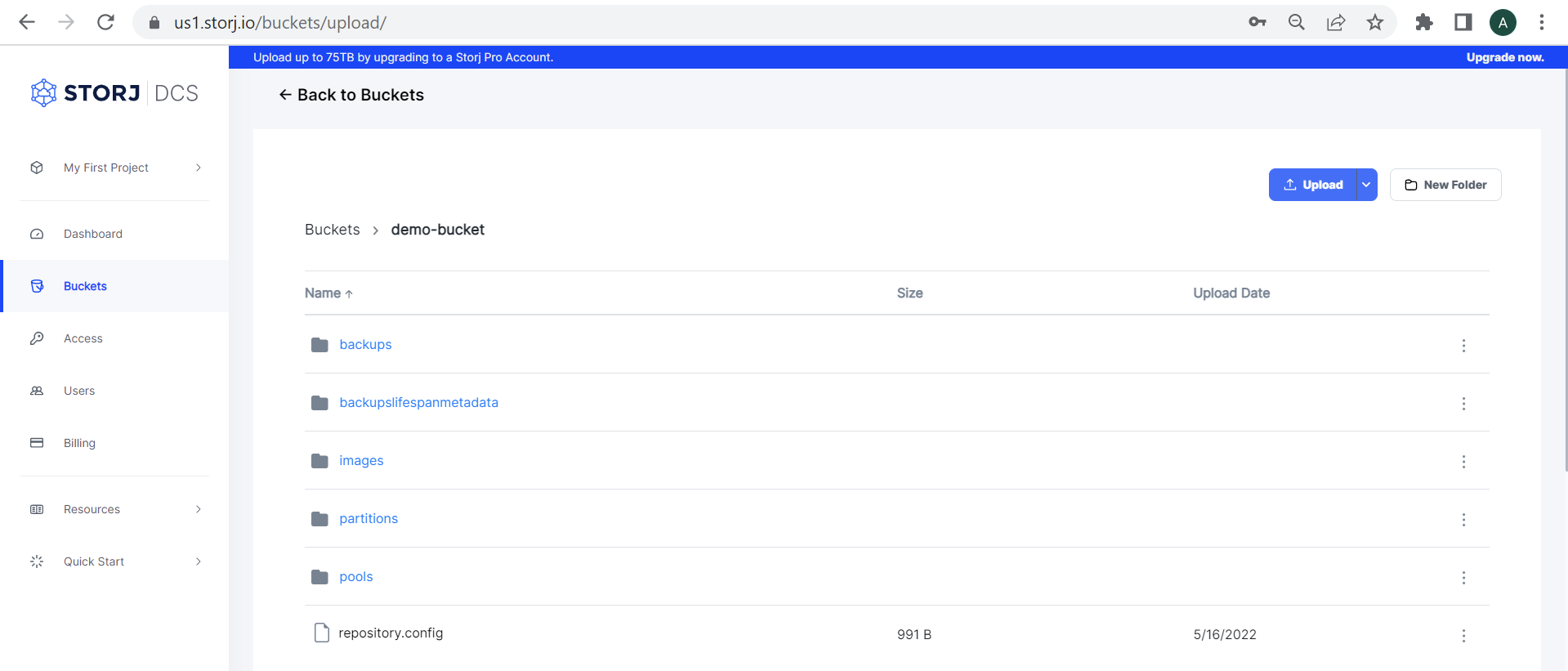
diff --git a/app/learn/concepts/access/access-grants/api-key/page.md b/app/learn/concepts/access/access-grants/api-key/page.md
index 3e057d0cf..500ec2c48 100644
--- a/app/learn/concepts/access/access-grants/api-key/page.md
+++ b/app/learn/concepts/access/access-grants/api-key/page.md
@@ -15,12 +15,12 @@ API Keys are based on Macaroons and include the capability to encode programmati
The API Key encoded into an Access Grants is based on a type of token called a Macaroon. A Macaroon is essentially a cookie with an internal structure for encoding logic, in this case, access restrictions. A Macaroon embeds the logic for the access it allows and can be restricted, simply by embedding the path restrictions and any additional restrictions within the string that represents the Macaroon. Unlike a typical cookie, a Macaroon is not a random string of bytes, but rather is an envelope with access logic encoded in it.
{% callout type="info" %}
-Storj DCS make it easy to share access to objects securely and privately. You don't need to know how to construct an API Key, but understanding how they work and what the capabilities are provide you with a better understanding of the tools Storj DCS provides you to build more private and secure applications.
+Storj make it easy to share access to objects securely and privately. You don't need to know how to construct an API Key, but understanding how they work and what the capabilities are provide you with a better understanding of the tools Storj provides you to build more private and secure applications.
{% /callout %}
## About API Keys
-For a more complete review of Macaroons, please check out [the Google paper](https://ai.google/research/pubs/pub41892). This documentation will provide enough information to effectively use the access management and object sharing functionality of Storj DCS, but is not intended to be an exhaustive explanation on the full functionality of Macaroons.
+For a more complete review of Macaroons, please check out [the Google paper](https://ai.google/research/pubs/pub41892). This documentation will provide enough information to effectively use the access management and object sharing functionality of Storj, but is not intended to be an exhaustive explanation on the full functionality of Macaroons.
Although this documentation uses the terms “API Key” and “Macaroon” interchangeably, only the term “Access Grant” is referenced on the service, through the libraries, and in the documentation. The API Key is embedded inside of an Access Grant, and is not something you need to manage separately.
diff --git a/app/learn/concepts/access/access-grants/api-key/restriction/page.md b/app/learn/concepts/access/access-grants/api-key/restriction/page.md
index 1828bcf67..6cd277101 100644
--- a/app/learn/concepts/access/access-grants/api-key/restriction/page.md
+++ b/app/learn/concepts/access/access-grants/api-key/restriction/page.md
@@ -16,7 +16,7 @@ Access restrictions are encoded into the API Key inside of an Access Grant via C
## Granular Access Control with Caveats
-Access restrictions are encoded into the API Key within and Access Grant automatically when creating an Access Grant via the Satellite Admin Console, via the CLI, or libuplink library, when using the Share command. While the possibilities for access controls that can be encoded in a Caveat are virtually unlimited, the specific Caveats supported on Storj DCS today are as follows:
+Access restrictions are encoded into the API Key within and Access Grant automatically when creating an Access Grant via the Satellite Admin Console, via the CLI, or libuplink library, when using the Share command. While the possibilities for access controls that can be encoded in a Caveat are virtually unlimited, the specific Caveats supported on Storj today are as follows:
Specific Operations: Caveats can restrict whether an Access Grant can permit any of the following operations:
diff --git a/app/learn/concepts/access/access-grants/page.md b/app/learn/concepts/access/access-grants/page.md
index 34968ff1f..1b09be7da 100644
--- a/app/learn/concepts/access/access-grants/page.md
+++ b/app/learn/concepts/access/access-grants/page.md
@@ -11,7 +11,7 @@ metadata:
and encryption or decryption.
---
-An Access Grant is a bearer token that enables applications to interact with Storj DCS to access objects stored on the service and decrypt them client-side.
+An Access Grant is a bearer token that enables applications to interact with Storj to access objects stored on the service and decrypt them client-side.
An Access Grant is a security envelope that contains a satellite address, a restricted API Key, and a set of one or more restricted prefix-based encryption keys—everything an application needs to locate an object on the network, access that object, and decrypt it.
@@ -23,7 +23,7 @@ Access Grants coordinate two parallel constructs—encryption and authorization
Access Grants are used for access management for client applications using the libuplink library, the CLI, as well as for generating credentials for the S3 compatible gateway (both the hosted GatewayMT and the self-hosted GatewayST).
{% /callout %}
-To make the implementation of these constructs as easy as possible for developers, the Storj DCS developer tools abstract the complexity of encoding objects for access management and encryption/decryption. A simple share command encapsulates an encryption key, an [](docId:XOtletuYWGeA2Om86yvwA) ( a bearer token), and the appropriate Satellite address into an encoded string called an Access Grant.
+To make the implementation of these constructs as easy as possible for developers, the Storj developer tools abstract the complexity of encoding objects for access management and encryption/decryption. A simple share command encapsulates an encryption key, an [](docId:XOtletuYWGeA2Om86yvwA) ( a bearer token), and the appropriate Satellite address into an encoded string called an Access Grant.
Access Grants can be imported easily into an Uplink client, whether it's the CLI, developer library, or a client application. Imported Access Grants are managed client-side and may be leveraged in applications via the uplink client library.
@@ -34,5 +34,5 @@ Learn how to create an Access Grant using the Satellite Admin Console in the[](d
Learn how to [](docId:OXSINcFRuVMBacPvswwNU) in the[](docId:TbMdOGCAXNWyPpQmH6EOq).
{% callout type="warning" %}
-Storj DCS satellites never come in contact with encryption keys. When you use an access grant with the CLI, libuplink library, or the self-hosted Gateway, encryption keys are managed client-side using a serialized, hierarchically derived structure for end-to-end encryption. With the cloud-hosted Gateway-MT, your data is server-side encrypted, since Storj is hosting the gateway.
+Storj satellites never come in contact with encryption keys. When you use an access grant with the CLI, libuplink library, or the self-hosted Gateway, encryption keys are managed client-side using a serialized, hierarchically derived structure for end-to-end encryption. With the cloud-hosted Gateway-MT, your data is server-side encrypted, since Storj is hosting the gateway.
{% /callout %}
diff --git a/app/learn/concepts/access/access-management-at-the-edge/page.md b/app/learn/concepts/access/access-management-at-the-edge/page.md
index 57c108f6e..cf709433c 100644
--- a/app/learn/concepts/access/access-management-at-the-edge/page.md
+++ b/app/learn/concepts/access/access-management-at-the-edge/page.md
@@ -27,15 +27,15 @@ By way of example, when a file or segment is erasure coded, it is divided into 8
If a hacker wants to obtain a complete object, they need to find at least 29 Nodes that hold a piece of each segment, compromise the security of each one (with each Node being run by different people, on different Nodes, using different firewalls, etc.). Even then, they would only have enough to reconstitute a file that is still encrypted. And, they’ll have to repeat that process for the next segment. Compare that to a situation (e.g. what was seen at Equifax a few years ago), where a simple misconfiguration gave access to hundreds of millions of individuals’ data, and you’ll see the power of this new model.
-Just storing data on Storj DCS provides significant improvements over centralized data storage in terms of reducing threat surfaces and exposure to a variety of common attack vectors. But when it comes to sharing access to data—especially highly sensitive data—developers really experience the advantages of our platform. Where we’re already seeing the most interest from partners on the combination of end-to-end encryption and the access management capabilities of our API Keys.
+Just storing data on Storj provides significant improvements over centralized data storage in terms of reducing threat surfaces and exposure to a variety of common attack vectors. But when it comes to sharing access to data—especially highly sensitive data—developers really experience the advantages of our platform. Where we’re already seeing the most interest from partners on the combination of end-to-end encryption and the access management capabilities of our API Keys.
### Separating Access and Encryption
-One of the great things about Storj DCS is that it separates the encryption function from the access management capabilities of the API Keys, allowing both to be managed 100% client-side. From a developer perspective, managing those two constructs is easy because all of the complexity is abstracted down to a few simple commands. What this enables developers to do is move access management from a centralized server to the edge.
+One of the great things about Storj is that it separates the encryption function from the access management capabilities of the API Keys, allowing both to be managed 100% client-side. From a developer perspective, managing those two constructs is easy because all of the complexity is abstracted down to a few simple commands. What this enables developers to do is move access management from a centralized server to the edge.
### Hierarchically Deterministic End-to-End Encryption
-All data stored on Storj DCS is encrypted from the client side. What that means is users control the encryption keys and the result is an extremely private and secure data store. Both the objects and the associated metadata are encrypted using randomized, salted, path-based encryption keys. The randomized keys are then encrypted with keys derived from the user’s encryption passphrase. Neither Storj nor any Storage Nodes have access to those keys, the data, or the metadata.
+All data stored on Storj is encrypted from the client side. What that means is users control the encryption keys and the result is an extremely private and secure data store. Both the objects and the associated metadata are encrypted using randomized, salted, path-based encryption keys. The randomized keys are then encrypted with keys derived from the user’s encryption passphrase. Neither Storj nor any Storage Nodes have access to those keys, the data, or the metadata.
By using hierarchically derived encryption keys, it becomes easy to share the ability to decrypt a single object or set of objects without sharing the private encryption passphrase or having to re-encrypt objects. Unlike the HD API Keys, where the hierarchy is derived from further restrictions of access, the path prefix structure of the object storage hierarchy is the foundation of the encryption structure.
@@ -43,19 +43,19 @@ A unique encryption key can be derived client-side for each object whether it’
### Access Management with API Keys
-In addition to providing the tools to share the ability to decrypt objects, Storj DCS also provides sophisticated tools for managing access to objects. Storj DCS uses hierarchically deterministic API Keys as an access management layer for objects. Similar to HD encryption keys, HD API Keys are derived from a parent API Key.
+In addition to providing the tools to share the ability to decrypt objects, Storj also provides sophisticated tools for managing access to objects. Storj uses hierarchically deterministic API Keys as an access management layer for objects. Similar to HD encryption keys, HD API Keys are derived from a parent API Key.
-Unlike the HD encryption keys where the hierarchy is derived from the path prefix structure of the object storage hierarchy, the hierarchy of API Keys is derived from the structure and relationship of access restrictions. HD API Keys embed the logic for the access it allows and can be restricted, simply by embedding the path restrictions and any additional restrictions within the string that represents the API Key. Unlike a typical API key, the Storj DCS API Key is not a random string of bytes, but rather an envelope with access logic encoded in it.
+Unlike the HD encryption keys where the hierarchy is derived from the path prefix structure of the object storage hierarchy, the hierarchy of API Keys is derived from the structure and relationship of access restrictions. HD API Keys embed the logic for the access it allows and can be restricted, simply by embedding the path restrictions and any additional restrictions within the string that represents the API Key. Unlike a typical API key, the Storj API Key is not a random string of bytes, but rather an envelope with access logic encoded in it.
### Bringing it Together with the Access
-Access management on Storj DCS requires coordination of the two parallel constructs described above—encryption and authorization. Both of these constructs work together to provide an access management framework that is secure and private, as well as extremely flexible for application developers. Both encryption and delegation of authorization are managed client-side.
+Access management on Storj requires coordination of the two parallel constructs described above—encryption and authorization. Both of these constructs work together to provide an access management framework that is secure and private, as well as extremely flexible for application developers. Both encryption and delegation of authorization are managed client-side.
While both of these constructs are managed client-side, it’s important to point out that only the API Keys are sent to the Satellite. The Satellite interprets the restrictions set by the client in the form of caveats, then controls what operations are allowed based on those restrictions. Encryption keys are never sent to the Satellite.
-Sharing access to objects stored on Storj DCS requires sending encryption and authorization information about that object from one client to another. The information is sent in a construct called an Access. An Access is a security envelope that contains a restricted HD API Key and an HD encryption key—everything an application needs to locate an object on the network, access that object, and decrypt it.
+Sharing access to objects stored on Storj requires sending encryption and authorization information about that object from one client to another. The information is sent in a construct called an Access. An Access is a security envelope that contains a restricted HD API Key and an HD encryption key—everything an application needs to locate an object on the network, access that object, and decrypt it.
-To make the implementation of these constructs as easy as possible for developers, the Storj DCS developer tools abstract the complexity of encoding objects for access management and encryption/decryption. A simple share command encapsulates both an encryption key and an API Key into an Access in the format of an encoded string that can be easily imported into an Uplink client. Imported Accesses are managed client-side and may be leveraged in applications via the Uplink client library.
+To make the implementation of these constructs as easy as possible for developers, the Storj developer tools abstract the complexity of encoding objects for access management and encryption/decryption. A simple share command encapsulates both an encryption key and an API Key into an Access in the format of an encoded string that can be easily imported into an Uplink client. Imported Accesses are managed client-side and may be leveraged in applications via the Uplink client library.
### Why Security at the Edge Matters
@@ -79,9 +79,9 @@ Distributed and decentralized environments are designed to eliminate trust by de
### A Different Approach Delivers Differentiated Value Out-of-the-box
-Storj DCS’s distributed cloud storage and edge-based security model provide easy tools for building applications that are more private, more secure, and less susceptible to the range of common attacks. With this approach, no incompetent or malicious operator can undermine security. By embracing decentralization and security at the edge, the system is architected to be resilient. Unlike other cloud storage providers, like the AWS Detective solution, Storj DCS integrates security features which are enabled by default. With Storj DCS, you don’t pay extra for security and privacy.
+Storj’s distributed cloud storage and edge-based security model provide easy tools for building applications that are more private, more secure, and less susceptible to the range of common attacks. With this approach, no incompetent or malicious operator can undermine security. By embracing decentralization and security at the edge, the system is architected to be resilient. Unlike other cloud storage providers, like the AWS Detective solution, Storj integrates security features which are enabled by default. With Storj, you don’t pay extra for security and privacy.
-**Reduced Risk** - Common attacks (misconfigured access control lists, leaky buckets, insider threats, honeypots, man-in-the-middle attacks, etc.) depend for their success on breaching a central repository of access controls or gaining access to a treasure trove of data. The Storj DCS security model provides a way to architect out whole categories of typical application attack vectors.
+**Reduced Risk** - Common attacks (misconfigured access control lists, leaky buckets, insider threats, honeypots, man-in-the-middle attacks, etc.) depend for their success on breaching a central repository of access controls or gaining access to a treasure trove of data. The Storj security model provides a way to architect out whole categories of typical application attack vectors.
**Reduced Threat Surface** - By separating trust boundaries and distributing access management and storage functions, a significant percentage of the typical application threat surfaces is either eliminated or made orders of magnitude more complex to attack.
diff --git a/app/learn/concepts/access/access-revocation/page.md b/app/learn/concepts/access/access-revocation/page.md
index 72b4bf1bc..0552ab2d0 100644
--- a/app/learn/concepts/access/access-revocation/page.md
+++ b/app/learn/concepts/access/access-revocation/page.md
@@ -11,11 +11,11 @@ metadata:
adding it to the Revocation service.
---
-Storj DCS provides an easy way to revoke client-side delegated authorization with hierarchically deterministic API keys
+Storj provides an easy way to revoke client-side delegated authorization with hierarchically deterministic API keys
While delegated authorization and the ability to generate Access Grants at the edge provides the opportunity to create more private and secure applications, there are design considerations to take into account when building applications with data sharing capabilities based on long-lived bearer tokens.
-While it is possible to create Access Grants with time-based restrictions and to required Access Grants be refreshed as they expire, applications must be able to revoke access to data. Access grant revocation is supported on Storj DCS in two ways:
+While it is possible to create Access Grants with time-based restrictions and to required Access Grants be refreshed as they expire, applications must be able to revoke access to data. Access grant revocation is supported on Storj in two ways:
1. Deleting a primary Access Grant - from the Satellite Admin Console, it is possible to delete a primary Access Grant. Deleting a primary Access Grant also immediately invalidates all child Restricted Access Grants derived from that primary Access Grant.
diff --git a/app/learn/concepts/access/capability-based-access-control/page.md b/app/learn/concepts/access/capability-based-access-control/page.md
index 602218a4f..0bf2a80e0 100644
--- a/app/learn/concepts/access/capability-based-access-control/page.md
+++ b/app/learn/concepts/access/capability-based-access-control/page.md
@@ -27,8 +27,8 @@ Those coming from the Blockchain world will be very familiar with the capability
This gives the client-user full insight into their privilege set, illustrating the core tenet of the Capability Mindset: “[don’t separate designation from authority.](https://crypto.stanford.edu/cs155old/cs155-spring09/papers/ConfusedDeputy.html)”.
-Similar to how in the Blockchain world, “your keys are your money,” with Storj DCS, your keys are your data, and access grants add additional capabilities that allow the owners of data to caveat it, or granularly delegate access for sharing, programmatically.
+Similar to how in the Blockchain world, “your keys are your money,” with Storj, your keys are your data, and access grants add additional capabilities that allow the owners of data to caveat it, or granularly delegate access for sharing, programmatically.
Key-based ownership of object data will enable users to intuitively control their data as a first principle, and then delegate it as they see fit. The decentralized cloud eliminates the increasingly apparent risk of data loss/extortion due to holding data on one single provider (like Amazon, Google, or Microsoft).
-Storj DCS presents a better model where object data is encrypted, erasure-coded, and spread across thousands of nodes stratified by reputation whereby any and every computer can be the cloud.
+Storj presents a better model where object data is encrypted, erasure-coded, and spread across thousands of nodes stratified by reputation whereby any and every computer can be the cloud.
diff --git a/app/learn/concepts/access/encryption-and-keys/key-management/page.md b/app/learn/concepts/access/encryption-and-keys/key-management/page.md
index bccb3f3ca..802ff1311 100644
--- a/app/learn/concepts/access/encryption-and-keys/key-management/page.md
+++ b/app/learn/concepts/access/encryption-and-keys/key-management/page.md
@@ -14,7 +14,7 @@ End-to-end encryption means that you are responsible for creating and maintainin
## A Word of Caution on encryption keys
-At several points in the Documentation it’s important to point out three important things about your encryption keys. Please make sure you clearly understand how encryption keys are used on Storj DCS. You, your application and/or your users are responsible for managing your encryption keys.
+At several points in the Documentation it’s important to point out three important things about your encryption keys. Please make sure you clearly understand how encryption keys are used on Storj. You, your application and/or your users are responsible for managing your encryption keys.
{% callout type="info" %}
If you lose your encryption keys, you have lost the ability to decrypt your data rendering it useless.
@@ -22,17 +22,17 @@ If you lose your encryption keys, you have lost the ability to decrypt your data
## Thing 1: Your encryption keys are your data
-Storj DCS does not have access to your encryption keys. If you lose your encryption keys, they are gone. If you can’t decrypt your data, you’ve effectively lost it. All of it.
+Storj does not have access to your encryption keys. If you lose your encryption keys, they are gone. If you can’t decrypt your data, you’ve effectively lost it. All of it.
### Thing 2: Make sure you backup your encryption keys
-It is very important you make sure to backup your encryption keys in a safe place. Storj DCS does not have any features or functions to back up encryption keys. We have a reference implementation of a user interface to ensure a user has backed up their encryption keys, but all of that happens client-side.
+It is very important you make sure to backup your encryption keys in a safe place. Storj does not have any features or functions to back up encryption keys. We have a reference implementation of a user interface to ensure a user has backed up their encryption keys, but all of that happens client-side.
### Thing 3: Secure your encryption keys
This probably goes without saying, but be careful with how your app stores and transmits encryption keys.
-By keeping encryption and access management separate, and by implementing client-side encryption, Storj DCS ensures that your data can’t be processed, mined, scanned by Storj or any unauthorized 3rd parties. If you don’t, it will end badly and Storj won’t be able to help.
+By keeping encryption and access management separate, and by implementing client-side encryption, Storj ensures that your data can’t be processed, mined, scanned by Storj or any unauthorized 3rd parties. If you don’t, it will end badly and Storj won’t be able to help.
### Thing 4: Choose complex encryption passphrases.
diff --git a/app/learn/concepts/decentralization/coordination-avoidance/page.md b/app/learn/concepts/decentralization/coordination-avoidance/page.md
index 5438eef73..30b5527b4 100644
--- a/app/learn/concepts/decentralization/coordination-avoidance/page.md
+++ b/app/learn/concepts/decentralization/coordination-avoidance/page.md
@@ -17,7 +17,7 @@ Rather than coming to a global consensus around the entire state of the network
## Advantages Over Coordination-dependant Systems
-By ensuring coordination avoidance within Storj DCS, we’re able to deliver better performance and scalability over other decentralized systems—two issues that are critical to achieving broad adoption with traditional storage users. Decentralized systems that are coordination dependent, like Bitcoin, require an increasing number of resources as they scale. To compete with centralized cloud storage platforms like Amazon S3, Microsoft Azure, and Google Cloud, Storj DCS must be able to scale into the exabyte range, and beyond—something we feel confident it will be able to achieve.
+By ensuring coordination avoidance within Storj, we’re able to deliver better performance and scalability over other decentralized systems—two issues that are critical to achieving broad adoption with traditional storage users. Decentralized systems that are coordination dependent, like Bitcoin, require an increasing number of resources as they scale. To compete with centralized cloud storage platforms like Amazon S3, Microsoft Azure, and Google Cloud, Storj must be able to scale into the exabyte range, and beyond—something we feel confident it will be able to achieve.
We believe our approach of decentralizing both storage and metadata tiers in the network allows greater scalability, performance, and reliability than systems that rely on seeking consensus.
@@ -25,10 +25,10 @@ We believe our approach of decentralizing both storage and metadata tiers in the
Blockchain consensus offers very strong guarantees, but this comes at a heavy cost in coordination overhead. Coordination is not always necessary for correctness and minimizing coordination is key to maximizing scalability, availability, and high performance in database systems. One fundamental design decision of the Storj network was not to utilize blockchain consensus for file transfers to increase those properties of the Storj network. Storj takes a pragmatic approach to avoiding blockchain consensus while still maintaining correctness for file transfers. But, at the same time by default, Storj uses blockchain consensus with the Ethereum-based STORJ token for payment processing to storage node operators.
-Storj DCS is an enterprise, production-ready version of the Storj network, complete with guaranteed SLAs. All user uploads and downloads on Storj DCS uses metainformation from Storj DCS [Satellites which are special nodes on the network that audit storage nodes](https://storj.io/blog/2018/12/decentralized-auditing-and-repair-the-low-key-life-of-data-resurrection/) and ensure Storage Nodes properly storing files and managing metadata for users storing data on the network.
+Storj is an enterprise, production-ready version of the Storj network, complete with guaranteed SLAs. All user uploads and downloads on Storj uses metainformation from Storj [Satellites which are special nodes on the network that audit storage nodes](https://storj.io/blog/2018/12/decentralized-auditing-and-repair-the-low-key-life-of-data-resurrection/) and ensure Storage Nodes properly storing files and managing metadata for users storing data on the network.
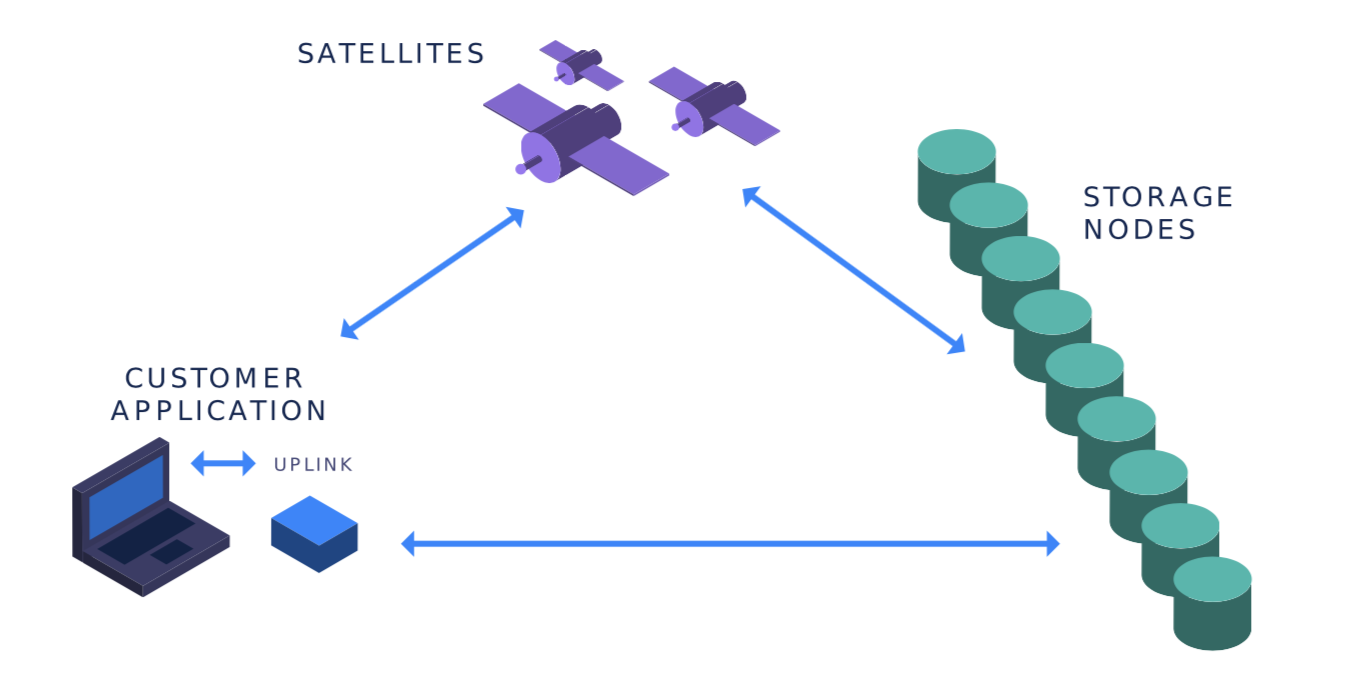
As shown in the above architecture, there are three primary peer classes within the Storj network. All are open source, and capable of being run by any third party, making the network architecture fundamentally decentralized.
-The Storj network can leverage the decentralized nature of storage nodes and Satellites to create partitions in the network to isolate users and file transfers from each other, which helps minimize coordination across the Storj network. For extremely high throughput demands, organizations can run their own Satellite. This avoids coordination overhead with the rest of Storj DCS and allows users to make their own decisions about what database infrastructure their Satellite will use and relax consistency guarantees if they wish.
+The Storj network can leverage the decentralized nature of storage nodes and Satellites to create partitions in the network to isolate users and file transfers from each other, which helps minimize coordination across the Storj network. For extremely high throughput demands, organizations can run their own Satellite. This avoids coordination overhead with the rest of Storj and allows users to make their own decisions about what database infrastructure their Satellite will use and relax consistency guarantees if they wish.
diff --git a/app/learn/concepts/decentralization/page.md b/app/learn/concepts/decentralization/page.md
index c54cc893f..a322ce878 100644
--- a/app/learn/concepts/decentralization/page.md
+++ b/app/learn/concepts/decentralization/page.md
@@ -13,7 +13,7 @@ metadata:
storage option.
---
-Decentralized data storage means more security and privacy. Decentralized cloud storage is more difficult to attack than traditional centralized data. On a decentralized network, files are broken apart and spread across multiple nodes. Storj DCS uses Erasure Coding to distribute file pieces over many nodes located in different physical locations around the world.
+Decentralized data storage means more security and privacy. Decentralized cloud storage is more difficult to attack than traditional centralized data. On a decentralized network, files are broken apart and spread across multiple nodes. Storj uses Erasure Coding to distribute file pieces over many nodes located in different physical locations around the world.
There are more than a number of reasons why you may wish to utilize **decentralized storage** over legacy alternatives, namely:
@@ -35,12 +35,12 @@ Our decentralization goals for fundamental infrastructure, such as storage, are
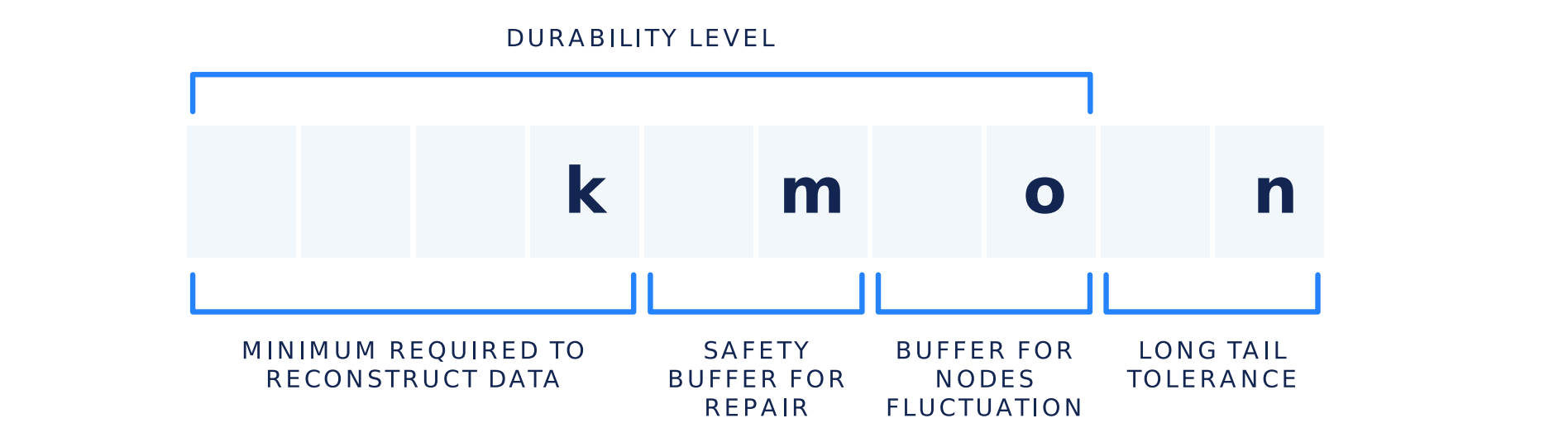
-You can learn more about erasure codes in Storj DCS under the [](docId:CBMEVO2vA2lDZ_BVuZ9aP) section under Concepts.
+You can learn more about erasure codes in Storj under the [](docId:CBMEVO2vA2lDZ_BVuZ9aP) section under Concepts.
**Data Repair** is necessary when the number of available pieces of a file still held on the network approaches the minimum threshold below which it would become impossible to recover the file. When we reach this threshold, the network will proceed to repair the data in such a way that the number of available pieces is always big enough to prevent the file from becoming irretrievable.
-You can learn more about data repair in Storj DCS under the [](docId:z4JgCuivlGbnn4YQMmlVX) section under Concepts.
+You can learn more about data repair in Storj under the [](docId:z4JgCuivlGbnn4YQMmlVX) section under Concepts.
-**File Audit** is the action of testing if a random piece can successfully be retrieved from a node that is storing it. File Audits are continually applied to assure the durability of the files on Storj DCS. The audit service is a highly scalable and performant analog to the consensus mechanism, typically a distributed ledger, used in other decentralized storage services.
+**File Audit** is the action of testing if a random piece can successfully be retrieved from a node that is storing it. File Audits are continually applied to assure the durability of the files on Storj. The audit service is a highly scalable and performant analog to the consensus mechanism, typically a distributed ledger, used in other decentralized storage services.
****
diff --git a/app/learn/concepts/definitions/page.md b/app/learn/concepts/definitions/page.md
index d35658e09..9e916d9fc 100644
--- a/app/learn/concepts/definitions/page.md
+++ b/app/learn/concepts/definitions/page.md
@@ -11,7 +11,7 @@ metadata:
related to encryption, erasure coding, and client-side technologies.
---
-The Storj DCS service uses an array of different technologies such as strong encryption and erasure codes to ensure a differentiated level of privacy and security across a network of peer classes. Some of the terms we use may be familiar and some may be new, but if you see a word you don't recognize or see a familiar word in a different context, you'll probably find a useful definition here:
+The Storj service uses an array of different technologies such as strong encryption and erasure codes to ensure a differentiated level of privacy and security across a network of peer classes. Some of the terms we use may be familiar and some may be new, but if you see a word you don't recognize or see a familiar word in a different context, you'll probably find a useful definition here:
1. **Peer Class** A cohesive collection of network services and responsibilities. There are three different peer classes that represent services in our network: storage nodes, Uplinks, and Satellites.
@@ -23,15 +23,15 @@ The Storj DCS service uses an array of different technologies such as strong enc
2. **Gateway** A service which provides a compatibility layer between other object storage services such as Amazon S3 and libuplink exposing an Amazon S3-compatible API.
- 1. **Gateway ST -** a single-tenant, self-hosted S3-compatible gateway service provided as part of the Storj DCS developer tools/SDK
+ 1. **Gateway ST -** a single-tenant, self-hosted S3-compatible gateway service provided as part of the Storj developer tools/SDK
- 2. **Gateway MT** **-** a multi-tenant, multi-region, cloud-hosted S3-compatible gateway service provided as part of the Storj DCS service. We consider this service server-side encrypted instead of end-to-end encrypted because this service temporarily manages encryption for you. While more complex, this can be run on your own infrastructure.
+ 2. **Gateway MT** **-** a multi-tenant, multi-region, cloud-hosted S3-compatible gateway service provided as part of the Storj service. We consider this service server-side encrypted instead of end-to-end encrypted because this service temporarily manages encryption for you. While more complex, this can be run on your own infrastructure.
3. **Linksharing/webhosting -** a gateway for standard HTTP requests, so you can share objects with users via a web browser or even host full websites. This can also be run on your own infrastructure if preferred.
3. **Uplink** **CLI** A command line interface for uploading and downloading files from the network, managing permissions and sharing, and managing accounts.
-4. **Satellite** - A peer class and one of the primary components of the Storj network. The satellite participates in the node discovery system, caches node address information, stores per-object metadata, maintains storage node reputation, aggregates billing data, pays storage nodes, performs audits and repair, and manages authorization and user accounts. Users have accounts on and trust specific Satellites. Any user can run their own Satellite, but we expect many users to elect to avoid the operational complexity and create an account on another Satellite hosted by a trusted third party such as Storj Labs, a friend, group, or workplace. Storj Labs satellites are operated under the Storj DCS brand. This component has a couple of main responsibilities:
+4. **Satellite** - A peer class and one of the primary components of the Storj network. The satellite participates in the node discovery system, caches node address information, stores per-object metadata, maintains storage node reputation, aggregates billing data, pays storage nodes, performs audits and repair, and manages authorization and user accounts. Users have accounts on and trust specific Satellites. Any user can run their own Satellite, but we expect many users to elect to avoid the operational complexity and create an account on another Satellite hosted by a trusted third party such as Storj Labs, a friend, group, or workplace. Storj Labs satellites are operated under the Storj brand. This component has a couple of main responsibilities:
1. developer account registration & management,
@@ -43,7 +43,7 @@ The Storj DCS service uses an array of different technologies such as strong enc
5. garbage collection & other chores.
-5. **Satellite Developer Account** - Basic information about users is stored and used to allow users to access Storj DCS. User account data includes user name, email, password, and payment methods. User account data is not client-side encrypted so that it may be rendered in the satellite user interface.
+5. **Satellite Developer Account** - Basic information about users is stored and used to allow users to access Storj. User account data includes user name, email, password, and payment methods. User account data is not client-side encrypted so that it may be rendered in the satellite user interface.
6. **Strong Encryption** - a strong encryption algorithm is one that can guarantee the confidentiality of sensitive data. The time and cost of the compute resources required to decrypt data encrypted via a strong encryption method is either not possible, feasible, or economically justifiable, within the usable lifespan of the data.
@@ -65,7 +65,7 @@ The Storj DCS service uses an array of different technologies such as strong enc
4. **Object or file** - An object (or file) is the main data type in our system. An object is referred to by an object key, contains an arbitrary amount of bytes, and has no minimum or maximum size. An object is represented by an ordered collection of one or more segments. Segments have a fixed maximum size. An object also supports a limited amount of key/value user- defined fields in which to store user metadata. Like object keys, the object data is client-side encrypted.
- 5. **Segment** - A segment represents a single array of bytes, between 0 and a system-configurable maximum segment size. The max Segment size on Storj DCS Satellites is 64MB. An object smaller than 64MB is stored as one segment. Objects larger than 64MB are stored in multiple 64MB Segments. Each Segment is stored as pieces on the network. Only a subset of pieces of the total are required to reconstitute a Segment. All Segments are required to reconstitute an Object. Segment data is client-side encrypted.
+ 5. **Segment** - A segment represents a single array of bytes, between 0 and a system-configurable maximum segment size. The max Segment size on Storj Satellites is 64MB. An object smaller than 64MB is stored as one segment. Objects larger than 64MB are stored in multiple 64MB Segments. Each Segment is stored as pieces on the network. Only a subset of pieces of the total are required to reconstitute a Segment. All Segments are required to reconstitute an Object. Segment data is client-side encrypted.
1. **Remote Segment** - A remote segment is a segment that will be erasure encoded and distributed across the network. A remote segment is larger than the metadata required to keep track of its bookkeeping, which includes information such as the IDs of the nodes that the data is stored on. Remote segment data is client-side encrypted.
@@ -99,7 +99,7 @@ The Storj DCS service uses an array of different technologies such as strong enc
4. **_n_ = 130** – The number of pieces an Uplink attempts to upload to diverse Storage Nodes when uploading a Segment.
-13. **Multipart Upload** Multipart Upload is a function that allows large files to be broken up into smaller pieces for more efficient uploads. When an object is uploaded using Multipart Upload, a file is first broken into parts, each part of a Multipart Upload is also stored as one or more Segments. With Multipart Upload, a single object is uploaded as a set of parts. Each part is an integral portion of the data comprising the object. The object parts may be uploaded independently, in parallel, and in any order. Uploads may be paused and resumed by uploading an initial set of parts, then resuming and uploading the remaining parts. If the upload of any part fails, that part may be re-uploaded without impacting the upload of other parts. All of these parts are broken into one or more Segments by the Storj DCS Gateway based on whether the Part Size is smaller or larger than the default Segment size. While Multipart Upload is most appropriate for files larger than the 64MB default Segment size, the Part Size is configurable in applications that use Multipart Upload.
+13. **Multipart Upload** Multipart Upload is a function that allows large files to be broken up into smaller pieces for more efficient uploads. When an object is uploaded using Multipart Upload, a file is first broken into parts, each part of a Multipart Upload is also stored as one or more Segments. With Multipart Upload, a single object is uploaded as a set of parts. Each part is an integral portion of the data comprising the object. The object parts may be uploaded independently, in parallel, and in any order. Uploads may be paused and resumed by uploading an initial set of parts, then resuming and uploading the remaining parts. If the upload of any part fails, that part may be re-uploaded without impacting the upload of other parts. All of these parts are broken into one or more Segments by the Storj Gateway based on whether the Part Size is smaller or larger than the default Segment size. While Multipart Upload is most appropriate for files larger than the 64MB default Segment size, the Part Size is configurable in applications that use Multipart Upload.
1. **Part** - a single piece of an object that has been separated into multiple piece during a MultiPart Upload.
@@ -107,7 +107,7 @@ The Storj DCS service uses an array of different technologies such as strong enc
15. **Value Attribution** Through our partner program, we offer a variety of programs for partners who refer business to us. We track referrals using Value Attribution.
- 1. **Value Attribution Code** Partners have a code that is passed by and to a User Agent to track Storj DCS usage associated with a partner's application.
+ 1. **Value Attribution Code** Partners have a code that is passed by and to a User Agent to track Storj usage associated with a partner's application.
16. **Encryption-related Terms**
@@ -131,7 +131,7 @@ The Storj DCS service uses an array of different technologies such as strong enc
17. **Access Management-related Terms**
- 1. **Access Grant:** An encoded string that contains an API Key, an Encryption store, and the address of the Satellite storing the object metadata for the purpose of sharing access to objects stored on Storj DCS.
+ 1. **Access Grant:** An encoded string that contains an API Key, an Encryption store, and the address of the Satellite storing the object metadata for the purpose of sharing access to objects stored on Storj.
2. **API Key**: A string generated for a project to authorize access management to data on the service. The API key is an authorization token based on an implementation called macaroons and is sent to the Satellite in order to authorize requests.
diff --git a/app/learn/concepts/edge-services/page.md b/app/learn/concepts/edge-services/page.md
index c056e02d0..d762cabbc 100644
--- a/app/learn/concepts/edge-services/page.md
+++ b/app/learn/concepts/edge-services/page.md
@@ -25,7 +25,7 @@ The three components comprising the edge services are:
**S3 Compatible Gateway**
-Storj DCS includes a globally distributed, multi-region cloud-hosted [](docId:yYCzPT8HHcbEZZMvfoCFa).
+Storj includes a globally distributed, multi-region cloud-hosted [](docId:yYCzPT8HHcbEZZMvfoCFa).
**Linkshare Service**
diff --git a/app/learn/concepts/encryption-key/how-encryption-is-implemented/page.md b/app/learn/concepts/encryption-key/how-encryption-is-implemented/page.md
index 8301fe82f..2d61529e0 100644
--- a/app/learn/concepts/encryption-key/how-encryption-is-implemented/page.md
+++ b/app/learn/concepts/encryption-key/how-encryption-is-implemented/page.md
@@ -13,7 +13,7 @@ metadata:
Strong encryption is essential when data is stored on a network of storage nodes operated by 3rd parties
-## Ensuring the Privacy and Security of Data on Storj DCS
+## Ensuring the Privacy and Security of Data on Storj
All data stored on the distributed and decentralized network of storage nodes and all metadata stored on Satellites is encrypted.
@@ -65,7 +65,7 @@ Each segment has metadata associated with it on the Satellite. Segment metadata
The last segment’s metadata contains information in addition to the encrypted key and key nonce. The additional information is the metadata for the entire file. Some of this metadata is unencrypted, such as encryption type (AES-GCM or Secretbox) and encryption block size, since they are necessary to properly decrypt the file and metadata. The remainder of the metadata, which includes the number of segments, segment size, last segment size, and additional arbitrary metadata is encrypted with the last segment’s random content encryption key.
-In summary, encryption and security on decentralized cloud storage networks has been carefully thought out to enable the sharing of files without compromising entire buckets of data. Cloud storage platforms must have the ability to easily share data for deployments like CDNs, websites and other use-cases. By deriving keys hierarchically from file paths, and encrypting data with different keys, Storj DCS maintains data privacy without removing important features.
+In summary, encryption and security on decentralized cloud storage networks has been carefully thought out to enable the sharing of files without compromising entire buckets of data. Cloud storage platforms must have the ability to easily share data for deployments like CDNs, websites and other use-cases. By deriving keys hierarchically from file paths, and encrypting data with different keys, Storj maintains data privacy without removing important features.
This description pulls heavily from Moby von Briesen's blog post, located here:
diff --git a/app/learn/concepts/encryption-key/page.md b/app/learn/concepts/encryption-key/page.md
index fa5d8f5cf..46d6762bc 100644
--- a/app/learn/concepts/encryption-key/page.md
+++ b/app/learn/concepts/encryption-key/page.md
@@ -10,10 +10,10 @@ metadata:
and applications for enhanced application privacy and security.
---
-This section describes the encryption mechanisms used on Storj DCS and describes supported approaches to data and metadata encryption.
+This section describes the encryption mechanisms used on Storj and describes supported approaches to data and metadata encryption.
-Separate and distinct from the topic of access management, a number of different levels and applications of strong encryption are applied throughout the Storj DCS service. Within the encryption paradigm, there are design choices that impact the level of privacy and security of an application.
+Separate and distinct from the topic of access management, a number of different levels and applications of strong encryption are applied throughout the Storj service. Within the encryption paradigm, there are design choices that impact the level of privacy and security of an application.
{% callout type="info" %}
-**Key Point:** Storj DCS provides several approaches to developing more secure and private applications and your choice of integration pattern will allow you to make an informed decision on the right type of encryption to provide the commensurate level of privacy and security for your application data.
+**Key Point:** Storj provides several approaches to developing more secure and private applications and your choice of integration pattern will allow you to make an informed decision on the right type of encryption to provide the commensurate level of privacy and security for your application data.
{% /callout %}
diff --git a/app/learn/concepts/immutability/page.md b/app/learn/concepts/immutability/page.md
index 4a4b1a77b..bd78ff1cf 100644
--- a/app/learn/concepts/immutability/page.md
+++ b/app/learn/concepts/immutability/page.md
@@ -58,7 +58,7 @@ While enabling MFA on privileged accounts is the industry norm and best practice
While it is important to secure privileged user accounts, by far the most common attack vector on cloud storage repositories are credential-based attacks. Credentials created for applications to interact with cloud storage are frequently embedded in application configurations in SaaS applications or installed applications on servers. If those Saas applications or hardware devices are compromised and a bad actor is able to access a credential, that bad actor may do whatever the credential is authorized to do. In all cases, the bad actor will attempt to escalate the privileges associated with the credential, either by bypassing additional environmental restrictions such as security policies on a specific environment or using the credential in a different application, environment or security context. Moreover, where the implementation of security controls requires a high level of complexity, users frequently choose not to implement the full spectrum of security options due to the high level of friction introduced into development lifecycles.
-Storj significantly simplifies the process of securing credentials and restricting the attack surface through the use of API Keys based on Macaroons. Access restrictions are encoded into API Keys within and Access Grant automatically upon creation via the Satellite Admin Console, via the CLI, or libuplink library, when using the Share command. While the possibilities for access controls that can be encoded in a Caveat are virtually unlimited, the specific Caveats supported on Storj DCS today are as follows:
+Storj significantly simplifies the process of securing credentials and restricting the attack surface through the use of API Keys based on Macaroons. Access restrictions are encoded into API Keys within and Access Grant automatically upon creation via the Satellite Admin Console, via the CLI, or libuplink library, when using the Share command. While the possibilities for access controls that can be encoded in a Caveat are virtually unlimited, the specific Caveats supported on Storj today are as follows:
**Specific Operations:** Caveats can restrict whether an Access Grant can permit any of the following operations:
diff --git a/app/learn/concepts/key-architecture-constructs/page.md b/app/learn/concepts/key-architecture-constructs/page.md
index 9caa6c1d0..f4abb2e05 100644
--- a/app/learn/concepts/key-architecture-constructs/page.md
+++ b/app/learn/concepts/key-architecture-constructs/page.md
@@ -11,15 +11,15 @@ metadata:
secure and private applications on Storj.
---
-Developing applications on Storj DCS require a basic familiarity with the basic constructs of the service.
+Developing applications on Storj require a basic familiarity with the basic constructs of the service.
-At a high level, object storage is a well-understood technology with established vendors and standards for integration. Storj DCS brings a number of new capabilities to make it easy for developers to build more secure and private applications and, as with any new and disruptive technology, the key to maximizing the potential value of that technology is understanding how that technology can be practically applied to solve real-world problems.
+At a high level, object storage is a well-understood technology with established vendors and standards for integration. Storj brings a number of new capabilities to make it easy for developers to build more secure and private applications and, as with any new and disruptive technology, the key to maximizing the potential value of that technology is understanding how that technology can be practically applied to solve real-world problems.
-This section will orient you to some of the main constructs within the service and describes how to use Storj DCS in your application.
+This section will orient you to some of the main constructs within the service and describes how to use Storj in your application.
## But first, a word on information architecture...
-It's important to understand the constructs of Storj DCS so that an application storing data is optimized depending on the requirements for privacy, access control, sharing, etc. The main constructs to understand are shown in the figure below:
+It's important to understand the constructs of Storj so that an application storing data is optimized depending on the requirements for privacy, access control, sharing, etc. The main constructs to understand are shown in the figure below:
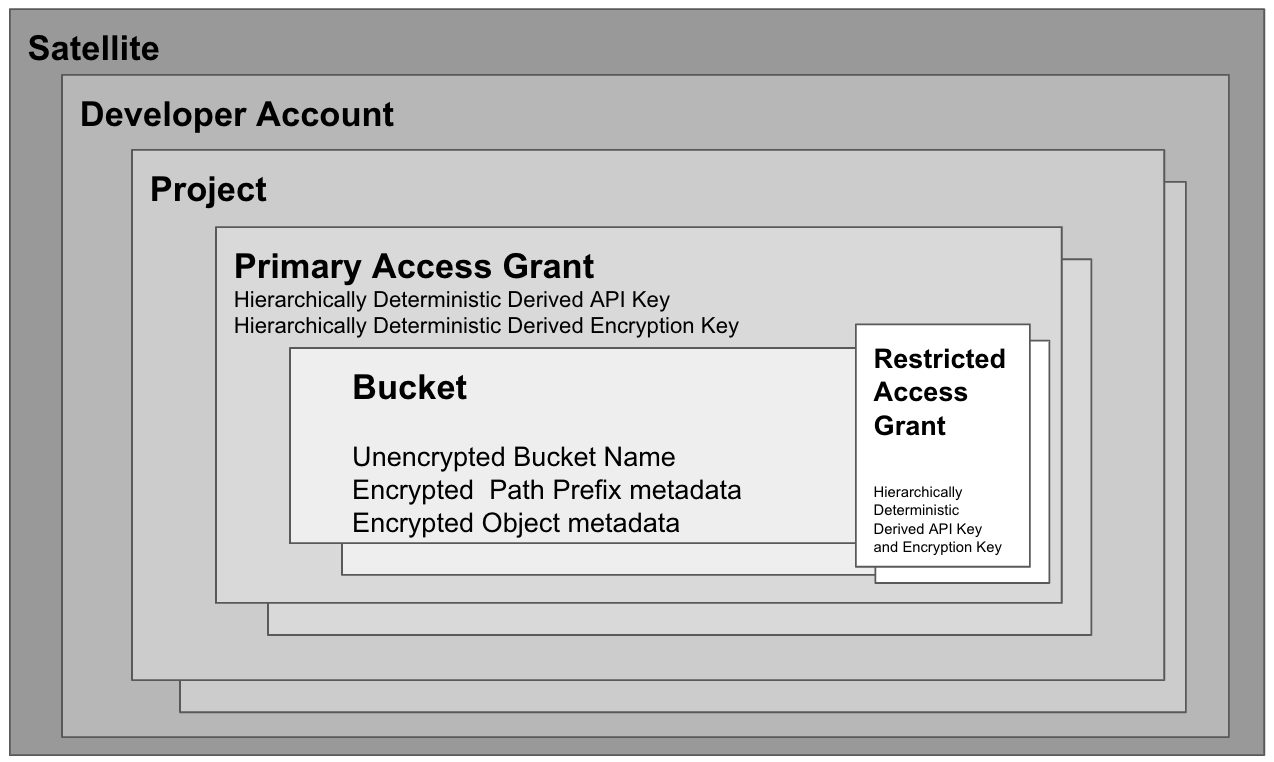
@@ -71,7 +71,7 @@ A bucket is an unbounded but named collection of objects identified by paths. Ev
Bucket names are not client-side encrypted so that they may be rendered in the Satellite user interface.
-Usage is tracked and itemized on invoices at the Bucket level. One practical consideration when choosing how to map constructs in your application to constructs on Storj DCS is that large numbers of buckets will increase the size and complexity of your invoices.
+Usage is tracked and itemized on invoices at the Bucket level. One practical consideration when choosing how to map constructs in your application to constructs on Storj is that large numbers of buckets will increase the size and complexity of your invoices.
From an access management perspective, there’s really no difference between using a bucket and using a top-level path within a bucket. The only differences are that bucket names are unencrypted and appear on invoices while top-level path names are encrypted and billing is aggregated at the bucket level.
@@ -84,7 +84,7 @@ With this structure, your application can manage the data for all of the tenants
An object key (or path) is a unique identifier for an object within a bucket. An object key is an arbitrary string of bytes. Object keys resemble file system paths by containing forward slashes at access control boundaries. Forward slashes (referred to as the path separator) separate path components. An example path might be `videos/carlsagan/gloriousdawn.mp4`, where the path components are `videos`, `carlsagan`, and `gloriousdawn.mp4`. It is possible to share just the encryption keys for objects that have a common object key path component prefix.
{% callout type="info" %}
-While many object storage platforms provide access management restrictions only at the bucket level, Storj DCS provides the tools to manage granular access at the path level.
+While many object storage platforms provide access management restrictions only at the bucket level, Storj provides the tools to manage granular access at the path level.
{% /callout %}
## Object (encrypted metadata)
@@ -93,11 +93,11 @@ An object is the main data type in our system. An object is referred to by an ob
## Access Grant
-Storj DCS uses hierarchically deterministic Access Grants as an access management layer for objects. An Access Grant is a security envelope that contains a satellite address, a restricted API Key, and a restricted path component prefix-based encryption key—everything an application needs to locate an object on the network, access that object, and decrypt it. The key benefit of this approach is that these Access Grants and any associated restrictions can be entirely managed client-side, without a central Access Control List or other server-side mechanism involved in the access management process. We call this delegated authorization.
+Storj uses hierarchically deterministic Access Grants as an access management layer for objects. An Access Grant is a security envelope that contains a satellite address, a restricted API Key, and a restricted path component prefix-based encryption key—everything an application needs to locate an object on the network, access that object, and decrypt it. The key benefit of this approach is that these Access Grants and any associated restrictions can be entirely managed client-side, without a central Access Control List or other server-side mechanism involved in the access management process. We call this delegated authorization.
-The most important thing to understand about Access Grants is, even though an Access Grant contains a serialized encryption key encapsulated in the Access Grant, that encryption key is NEVER passed to a Satellite. Storj DCS Uplink clients separate the API Key from the Access Grant and only pass the API Key to Satellites. That way, a Satellite can receive an access request, evaluate the validity of the API Key associated with that request, and respond with the metadata needed to retrieve the pieces of the object associated with that request without having any ability to decrypt the underlying data or metadata or have any information about the context of the user or application making the request.
+The most important thing to understand about Access Grants is, even though an Access Grant contains a serialized encryption key encapsulated in the Access Grant, that encryption key is NEVER passed to a Satellite. Storj Uplink clients separate the API Key from the Access Grant and only pass the API Key to Satellites. That way, a Satellite can receive an access request, evaluate the validity of the API Key associated with that request, and respond with the metadata needed to retrieve the pieces of the object associated with that request without having any ability to decrypt the underlying data or metadata or have any information about the context of the user or application making the request.
-The result is that the Storj DCS service allows you to create more private and secure applications. Below is a brief description of the three components within an Access Grant:
+The result is that the Storj service allows you to create more private and secure applications. Below is a brief description of the three components within an Access Grant:
### Satellite Address
@@ -119,7 +119,7 @@ Restrictions applied to an API Key within an Access Grant are hierarchically der
### Encryption Key
-All data stored on Storj DCS is encrypted. By using hierarchically-derived encryption keys, it becomes easy to share the ability to decrypt a single object or set of objects without sharing the private encryption passphrase or having to re-encrypt objects. When you create a Primary Access Grant, you provide an encryption passphrase. All Restricted Access Grants derived from that Primary Access Grant contain a path-based hierarchically derived serialized encryption key (or set of encryption keys, based on what has been shared).
+All data stored on Storj is encrypted. By using hierarchically-derived encryption keys, it becomes easy to share the ability to decrypt a single object or set of objects without sharing the private encryption passphrase or having to re-encrypt objects. When you create a Primary Access Grant, you provide an encryption passphrase. All Restricted Access Grants derived from that Primary Access Grant contain a path-based hierarchically derived serialized encryption key (or set of encryption keys, based on what has been shared).
If you're interested in more details, please read more about [](docId:uuhN7eyr1a8P3l_vzdnDk) at your leisure.
@@ -135,22 +135,22 @@ A Primary Access Grant can then be imported into an Uplink Client for use. The U
## Restricted Access Grants
-The Storj DCS service generates primary Access Grants, and restricted Access Grants are derived from a primary Access Grant or any other Access Grant via the Uplink Client. Parent-to-child, access may be further restricted, but not expanded. A restricted Access Grant can never have more access than its parent.
+The Storj service generates primary Access Grants, and restricted Access Grants are derived from a primary Access Grant or any other Access Grant via the Uplink Client. Parent-to-child, access may be further restricted, but not expanded. A restricted Access Grant can never have more access than its parent.
A primary Access Grant is created in the admin console of the Satellite. A primary Access Grant has all permissions to all buckets within a project and can be used to create a child Access Grant.
A restricted Access Grant may be created using the Satellite console or Uplink client. Restricted Access Grants are created in the context of creating access. Essentially, you don’t explicitly create a Restricted Access Grant, the Uplink client creates one when you generate an access, which handles both access management and encryption, both restricted to the scope of access being shared.
-The Storj DCS service also supports the revocation of Access Grants. Note that revoking an Access Grant adds that Access Grant to a revocation list and invalidates the Access Grant and any child Access Grant derived from the Access Grant that has been revoked. Revoking a primary access grant can be done in the UI, but currently revoking a restricted access grant can only happen via the Uplink CLI.
+The Storj service also supports the revocation of Access Grants. Note that revoking an Access Grant adds that Access Grant to a revocation list and invalidates the Access Grant and any child Access Grant derived from the Access Grant that has been revoked. Revoking a primary access grant can be done in the UI, but currently revoking a restricted access grant can only happen via the Uplink CLI.
## Sharing Access with Restricted Access Grants
-Sharing access to objects stored on Storj DCS requires sending encryption and authorization information about that object from one client to another. The information is sent in a construct called a Restricted Access Grant. As noted above, an Access Grant is a security envelope that contains a satellite address, a restricted API Key, and a restricted path-based encryption key—everything an application needs to locate an object on the network, access that object, and decrypt it.
+Sharing access to objects stored on Storj requires sending encryption and authorization information about that object from one client to another. The information is sent in a construct called a Restricted Access Grant. As noted above, an Access Grant is a security envelope that contains a satellite address, a restricted API Key, and a restricted path-based encryption key—everything an application needs to locate an object on the network, access that object, and decrypt it.
An Access contains a bearer token that is generated client-side and transmitted client-to-client. When the Uplink client generates or uses an Access, only the API Key (the bearer token) from the Access is sent to a Satellite to retrieve an object. The encryption key is retained by the Client and used to decrypt objects, metadata, and paths client-side.
-To implement these constructs as easily as possible for developers, the Storj DCS developer tools abstract the complexity of encoding objects for access management and encryption/decryption. A simple share command encapsulates the satellite address for an object’s metadata, an encryption key, and an API Key into an Access in the format of an encoded string that can be easily imported into an Uplink client. Imported Accesses are managed client-side and may be leveraged in applications via the Uplink client library.
+To implement these constructs as easily as possible for developers, the Storj developer tools abstract the complexity of encoding objects for access management and encryption/decryption. A simple share command encapsulates the satellite address for an object’s metadata, an encryption key, and an API Key into an Access in the format of an encoded string that can be easily imported into an Uplink client. Imported Accesses are managed client-side and may be leveraged in applications via the Uplink client library.
-## Applying the Storj DCS Information Architecture
+## Applying the Storj Information Architecture
-Once you understand the basic building blocks of Storj DCS, it’s pretty easy to build some fairly sophisticated privacy and security controls into your application.
+Once you understand the basic building blocks of Storj, it’s pretty easy to build some fairly sophisticated privacy and security controls into your application.
diff --git a/app/learn/concepts/limits/page.md b/app/learn/concepts/limits/page.md
index 972529504..a34dbed42 100644
--- a/app/learn/concepts/limits/page.md
+++ b/app/learn/concepts/limits/page.md
@@ -12,7 +12,7 @@ metadata:
increases.
---
-Usage Limits allow us to ensure a consistent level of service for all customers. We have limits for usage established per Project on all Storj DCS Satellites. All limits are set to default values as follows:
+Usage Limits allow us to ensure a consistent level of service for all customers. We have limits for usage established per Project on all Storj Satellites. All limits are set to default values as follows:
## PRO Account (Paid Tier)
@@ -60,11 +60,11 @@ Note that you could avoid having to wait for a manual project limit increase to
- 10,000 Segments
-If you would like to increase your limits to higher values and your only payment method is STORJ token, you may[ contact our support team through the Storj DCS support portal](https://supportdcs.storj.io/hc/en-us/requests/new?ticket_form_id=360000683212).
+If you would like to increase your limits to higher values and your only payment method is STORJ token, you may[ contact our support team through the Storj support portal](https://supportdcs.storj.io/hc/en-us/requests/new?ticket_form_id=360000683212).
## Rationales behind limits
-Storage and bandwidth limits are imposed by most cloud infrastructure providers as a normal part of capacity planning and to ensure achievement of SLAs. In distributed and decentralized storage systems they are equally important, if not more so. Just like any provider, the aggregate amount of available storage and bandwidth must be shared across all users. With a distributed and decentralized storage system like Storj DCS, the storage and bandwidth are provided by a network of third parties running storage node software. One of the key aspects to success is the balance of supply and demand. If there are too many users over-utilizing available resources, the user experience will be poor.
+Storage and bandwidth limits are imposed by most cloud infrastructure providers as a normal part of capacity planning and to ensure achievement of SLAs. In distributed and decentralized storage systems they are equally important, if not more so. Just like any provider, the aggregate amount of available storage and bandwidth must be shared across all users. With a distributed and decentralized storage system like Storj, the storage and bandwidth are provided by a network of third parties running storage node software. One of the key aspects to success is the balance of supply and demand. If there are too many users over-utilizing available resources, the user experience will be poor.
If there are too many storage nodes, there won’t be enough use to provide a meaningful ROI for Storage Node Operators. This can lead to storage node churn, increasing load on the network, and potentially impacting durability. Usage limits are one of the tools that maintain the balance.
@@ -76,6 +76,6 @@ In addition, we limit the number of Projects per Developer Account to minimize c
We have also set the default limit for the number of segments to a level that is healthy for the network. Note that increasing the Segment Project Limit may incur additional fees. Read more about [](docId:A4kUGYhfgGbVhlQ2ZHXVS).
-Customers can request a limit increase when needed by filling out the [limit increase request form](https://supportdcs.storj.io/hc/en-us/requests/new?ticket_form_id=360000683212) on our Storj DCS support portal if their only payment method on file is STORJ token.
+Customers can request a limit increase when needed by filling out the [limit increase request form](https://supportdcs.storj.io/hc/en-us/requests/new?ticket_form_id=360000683212) on our Storj support portal if their only payment method on file is STORJ token.
An automatic limit increase to Pro Account can be accomplished by adding a credit card as payment method. Please only make such requests if your use case really requires more than the current default limits. Requests will be evaluated taking into account the intended use case and availability on the network.
diff --git a/app/learn/concepts/linksharing-service/page.md b/app/learn/concepts/linksharing-service/page.md
index 39f893da3..f357f01c7 100644
--- a/app/learn/concepts/linksharing-service/page.md
+++ b/app/learn/concepts/linksharing-service/page.md
@@ -16,7 +16,7 @@ metadata:
The Linksharing service provides an easy way to share an object via a web browser. Linkshare links may be shared with the following features:
-- **Storj DCS Linkshare web page** - displays a preview of the shared object, including a streaming player for multimedia files along with a map displaying the geolocation of the storage nodes storing the encrypted and erasure coded pieces of the object
+- **Storj Linkshare web page** - displays a preview of the shared object, including a streaming player for multimedia files along with a map displaying the geolocation of the storage nodes storing the encrypted and erasure coded pieces of the object
- **Custom Domains** - Instead of using the default URL provided by linksharing, users can access their content using a custom domain: [](docId:RI4zz1sLvVEZ4ZcZbuT7l)
@@ -50,7 +50,7 @@ The [](docId:4oDAezF-FcfPr0WPl7knd) are included in that tutorial.
## Linkshare via CLI (Advanced)
-If you prefer a command line interface (CLI) or wish to programmatically integrate to Storj DCS we have our [uplink CLI](docId:tBnCSrmR1jbOewG38fIr4) in addition to our [](docId:2x_b4StTLjm2WoHEPx2Cm). You can also use a [](docId:GkgE6Egi02wRZtyryFyPz).
+If you prefer a command line interface (CLI) or wish to programmatically integrate to Storj we have our [uplink CLI](docId:tBnCSrmR1jbOewG38fIr4) in addition to our [](docId:2x_b4StTLjm2WoHEPx2Cm). You can also use a [](docId:GkgE6Egi02wRZtyryFyPz).
## Regions of availability
diff --git a/app/learn/concepts/solution-architectures/common-use-cases/page.md b/app/learn/concepts/solution-architectures/common-use-cases/page.md
index 46d5c06dc..5f11f8e02 100644
--- a/app/learn/concepts/solution-architectures/common-use-cases/page.md
+++ b/app/learn/concepts/solution-architectures/common-use-cases/page.md
@@ -15,7 +15,7 @@ metadata:
Object storage is ideal for files that are written once and read many times (WORM - Write Once, Read Many data). Object storage has formed the backbone of many different applications and use cases. Distributed and decentralized object storage is optimized for larger files, especially where those files are accessed regularly from geographically diverse locations.
-Object storage, in general, has a wide range of use cases. The use cases that are the best fit for Storj DCS are outlined below. If you don't see your use case listed, don't worry - this will just give you a sense of how Storj DCS is meant to be used.
+Object storage, in general, has a wide range of use cases. The use cases that are the best fit for Storj are outlined below. If you don't see your use case listed, don't worry - this will just give you a sense of how Storj is meant to be used.
## Common Use Cases
diff --git a/app/learn/tutorials/quickstart-uplink-cli/uploading-your-first-object/page.md b/app/learn/tutorials/quickstart-uplink-cli/uploading-your-first-object/page.md
index 1ba679c1b..0f3b0f91a 100644
--- a/app/learn/tutorials/quickstart-uplink-cli/uploading-your-first-object/page.md
+++ b/app/learn/tutorials/quickstart-uplink-cli/uploading-your-first-object/page.md
@@ -7,10 +7,10 @@ redirects:
weight: 0
---
-Install and configure the CLI and follow the steps below to upload your first object to Storj DCS.
+Install and configure the CLI and follow the steps below to upload your first object to Storj.
{% callout type="success" %}
-Every time you upload a file, the Storj DCS CLI will do all the heavy lifting - encrypt the data using [](docId:Pksf8d0TCLY2tBgXeT18d) (including path and metadata), break large files into 64MB Segments (or for smaller files into a single segment), then erasure code the segments, breaking each segment into 80 pieces, then distributing those pieces over our network of thousands of independently operated storage nodes. All of that happens in the background with a simple `cp` command.
+Every time you upload a file, the Storj CLI will do all the heavy lifting - encrypt the data using [](docId:Pksf8d0TCLY2tBgXeT18d) (including path and metadata), break large files into 64MB Segments (or for smaller files into a single segment), then erasure code the segments, breaking each segment into 80 pieces, then distributing those pieces over our network of thousands of independently operated storage nodes. All of that happens in the background with a simple `cp` command.
{% /callout %}
- [](docId:b4-QgUOxVHDHSIWpAf3hG)
diff --git a/app/node/faq/migrate-my-node/how-to-migrate-the-windows-gui-node-from-a-one-physical-location-to-other/page.md b/app/node/faq/migrate-my-node/how-to-migrate-the-windows-gui-node-from-a-one-physical-location-to-other/page.md
index ba3514332..a261a7f82 100644
--- a/app/node/faq/migrate-my-node/how-to-migrate-the-windows-gui-node-from-a-one-physical-location-to-other/page.md
+++ b/app/node/faq/migrate-my-node/how-to-migrate-the-windows-gui-node-from-a-one-physical-location-to-other/page.md
@@ -64,7 +64,7 @@ The network-attached storage location could work, but it is neither supported no
There are plenty of options how to transfer the identity and data to the remote location, here are some examples:
-- [Storj DCS](https://www.storj.io/)
+- [Storj](https://www.storj.io/)
- ftp service
diff --git a/app/node/get-started/setup/page.md b/app/node/get-started/setup/page.md
index d3d0cd450..23694c4ec 100644
--- a/app/node/get-started/setup/page.md
+++ b/app/node/get-started/setup/page.md
@@ -41,4 +41,4 @@ Install the software that works best for you.
## Recommended step: [](docId:DVKqtMtnBdZ99gFRWCojP) {% anchor=false %}
-Understand how Node Operators are compensated for the resources used by Storj DCS Satellites every month.
+Understand how Node Operators are compensated for the resources used by Storj Satellites every month.
diff --git a/app/support/account-management-billing/closing-an-account/page.md b/app/support/account-management-billing/closing-an-account/page.md
index e473a31d3..81f79de72 100644
--- a/app/support/account-management-billing/closing-an-account/page.md
+++ b/app/support/account-management-billing/closing-an-account/page.md
@@ -11,11 +11,11 @@ metadata:
account.
---
-We want all of our users to receive value when they choose the Storj DCS Platform for their storage needs, but it’s possible that a user may no longer need Storj DCS services. If a user wants to stop using an account and permanently delete the account, the user may submit a request for this only after following the steps outlined below to eliminate platform usage.
+We want all of our users to receive value when they choose the Storj Platform for their storage needs, but it’s possible that a user may no longer need Storj services. If a user wants to stop using an account and permanently delete the account, the user may submit a request for this only after following the steps outlined below to eliminate platform usage.
The process to eliminate platform usage starts with deleting all data from the platform, including all objects and buckets. Next, all Access Grants should be deleted. Once this is done, the user should submit a support ticket to remove all payment methods and delete the account.
-Note that in order to verify the deletion request is legitimate, the user will need to confirm they control the email address used for the account in question. Therefore, the user should file their support ticket while signed in to their [Storj help desk](https://supportdcs.storj.io/hc/en-us) account. If the user does not yet have a help desk account, they should sign up first before filing their account deletion request. Support agents will be happy to remove the help desk account once the Storj DCS account deletion has been completed.The account deletion request ticket should specify the following:
+Note that in order to verify the deletion request is legitimate, the user will need to confirm they control the email address used for the account in question. Therefore, the user should file their support ticket while signed in to their [Storj help desk](https://supportdcs.storj.io/hc/en-us) account. If the user does not yet have a help desk account, they should sign up first before filing their account deletion request. Support agents will be happy to remove the help desk account once the Storj account deletion has been completed.The account deletion request ticket should specify the following:
1. State that all data has been deleted (Buckets, Objects)
diff --git a/app/support/account-management-billing/creating-your-account/page.md b/app/support/account-management-billing/creating-your-account/page.md
index a554373ca..068311a1b 100644
--- a/app/support/account-management-billing/creating-your-account/page.md
+++ b/app/support/account-management-billing/creating-your-account/page.md
@@ -13,10 +13,10 @@ metadata:
Choose a Satellite from one of the available metadata regions and register for a developer account.
-The first step in creating your developer account on Storj DCS is to select a Satellite. A Satellite is a set of hosted services that is responsible for a range of functions on the network, including the node discovery system, node address information caching, per-object metadata storage, storage node reputation management, billing data aggregation, storage node payment, data audit and repair, as well as user account and authorization management.
+The first step in creating your developer account on Storj is to select a Satellite. A Satellite is a set of hosted services that is responsible for a range of functions on the network, including the node discovery system, node address information caching, per-object metadata storage, storage node reputation management, billing data aggregation, storage node payment, data audit and repair, as well as user account and authorization management.
{% callout type="info" %}
-When selecting the Satellite for your project, you'll want to choose the geographic region where the majority of the end users of your service who will be interacting with the objects on Storj DCS will be located.
+When selecting the Satellite for your project, you'll want to choose the geographic region where the majority of the end users of your service who will be interacting with the objects on Storj will be located.
Learn more about [](docId:v0b3GtAU4dDT_1qibwCxc) under Concepts.
{% /callout %}
@@ -33,7 +33,7 @@ Choose your account type - Personal if you're an individual with a smaller proje
-Or Professional if you are part of a business interested in leveraging Storj DCS in an application or service
+Or Professional if you are part of a business interested in leveraging Storj in an application or service
diff --git a/app/support/account-management-billing/data-retention-policy/page.md b/app/support/account-management-billing/data-retention-policy/page.md
index 97febda44..c32fe20b0 100644
--- a/app/support/account-management-billing/data-retention-policy/page.md
+++ b/app/support/account-management-billing/data-retention-policy/page.md
@@ -10,4 +10,4 @@ metadata:
payment and usage limits.
---
-All unpaid balances must be paid via a valid payment method in a billing cycle. Note that if no valid payment method remains on an account, usage limits may be reduced to zero. If all credit cards expire or are invalid, or the STORJ token balance is exhausted and no new payment method is added on a project, after a reasonable time and opportunity to add a payment method, we reserve the right to reclaim the available resources (the storage space and bandwidth made available by Storage Node Operators to the Storj network) and delete the data from Storj DCS if a valid payment method is not added and any unpaid fees are not paid.
+All unpaid balances must be paid via a valid payment method in a billing cycle. Note that if no valid payment method remains on an account, usage limits may be reduced to zero. If all credit cards expire or are invalid, or the STORJ token balance is exhausted and no new payment method is added on a project, after a reasonable time and opportunity to add a payment method, we reserve the right to reclaim the available resources (the storage space and bandwidth made available by Storage Node Operators to the Storj network) and delete the data from Storj if a valid payment method is not added and any unpaid fees are not paid.
diff --git a/app/support/account-management-billing/payment-methods/deleting-a-payment-method/page.md b/app/support/account-management-billing/payment-methods/deleting-a-payment-method/page.md
index 760dd5893..85390b1a8 100644
--- a/app/support/account-management-billing/payment-methods/deleting-a-payment-method/page.md
+++ b/app/support/account-management-billing/payment-methods/deleting-a-payment-method/page.md
@@ -11,7 +11,7 @@ metadata:
Access Grants.
---
-To use the Storj DCS Paid Tier, a user must have a valid payment method on their account. Users may delete payment methods:
+To use the Storj Paid Tier, a user must have a valid payment method on their account. Users may delete payment methods:
- when substituting for another valid payment method; or
diff --git a/app/support/account-management-billing/payment-methods/page.md b/app/support/account-management-billing/payment-methods/page.md
index 989fe1b95..d7d7d6d6a 100644
--- a/app/support/account-management-billing/payment-methods/page.md
+++ b/app/support/account-management-billing/payment-methods/page.md
@@ -11,7 +11,7 @@ metadata:
token for payments.
---
-Storj DCS accepts the following two payment methods:
+Storj accepts the following two payment methods:
1. Credit Card
@@ -21,7 +21,7 @@ Storj DCS accepts the following two payment methods:
## How To Add A Payment Method
-Once you have created a user account and a project, registered users are required to add a payment method before storing data on Storj DCS. Payment methods are added from the [](docId:Hurx0SirlRp_O5aUzew7_) section of the user interface.
+Once you have created a user account and a project, registered users are required to add a payment method before storing data on Storj. Payment methods are added from the [](docId:Hurx0SirlRp_O5aUzew7_) section of the user interface.
Begin by selecting "Billiing" from the "My Account" dropdown menu at the left bottom corner of your dashboard.
@@ -49,7 +49,7 @@ You’ll be prompted to add your card information. Using a credit card is somewh
## Using STORJ Token
-In addition to credit cards, users may also pay for usage fees with STORJ token. Storj created the STORJ utility token as a medium of exchange on its decentralized cloud storage network. The STORJ utility token facilitates payments from people around the world for their use of the Storj DCS network to store their data, and Storj uses it to pay our community of Storage Node Operators that rent their unused hard drive capacity and bandwidth to the network.
+In addition to credit cards, users may also pay for usage fees with STORJ token. Storj created the STORJ utility token as a medium of exchange on its decentralized cloud storage network. The STORJ utility token facilitates payments from people around the world for their use of the Storj network to store their data, and Storj uses it to pay our community of Storage Node Operators that rent their unused hard drive capacity and bandwidth to the network.
Making payments with STORJ token is a different process than using a credit card. When using STORJ as your payment method, you commit to using a pre-payment model, which means you must first deposit X amount of STORJ tokens, which will be automatically converted to Y amount of $USD based on the spot price of the token at the time of the payment transaction.
@@ -68,7 +68,7 @@ We realize the STORJ token price can fluctuate, so our billing system is designe
To deposit STORJ tokens in an account, open a **_Payment Methods_** tab on the **Billing** page and click **Add STORJ tokens**, then use provided deposit address to deposit STORJ tokens via L1 (Ethereum).
{% callout type="info" %}
-Important: The deposit address generated for your account is a deposit-only address to prepay for usage on the Storj DCS Platform. Users are not able to remove or otherwise withdraw tokens from this address. Any request for a refund or return of an unused prepaid deposit must follow the support process [](docId:LX9pqXsAduR8LEaEiX_It).
+Important: The deposit address generated for your account is a deposit-only address to prepay for usage on the Storj Platform. Users are not able to remove or otherwise withdraw tokens from this address. Any request for a refund or return of an unused prepaid deposit must follow the support process [](docId:LX9pqXsAduR8LEaEiX_It).
{% /callout %}
If the STORJ token balance runs out, a user will receive a notification to the registered email on the account. However, if a new payment is not added within a reasonable amount of time, Storj reserves the right to reduce account usage limits to zero and/or reclaim the available storage and bandwidth resources and delete your data stored on the network pursuant to our data retention policy.
diff --git a/app/support/account-management-billing/payment-methods/promotional-credits/page.md b/app/support/account-management-billing/payment-methods/promotional-credits/page.md
index b6c42c166..70fef3d84 100644
--- a/app/support/account-management-billing/payment-methods/promotional-credits/page.md
+++ b/app/support/account-management-billing/payment-methods/promotional-credits/page.md
@@ -10,7 +10,7 @@ metadata:
Coupons work to promote adoption and usage of the platform.
---
-The Storj DCS Service includes incentive programs to encourage adoption and use of the platform. These incentives are operationalized as Promotional Credits and include Credits and Coupons.
+The Storj Service includes incentive programs to encourage adoption and use of the platform. These incentives are operationalized as Promotional Credits and include Credits and Coupons.
## Credits
diff --git a/app/support/account-management-billing/reporting-a-payment-problem/page.md b/app/support/account-management-billing/reporting-a-payment-problem/page.md
index af7c462a7..8bdbffedd 100644
--- a/app/support/account-management-billing/reporting-a-payment-problem/page.md
+++ b/app/support/account-management-billing/reporting-a-payment-problem/page.md
@@ -12,7 +12,7 @@ metadata:
We use best-in-class partners for payment processing (Stripe for credit card payments and CoinPayments for STORJ utility token transactions). Still, sometimes unanticipated issues can arise.
-If the issue is with a credit card payment, please start by submitting a support ticket through our [Storj DCS support portal](https://supportdcs.storj.io/hc/en-us/requests/new). We will attempt to resolve the issue prior to escalating with Stripe.
+If the issue is with a credit card payment, please start by submitting a support ticket through our [Storj support portal](https://supportdcs.storj.io/hc/en-us/requests/new). We will attempt to resolve the issue prior to escalating with Stripe.
If the issue is with a STORJ token transaction, you should first contact CoinPayments to confirm that your STORJ token transaction was received by CoinPayments. Once you have documentation from CoinPayments that the STORJ token transaction was processed, submit a support ticket through our [support portal](https://supportdcs.storj.io/hc/en-us/requests/new), including any documentation you have for the STORJ token transaction.
diff --git a/app/support/account-management-billing/requesting-a-refund/page.md b/app/support/account-management-billing/requesting-a-refund/page.md
index cf76b2295..f0ea230b9 100644
--- a/app/support/account-management-billing/requesting-a-refund/page.md
+++ b/app/support/account-management-billing/requesting-a-refund/page.md
@@ -11,4 +11,4 @@ metadata:
coupons, and credits have special refund conditions.
---
-We want all of our users to receive value when they choose the Storj DCS Platform for their storage needs. While we strive to provide world-class service it is possible that a customer may request a refund. Refunds will only be granted based on the circumstances set forth in the [Terms of Use](https://www.storj.io/terms-of-use) and [Terms of Service](https://www.storj.io/terms-of-service). Coupons and Credits are not refundable under any circumstances. Prepayments made via STORJ token transactions are nonrefundable unless an account is being closed.
+We want all of our users to receive value when they choose the Storj Platform for their storage needs. While we strive to provide world-class service it is possible that a customer may request a refund. Refunds will only be granted based on the circumstances set forth in the [Terms of Use](https://www.storj.io/terms-of-use) and [Terms of Service](https://www.storj.io/terms-of-service). Coupons and Credits are not refundable under any circumstances. Prepayments made via STORJ token transactions are nonrefundable unless an account is being closed.
diff --git a/app/support/dashboard/page.md b/app/support/dashboard/page.md
index d6a0f9dba..99663f65a 100644
--- a/app/support/dashboard/page.md
+++ b/app/support/dashboard/page.md
@@ -13,7 +13,7 @@ metadata:
elements, storage and bandwidth usage, project details, and bucket information.
---
-The landing page for the Storj DCS Satellite Admin Console is the Project Dashboard.
+The landing page for the Storj Satellite Admin Console is the Project Dashboard.
When you log into the Satellite Admin Console, you start on the Project Dashboard for your default Project. A Project is the basic unit for aggregating usage, calculating billing, invoicing fees, collecting payment, and handling access management. Users can create multiple Projects and projects are invoiced separately. Within a Project, usage is tracked at the Bucket level and aggregated for invoicing to the Project. Project names are not client-side encrypted so that they may be rendered in the Satellite user interface. There are two main drivers for creating multiple Projects: access management and billing.
@@ -27,7 +27,7 @@ On the Project Dashboard, there are a number of navigational elements and inform
1. **Projects management** - This element allows you to add Projects and switch between different Projects. There you also have a [](docId:jwCUqpDCk8CUuUqFuykFx) setting.
-2. **Project Navigation** - This element allows you to move between the different functions related to the project you have selected, to view the [](docId:k6QwBZM3hnzxkCuQxLOal), use the [](docId:4oDAezF-FcfPr0WPl7knd) to interact with data stored on Storj DCS through a web browser interface, create [](docId:XKib9SzjtEXTXWvdyYWX6) for native integrations and credentials for the [](docId:yYCzPT8HHcbEZZMvfoCFa), invite other developers to collaborate with you on your project in [](docId:0_4hY4Dp5ju9B8Ec6OTf3), see [](docId:Hurx0SirlRp_O5aUzew7_), and **Quick Start**, and manage your Account in **My Account**.
+2. **Project Navigation** - This element allows you to move between the different functions related to the project you have selected, to view the [](docId:k6QwBZM3hnzxkCuQxLOal), use the [](docId:4oDAezF-FcfPr0WPl7knd) to interact with data stored on Storj through a web browser interface, create [](docId:XKib9SzjtEXTXWvdyYWX6) for native integrations and credentials for the [](docId:yYCzPT8HHcbEZZMvfoCFa), invite other developers to collaborate with you on your project in [](docId:0_4hY4Dp5ju9B8Ec6OTf3), see [](docId:Hurx0SirlRp_O5aUzew7_), and **Quick Start**, and manage your Account in **My Account**.
3. **Storage Utilization** - This element displays the amount of storage utilized in the current month measured in GB hours; see [](docId:59T_2l7c1rvZVhI8p91VX).
@@ -37,7 +37,7 @@ On the Project Dashboard, there are a number of navigational elements and inform
6. **Bucket Information** - This element displays the names of [Buckets](docId:M-5oxBinC6J1D-qSNjKYS#bucket), the current month usage on Buckets and the number of objects in Buckets.
-Here are some links to help you get a better understanding of your Satellite Admin Console and Storj DCS constructs:
+Here are some links to help you get a better understanding of your Satellite Admin Console and Storj constructs:
{% callout type="info" %}
Learn more about [](docId:M-5oxBinC6J1D-qSNjKYS) under Concepts.
diff --git a/app/support/faqs/page.md b/app/support/faqs/page.md
index 97063cf6b..d8e2f4853 100644
--- a/app/support/faqs/page.md
+++ b/app/support/faqs/page.md
@@ -11,7 +11,7 @@ metadata:
and web hosting.
---
-Frequently asked questions about Storj DCS.
+Frequently asked questions about Storj.
## How do I navigate to the binary location?
@@ -66,13 +66,13 @@ e.g. `https://link.ap1.storjshare.io/s//my/path`
Please, think twice before using the described method above - it exposes your access grant. If you would like to use this method anyway, then make sure to limit the access as much as possible. Ideally - read-only with time duration and only to one or two objects/paths, not to the whole bucket!
{% /callout %}
-## Can I use Storj DCS for web hosting?
+## Can I use Storj for web hosting?
-The Storj DCS service allows you to **host static websites** along with multimedia streaming, large file distribution, and other web-delivered assets.
+The Storj service allows you to **host static websites** along with multimedia streaming, large file distribution, and other web-delivered assets.
-Since your webpages and assets are simply objects stored on the network and there is no server/database, Storj DCS does **not** support the hosting of **dynamic websites.** However, you can store all of your unchanging assets on Storj DCS and reference them from your dynamic site that is hosted on an external compute service of your choice.
+Since your webpages and assets are simply objects stored on the network and there is no server/database, Storj does **not** support the hosting of **dynamic websites.** However, you can store all of your unchanging assets on Storj and reference them from your dynamic site that is hosted on an external compute service of your choice.
-There are a few ways you can host your static site on Storj DCS. We recommend using the [](docId:GkgE6Egi02wRZtyryFyPz) but you may also use the [](docId:EGM8O-1xt2Az03eBWT8Rf) to host your site.
+There are a few ways you can host your static site on Storj. We recommend using the [](docId:GkgE6Egi02wRZtyryFyPz) but you may also use the [](docId:EGM8O-1xt2Az03eBWT8Rf) to host your site.
{% callout type="info" %}
**Static websites** serve files, including HTML, CSS, and Javascript files, exactly as they are stored on the server. All visitors will be served the same files.
@@ -88,13 +88,13 @@ You can learn more under Concepts for [](docId:CBMEVO2vA2lDZ_BVuZ9aP) and [](doc
## How are encryption keys managed?
-Storj DCS is a secure and private object storage service. While there are several different ways to interact with the service, including an S3 compatible gateway, CLI, developer library and tools like FileZilla, Rclone, Restic, Duplicati and more, you are responsible for keeping your encryption keys safe.
+Storj is a secure and private object storage service. While there are several different ways to interact with the service, including an S3 compatible gateway, CLI, developer library and tools like FileZilla, Rclone, Restic, Duplicati and more, you are responsible for keeping your encryption keys safe.
You can learn more under [](docId:yI4q9JDB3w01xEkFWA4_z) and [](docId:KEt1PX_a8sbmwGXI4IhT_)
## When do you create an Access Grant in Satellite UI and when do you use the CLI?
-You can generate an Access Grant in the [](docId:nGzxQBhV8nx5Pukj6O0zT), or you can use either our Go Library or the CLI. In general, you use the Satellite Admin Console web interface to create an Access Grant that you can then use to set up whatever client tool you are using. The CLI, client library or other client tool can then use that Access Grant to interact with the Storj DCS service, or create restricted Access Grants - child Access Grants of the parent created in the Satellite Admin Console.
+You can generate an Access Grant in the [](docId:nGzxQBhV8nx5Pukj6O0zT), or you can use either our Go Library or the CLI. In general, you use the Satellite Admin Console web interface to create an Access Grant that you can then use to set up whatever client tool you are using. The CLI, client library or other client tool can then use that Access Grant to interact with the Storj service, or create restricted Access Grants - child Access Grants of the parent created in the Satellite Admin Console.
If you want to learn more, check out the [](docId:M-5oxBinC6J1D-qSNjKYS) section or read all about [](docId:bNywu7-9KLjYfk5LBQABx).
@@ -103,7 +103,7 @@ If you want to learn more, check out the [](docId:M-5oxBinC6J1D-qSNjKYS) section
Access Grants created using the Satellite user interface my be deleted using the Remove button on the Access page. Check the box next to the Access Grant(s) you want to delete, then click the Remove Selected button and follow the prompts.
{% callout type="success" %}
-**Important:** If you delete an Access Grant from the Satellite user interface, that Access Grant will immediately cease to function, and all hierarchically derived child Access Grants will also cease to function. Any data uploaded with that Access Grant will persist on Storj DCS. If you didn't back up the encryption passphrase used with the Access Grant you are deleting, you will not be able to decrypt that data without that encryption passphrase, and it will be effectively unrecoverable.
+**Important:** If you delete an Access Grant from the Satellite user interface, that Access Grant will immediately cease to function, and all hierarchically derived child Access Grants will also cease to function. Any data uploaded with that Access Grant will persist on Storj. If you didn't back up the encryption passphrase used with the Access Grant you are deleting, you will not be able to decrypt that data without that encryption passphrase, and it will be effectively unrecoverable.
{% /callout %}
If you created a child Access Grant client-side, using the CLI, the client Go library, or any other client-side tool or implementation, you can't "delete" the access because, by design and for enhanced privacy and security, the Satellite is not aware of Access Grants created in a client. When presented with any Access Grant, the Satellite can only verify whether the Access Grant is valid for the resource being requested. For this reason, Access Grants that have been created client-side cannot be deleted, but must be revoked instead.
@@ -112,7 +112,7 @@ You can learn more under Concepts for [](docId:XKib9SzjtEXTXWvdyYWX6).
## How do I recover from having lost my encryption key associated with an access grant?
-Your encryption keys effectively are your data. If you've lost the encryption key associated with an Access Grant, but you still have the Access Grant, DO NOT DELETE OR REVOKE that Access Grant. An Access Grant will continue to work until revoked or deleted. An Access Grant contains a serialized API key, encryption key, and the Satellite that holds the metadata for an object, but what is serialized in the access grant is derived from the passphrase - the passphrase is not stored in the access grant directly. Of course, that encryption passphrase is not stored by any Storj DCS service.
+Your encryption keys effectively are your data. If you've lost the encryption key associated with an Access Grant, but you still have the Access Grant, DO NOT DELETE OR REVOKE that Access Grant. An Access Grant will continue to work until revoked or deleted. An Access Grant contains a serialized API key, encryption key, and the Satellite that holds the metadata for an object, but what is serialized in the access grant is derived from the passphrase - the passphrase is not stored in the access grant directly. Of course, that encryption passphrase is not stored by any Storj service.
The safest approach would be to download your data with the working Access Grant, then create a new Access Grant with a new encryption passphrase and re-upload the data. Be sure to save that encryption passphrase in a secure location! As long as you have the encryption passphrase, you can generate new Access Grants that will work with pre-existing data.
@@ -120,13 +120,13 @@ If you've lost the Access Grant and you don't have a backup of the encryption pa
## How can I revoke an Access Grant I shared with someone?
-Access Grants can be created either in a browser or with the CLI or library, they can be further restricted, client-side creating additional hierarchically derived Access grants. Since these restricted Access Grants are managed client-side through delegated authorization, no server has any registry that these Access Grants even exist. While this gives developers a powerful tool kit to create more private and secure applications, shared access also needs to be revoked. The Storj DCS service has an API for revoking Access Grants via a revocation list.
+Access Grants can be created either in a browser or with the CLI or library, they can be further restricted, client-side creating additional hierarchically derived Access grants. Since these restricted Access Grants are managed client-side through delegated authorization, no server has any registry that these Access Grants even exist. While this gives developers a powerful tool kit to create more private and secure applications, shared access also needs to be revoked. The Storj service has an API for revoking Access Grants via a revocation list.
You can learn more under Concepts for [](docId:k-qsdTq8rYcpbfhWIFLeR).
## What kind of restrictions can I put on an Access Grant?
-You can generate a restricted Access Grant from the Satellite user interface, using the CLI, or using the client Go Library. While the possibilities for access controls that can be encoded in a caveat are virtually unlimited, the specific caveats supported on Storj DCS are as follows:
+You can generate a restricted Access Grant from the Satellite user interface, using the CLI, or using the client Go Library. While the possibilities for access controls that can be encoded in a caveat are virtually unlimited, the specific caveats supported on Storj are as follows:
- **Specific operations:** Caveats can restrict whether an API Key can perform any of the following operations: Read, Write, Delete, List
@@ -140,7 +140,7 @@ For some sample Go code around access-restriction, check out: