Exposor - A Contactless Reconnaissance Tool with unified syntax
Getting started • Installation • Usage • Contribution • Future Work • Disclaimer • License
Exposor is a contactless reconnaissance tool focused on technology detection across Censys, Fofa, Shodan, and Zoomeye. With a unified syntax for multi-platform querying, It gives security researchers and professionals a clear view of exposed systems, enabling quick risk identification.
- Configure your API keys for supported feeds.
- Use exposor's query syntax to find technologies
- Retrive and analyze results accross multiple search engines in a single workflow.
- Contribute custom YAML files to extend detection capabilities.
- Easily configure API credentials and keep the intelligence files updated.
- Perform targeted searches by netblock, country code, or hostname.
- Execute queries across multiple feeds with a unified syntax.
- Extend intel capabilities by contributing new YAML files.
- Identify exposed systems and potential vulnerabilities using CPEs or CVEs.
These features make Exposor a powerful tool for cybersecurity professionals conducting non-intrusive active reconnaissance.
You have two options to install Exposor:
Intall via pip
#latest stable release
pip install exposorClone the repository
git clone https://github.com/abuyv/exposor.git
cd exposor
pip install -r requirements.txtNote
For the latest stable releases, visit the Releases page
To use Exposor, you must configure API keys for the feeds you want to search. At least one API key is required to enable searching on a feed.
You can add your API keys in two ways:
- Using
--initoption
Run exposor --init option to create a configuration file:
exposor --init shodan:api_key zoomeye:api_key censys:api_id:api_secret fofa:email:api_key- Using env variables
Set the API keys as environment variables using the following commands:
# Unix
export CENSYS_API_ID="your_censys_api_id"
export CENSYS_API_KEY="your_censys_api_secret"
export FOFA_EMAIL="your_fofa_email"
export FOFA_API_KEY="your_fofa_api_key"
export SHODAN_API_KEY="your_shodan_api_key"
export ZOOMEYE_API_KEY="your_zoomeye_api_key"
# Windows
$env:CENSYS_API_ID="your_censys_api_id"
$env:CENSYS_API_KEY="your_censys_api_secret"
$env:FOFA_EMAIL="your_fofa_email"
$env:FOFA_API_KEY="your_fofa_api_key"
$env:SHODAN_API_KEY="your_shodan_api_key"
$env:ZOOMEYE_API_KEY="your_zoomeye_api_key"
These keys will be automatically picked up by Exposor.
Important
At least one API key must be configured to perform searches on any feed.
If you need to update your keys, you can either re-export them or re-run the --init command
Run Exposor to detect specific technologies using predefined YAML files:
__
/__\__ __ _ __ ___ ___ ___ _ __
/_\ \ \/ /| '_ \ / _ \ / __| / _ \ | '__|
//__ > < | |_) || (_) |\__ \| (_) || |
\__/ /_/\_\| .__/ \___/ |___/ \___/ |_|
|_|
version: 1.0.0
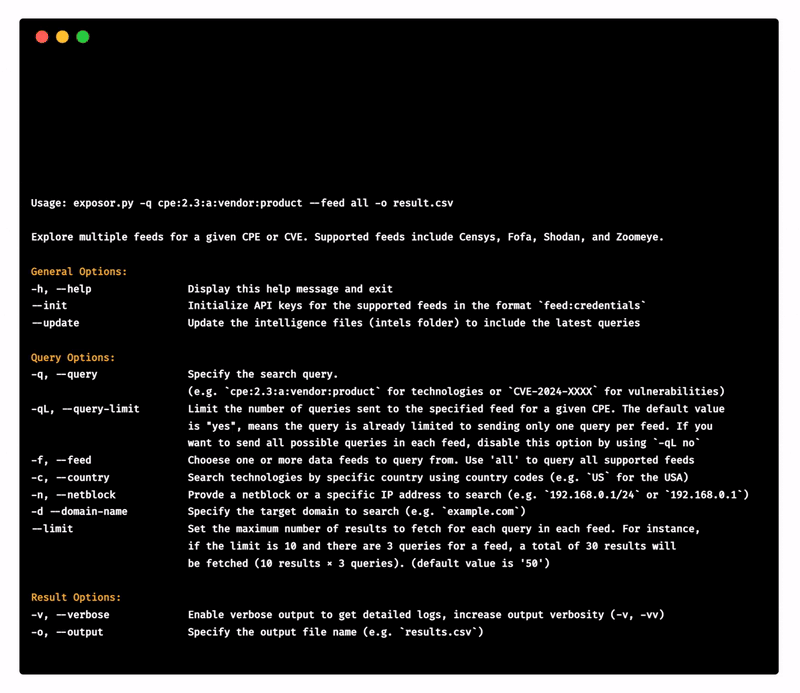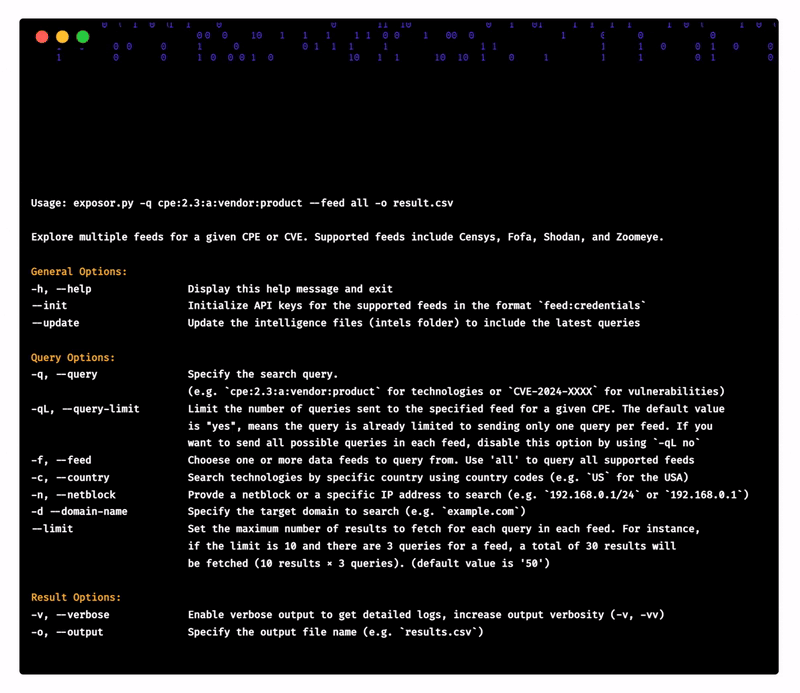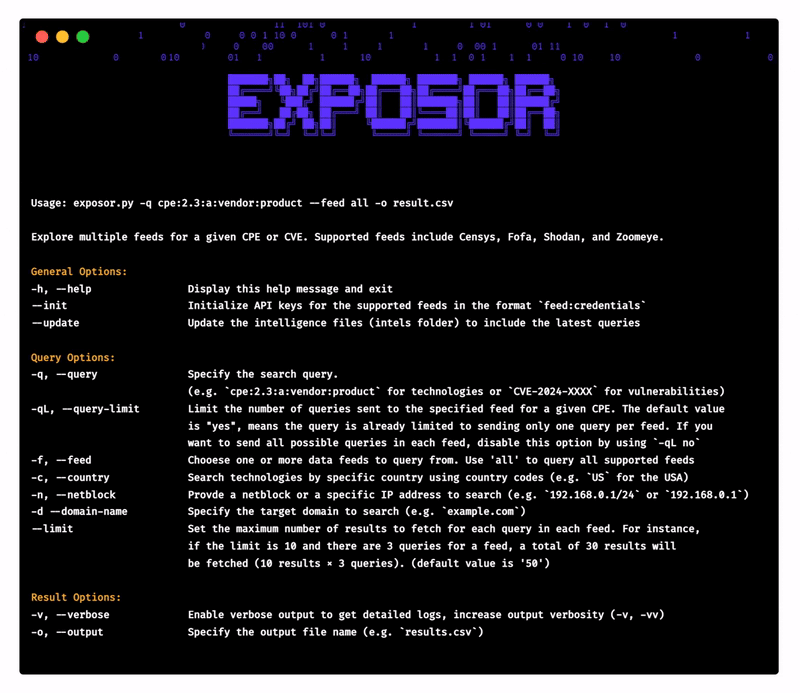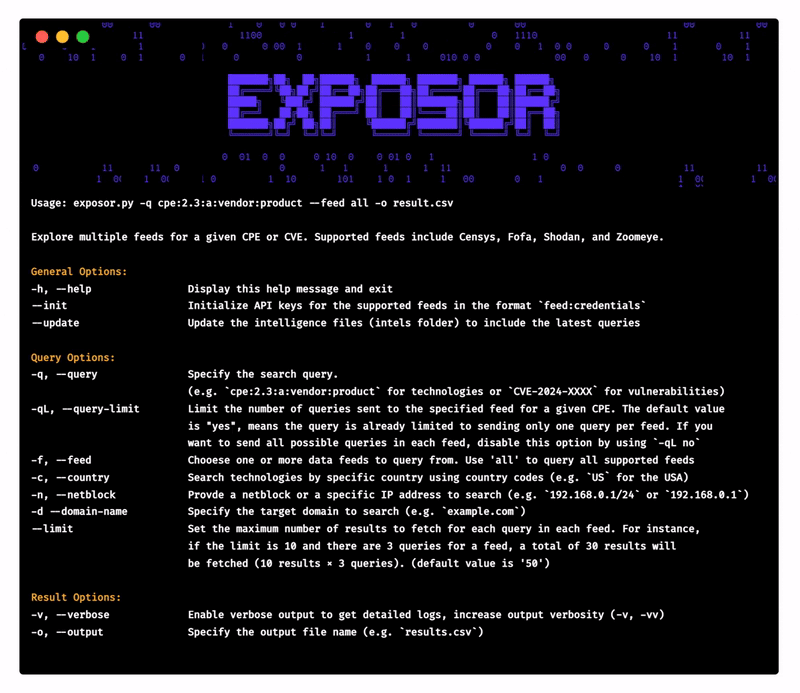
Usage: exposor.py -q cpe:2.3:a:vendor:product --feed all -o result.csv
Explore multiple feeds for a given CPE or CVE. Supported feeds include Censys, Fofa, Shodan, and Zoomeye.
General Options:
-h, --help Display this help message and exit
--init Initialize API keys for the supported feeds in the format `feed:credentials`
--update Update the intelligence files (intels folder) to include the latest queries
Query Options:
-q, --query Specify the search query.
(e.g. `cpe:2.3:a:vendor:product` for technologies or `CVE-2024-XXXX` for vulnerabilities)
-qL, --query-limit Limit the number of queries sent to the specified feed for a given CPE. The default value
is "yes", means the query is already limited to sending only one query per feed. If you
want to send all possible queries in each feed, disable this option by using `-qL no`
-f, --feed Chooese one or more data feeds to query from. Use 'all' to query all supported feeds
-c, --country Search technologies by specific country using country codes (e.g. `US` for the USA)
-n, --netblock Provde a netblock or a specific IP address to search (e.g. `192.168.0.1/24` or `192.168.0.1`)
-d --domain-name Specify the target domain to search (e.g. `example.com`)
--limit Set the maximum number of results to fetch for each query in each feed. For instance,
if the limit is 10 and there are 3 queries for a feed, a total of 30 results will
be fetched (10 results × 3 queries). (default value is '50')
Result Options:
-v, --verbose Enable verbose output to get detailed logs, increase output verbosity (-v, -vv)
-o, --output Specify the output file name (e.g. `results.csv`)
If you wish to contribute to the project and help expand the coverage of intels, follow the instructions below to add a new YAML file:
-
Please read Contributing Guidelines to understand how to propose changes.
-
technology_intels/: Contains YAML files for detecting specific technologies or platforms. Files are organized byvendor_name/product_name/vendor_product.yaml. -
vulnerability_intels/: Contains YAML files for tracking vulnerabilities (e.g., CVEs) generated using thevulners-api.pyscript.
exposor/
├── intels/ # Folder for intelligence YAML files
│ ├── technology_intels/ # Technology-specific YAML files
│ │ ├── vendor_name/ # Vendor name folder
│ │ │ ├── product_name/ # Product name folder
│ │ │ │ ├── vendor_product.yaml <––– Example technology YAML
│ └── vulnerability_intels/ # Vulnerability-specific YAML files
│ │ ├── vendor_product_cves.yaml <––– Example vulnerability YAML
└── ...
Integrate more feeds
Pending features
- Auto unifying queries across feeds
- Auto generation of vulnerability YAML files
- Supporting multiple API keys for a single feed
- Implementing custom query syntax
- Adding a logical OR operator for queries to save API credits and optimize usage.
Use Exposor responsibly and follow all regulations. You are fully responsible for your actions. If you misuse this tool or break the law, it’s entirely your own responsibility.
Exposor is developed by @abuyv and is MIT License
If you are here and found it useful, consider giving the repository a ⭐ to show your support.